تثبيت التطبيق
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
ملاحظة: This feature may not be available in some browsers.
أنت تستخدم أحد المتصفحات القديمة. قد لا يتم عرض هذا الموقع أو المواقع الأخرى بشكل صحيح.
يجب عليك ترقية متصفحك أو استخدام أحد المتصفحات البديلة.
يجب عليك ترقية متصفحك أو استخدام أحد المتصفحات البديلة.
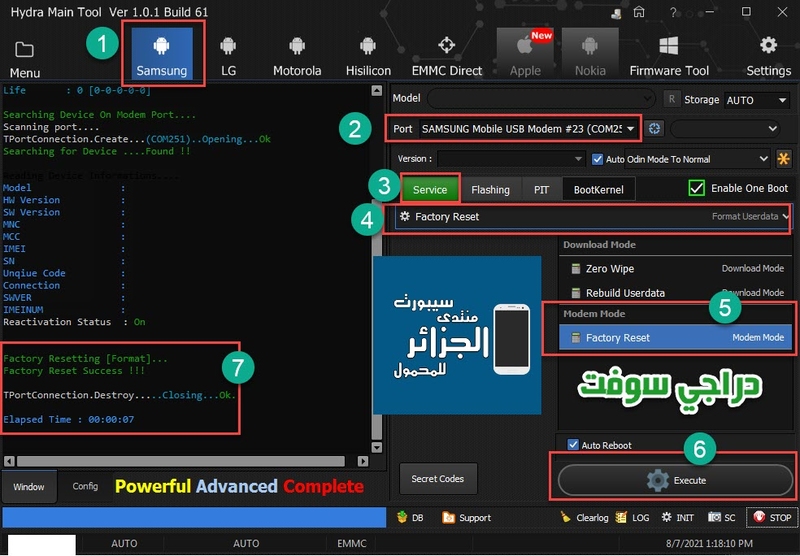
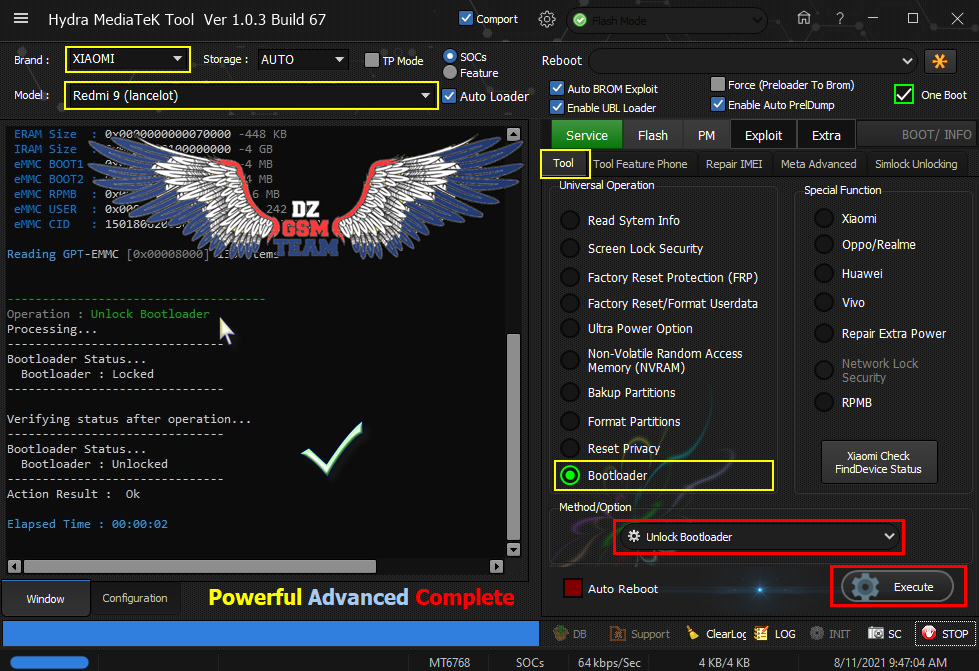
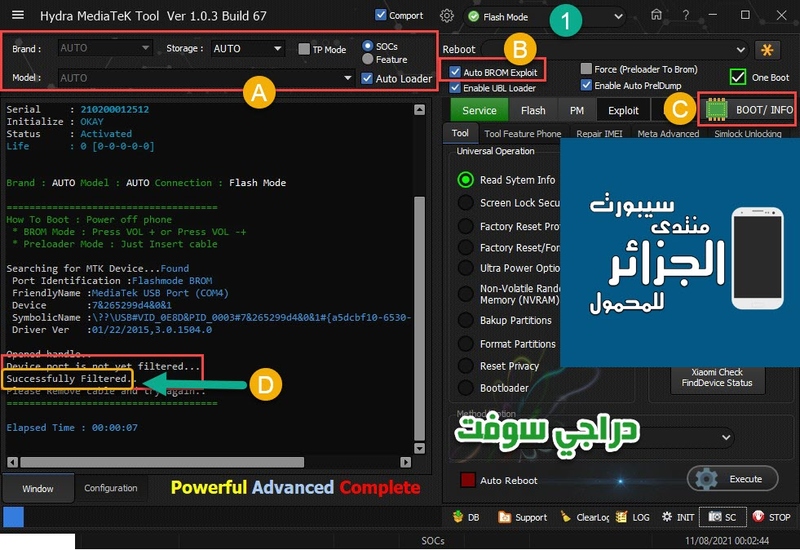
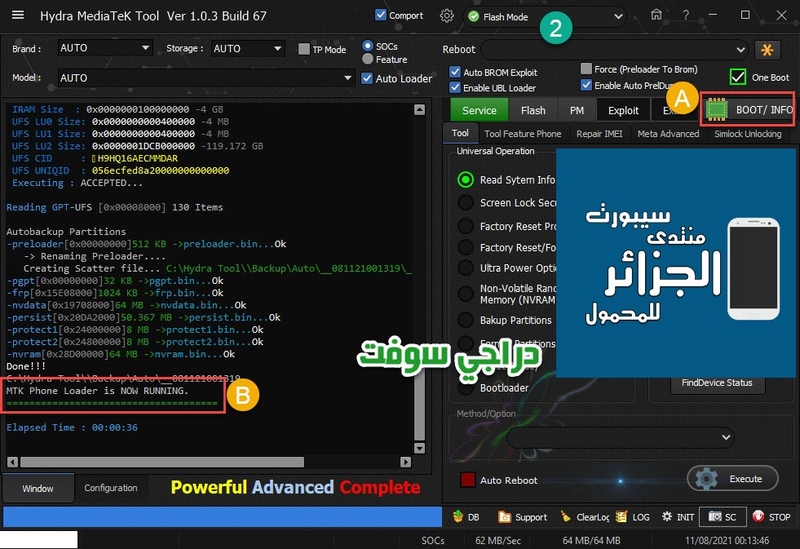
تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
- بادئ الموضوع DZ-Djamel-GSM
- تاريخ البدء
رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
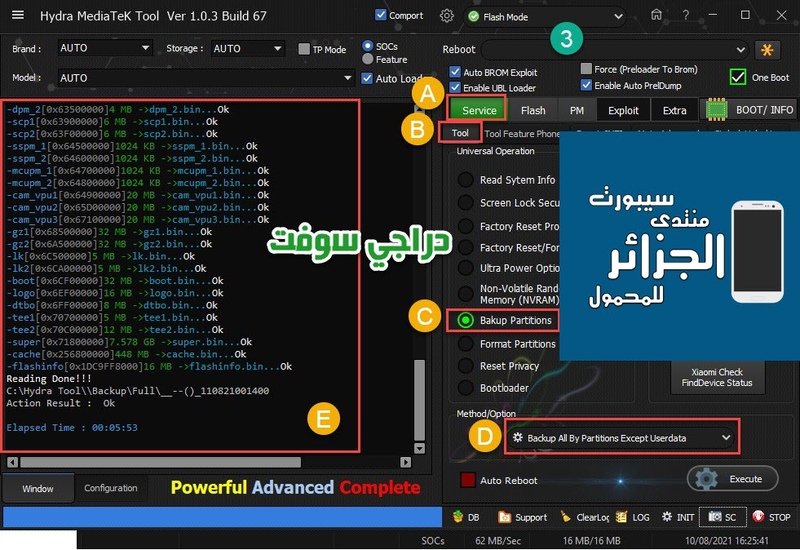
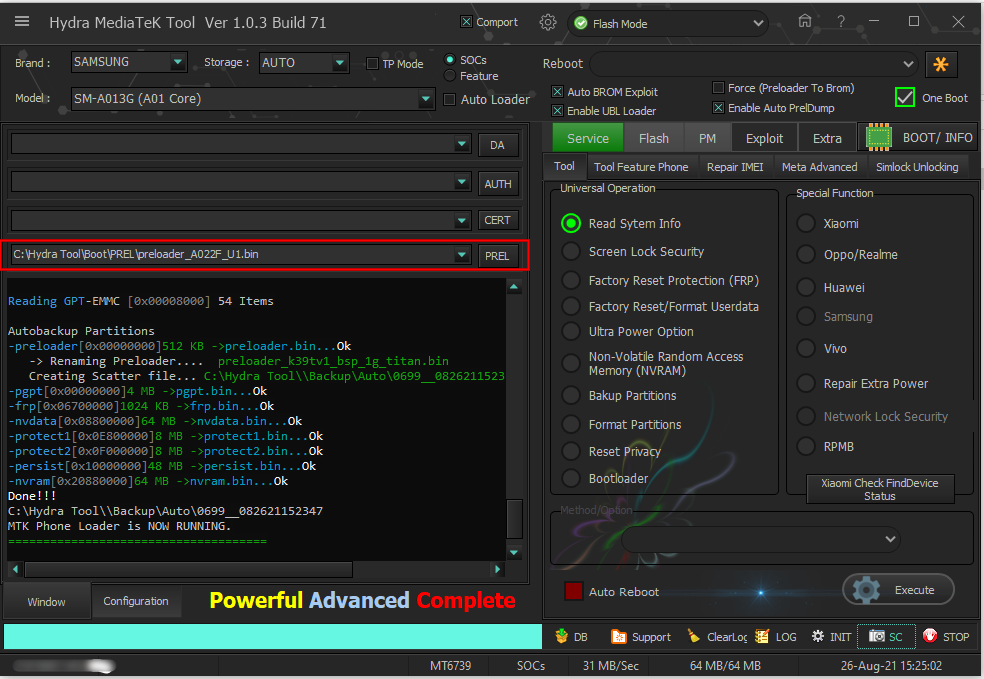
Oppo A5s (CPH1909) Formatting Userdata Flash Mode Done
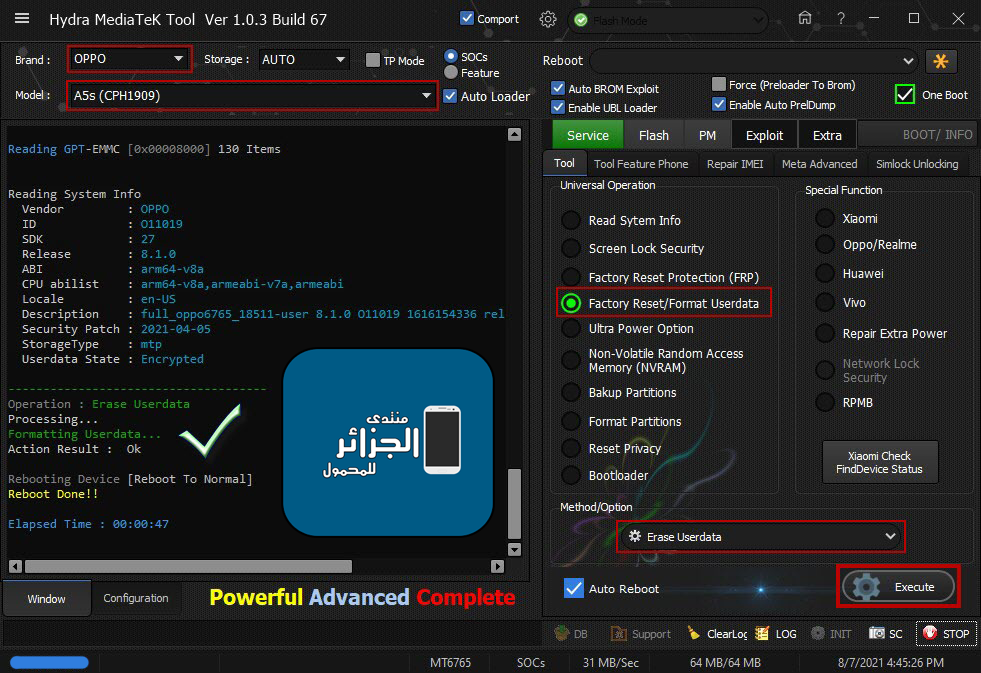
Oppo A5s (CPH1909) Formatting Userdata Flash Mode Done


كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1632 (COM61)
Device :6&12e3c9ed&0&2
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&2#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E5
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking...Ok
C:\Hydra Tool\Backup\Preloader_dump\prel.tmp
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : DEBAAE437782A99E5E0FA7B8C122BB90
Stage 1..[Size:216440]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Preloader Initialization...
Parsing prel.tmp
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 7C51C60E1F5F9CBE6A77AA0B9F3B0BEA
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 150100474436424D42011303D3A2C63F - GD6BMB
Executing : ACCEPTED...
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Vendor : OPPO
ID : O11019
SDK : 27
Release : 8.1.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_oppo6765_18511-user 8.1.0 O11019 1616154336 release-keys
Security Patch : 2021-04-05
StorageType : mtp
Userdata State : Encrypted
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader.... preloader_oppo6765_18511.bin
Creating Scatter file... C:\Hydra Tool\\Backup\Auto\0766__080721164507\MT6765_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x09E88000]1024 KB ->frp.bin...Ok
-nvdata[0x0BF88000]64 MB ->nvdata.bin...Ok
-protect1[0x11F88000]8 MB ->protect1.bin...Ok
-protect2[0x12788000]8.469 MB ->protect2.bin...Ok
-persist[0x13800000]48 MB ->persist.bin...Ok
-nvram[0x20000000]64 MB ->nvram.bin...Ok
Done!!!
C:\Hydra Tool\\Backup\Auto\0766__080721164507
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 7C51C60E1F5F9CBE6A77AA0B9F3B0BEA
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 150100474436424D42011303D3A2C63F - GD6BMB
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Vendor : OPPO
ID : O11019
SDK : 27
Release : 8.1.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_oppo6765_18511-user 8.1.0 O11019 1616154336 release-keys
Security Patch : 2021-04-05
StorageType : mtp
Userdata State : Encrypted
-------------------------------------
Operation : Erase Userdata
Processing...
Formatting Userdata...
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:47
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Condor TFX-708G Read Pattern Done
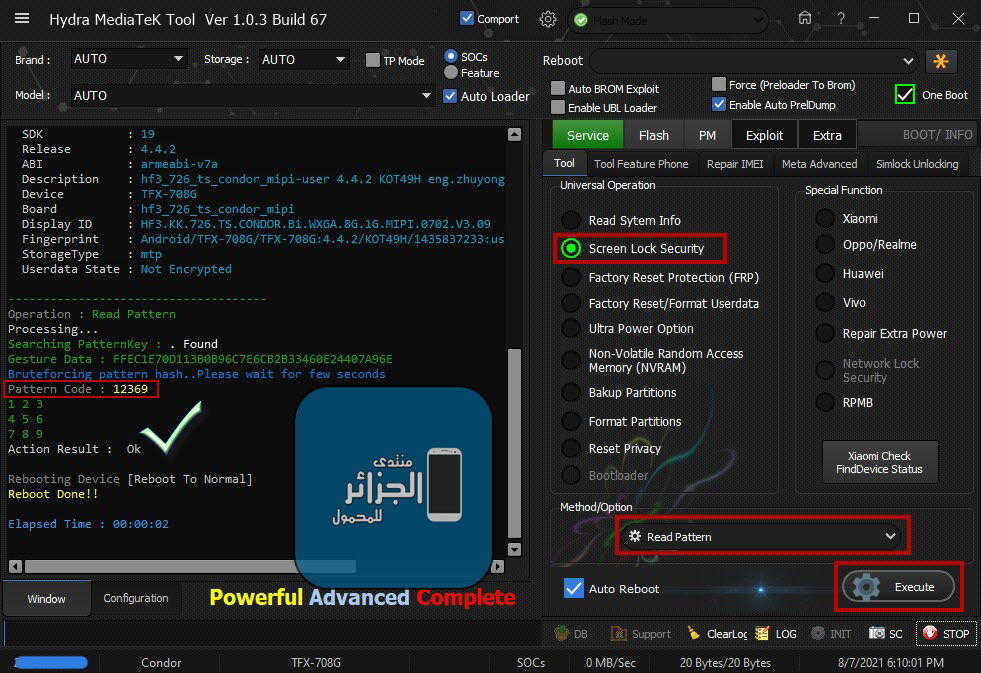
Condor TFX-708G Read Pattern Done

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1632 (Android) (COM62)
Device :6&12e3c9ed&0&2
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&2#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading System Info
Brand : [COLOR="#0000FF"]Condor[/COLOR]
Vendor : [COLOR="#0000FF"]SPA Condor Electronics[/COLOR]
Model : [COLOR="#0000FF"]TFX-708G[/COLOR]
ID : [COLOR="#0000FF"]KOT49H[/COLOR]
SDK : [COLOR="#0000FF"]19[/COLOR]
Release : [COLOR="#0000FF"]4.4.2[/COLOR]
ABI : [COLOR="#0000FF"]armeabi-v7a[/COLOR]
Description : [COLOR="#0000FF"]hf3_726_ts_condor_mipi-user 4.4.2 KOT49H eng.zhuyongjian.1435837233 release-keys[/COLOR]
Device : [COLOR="#0000FF"]TFX-708G[/COLOR]
Board : [COLOR="#0000FF"]hf3_726_ts_condor_mipi[/COLOR]
Display ID : [COLOR="#0000FF"]HF3.KK.726.TS.CONDOR.B1.WXGA.8G.1G.MIPI.0702.V3.09[/COLOR]
Fingerprint : [COLOR="#0000FF"]Android/TFX-708G/TFX-708G:4.4.2/KOT49H/1435837233:user/release-keys[/COLOR]
StorageType : m[COLOR="#0000FF"][/COLOR]tp
Userdata State : [COLOR="#0000FF"]Not Encrypted[/COLOR]
-------------------------------------
[COLOR="#808080"]Operation [/COLOR]: [COLOR="#008000"]Read Pattern[/COLOR]
Processing...
[COLOR="#008000"]Searching PatternKey[/COLOR] : . Found
[COLOR="#008000"]Gesture Data : FFEC1E70D113B0B96C7E6CB2B33460E24407A96E[/COLOR]
[COLOR="#0000CD"]Bruteforcing pattern hash..Please wait for few seconds[/COLOR]
[COLOR="#A9A9A9"]Pattern Code[/COLOR] : [COLOR="#FFD700"]12369[/COLOR]
[COLOR="#008000"]1 2 3
4 5 6
7 8 9
[/COLOR]Action Result : [COLOR="#808080"]Ok[/COLOR]
Rebooting Device [Reboot To Normal]
[COLOR="#FFD700"]Reboot Done!!
[/COLOR]
Elapsed Time : 00:00:02
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Lenovo A2016a40 (Lenovo B) ADB UltraPower
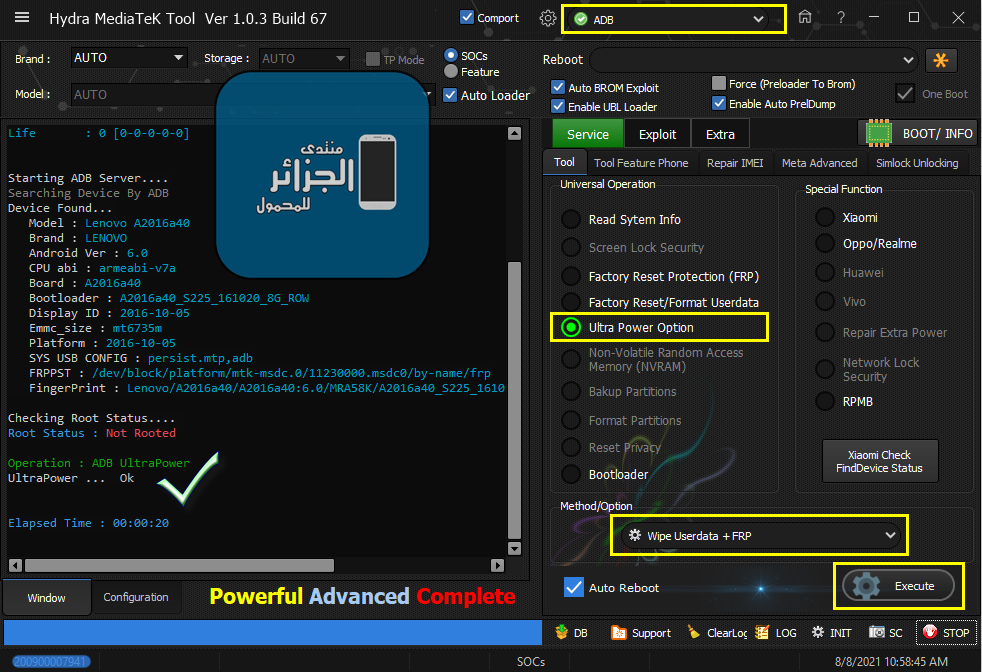
Lenovo A2016a40 (Lenovo B) ADB UltraPower

كود:
[B][FONT=Arial Black][SIZE=2]Starting ADB Server....
Searching Device By ADB
Device Found...
Model : [COLOR="#0000FF"]Lenovo A2016a40[/COLOR]
Brand : [COLOR="#0000FF"]LENOVO[/COLOR]
Android Ver : [COLOR="#0000FF"]6.0[/COLOR]
CPU abi : [COLOR="#0000FF"]armeabi-v7a[/COLOR]
Board : [COLOR="#0000FF"]A2016a40[/COLOR]
Bootloader : [COLOR="#0000FF"]A2016a40_S225_161020_8G_ROW[/COLOR]
Display ID : [COLOR="#0000FF"]2016-10-05[/COLOR]
Emmc_size : [COLOR="#0000FF"]mt6735m[/COLOR]
Platform : [COLOR="#0000FF"]2016-10-05[/COLOR]
SYS USB CONFIG : [COLOR="#0000FF"]persist.mtp,adb[/COLOR]
[COLOR="#0000FF"] FRPPST :[/COLOR] /dev/block/platform/mtk-msdc.0/11230000.msdc0/by-name/frp
FingerPrint : Lenovo/A2016a40/A2016a40:6.0/MRA58K/A2016a40_S225_1610202020.1610202020:user/release-keys
Checking Root Status....
[COLOR="#0000FF"]Root Status[/COLOR] : [COLOR="#0000FF"][COLOR="#FF0000"]Not Rooted[/COLOR][/COLOR]
[COLOR="#008000"]Operation : ADB UltraPower
[/COLOR]UltraPower ... Ok
Elapsed Time : 00:00:20
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
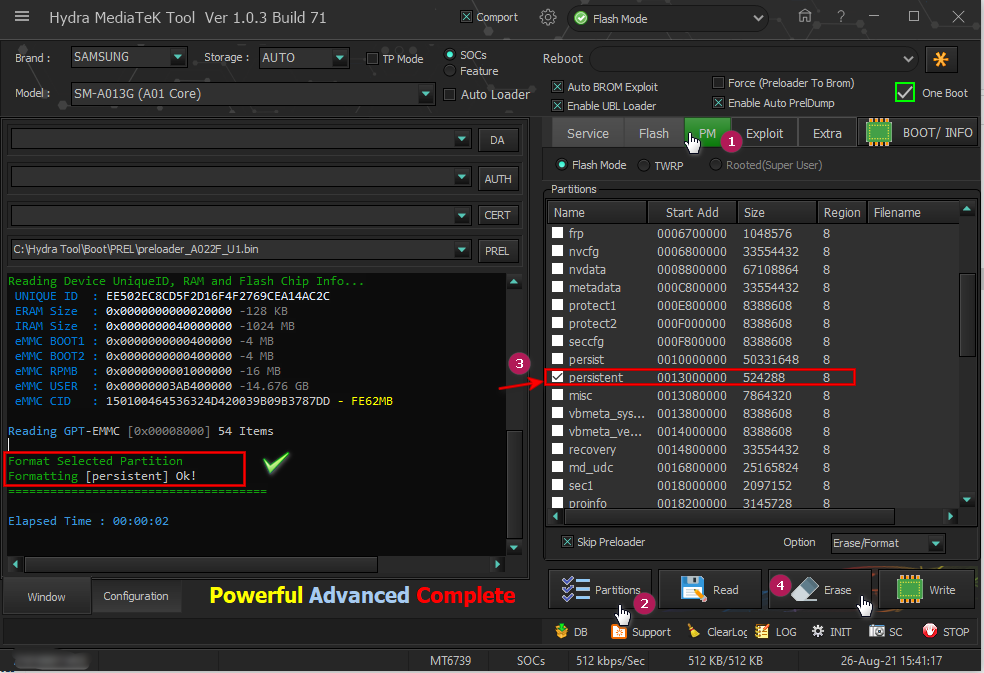
Samsung A10s (SM-A107F) FRP Remove Done
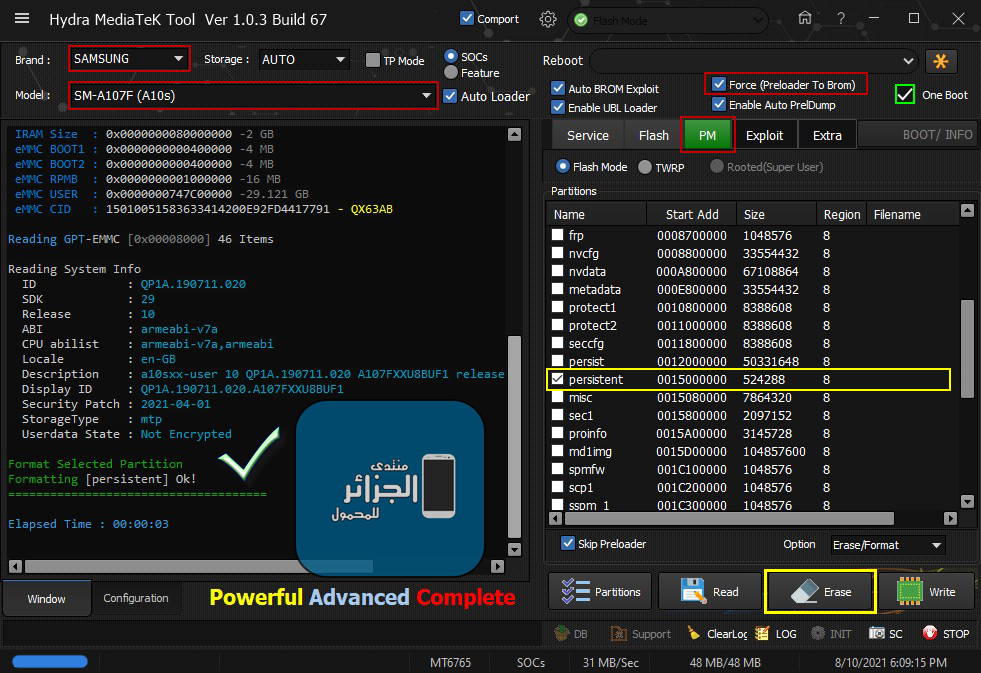
Samsung A10s (SM-A107F) FRP Remove Done


كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1632 (COM6)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : D2D5E1597EDF1BABF581641B10A42B37
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 15010051583633414200E92FD4417791 - QX63AB
Reading GPT-EMMC [0x00008000] 46 Items
Reading System Info
ID : [COLOR="#0000FF"]QP1A.190711.020[/COLOR]
SDK : [COLOR="#0000FF"]29[/COLOR]
Release : [COLOR="#0000FF"]10[/COLOR]
ABI : [COLOR="#0000FF"]armeabi-v7a[/COLOR]
CPU abilist : [COLOR="#0000FF"]armeabi-v7a,armeabi[/COLOR]
Locale : [COLOR="#0000FF"]en-GB[/COLOR]
Description : [COLOR="#0000FF"]a10sxx-user 10 QP1A.190711.020 A107FXXU8BUF1 release-keys[/COLOR]
Display ID : [COLOR="#0000FF"]QP1A.190711.020.A107FXXU8BUF1[/COLOR]
Security Patch : [COLOR="#0000FF"]2021-04-01[/COLOR]
StorageType : [COLOR="#0000FF"]mtp[/COLOR]
Userdata State :[COLOR="#0000FF"] Not Encrypted[/COLOR]
[COLOR="#008000"]Format Selected Partition[/COLOR]
[COLOR="#008000"]Formatting [/COLOR][persistent] Ok!
=====================================
[COLOR="#0000FF"]Elapsed Time : 00:00:03
[/COLOR][/SIZE][/FONT][/B]
رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
OPPO A1K (CPH1923) Erase Userdata Done
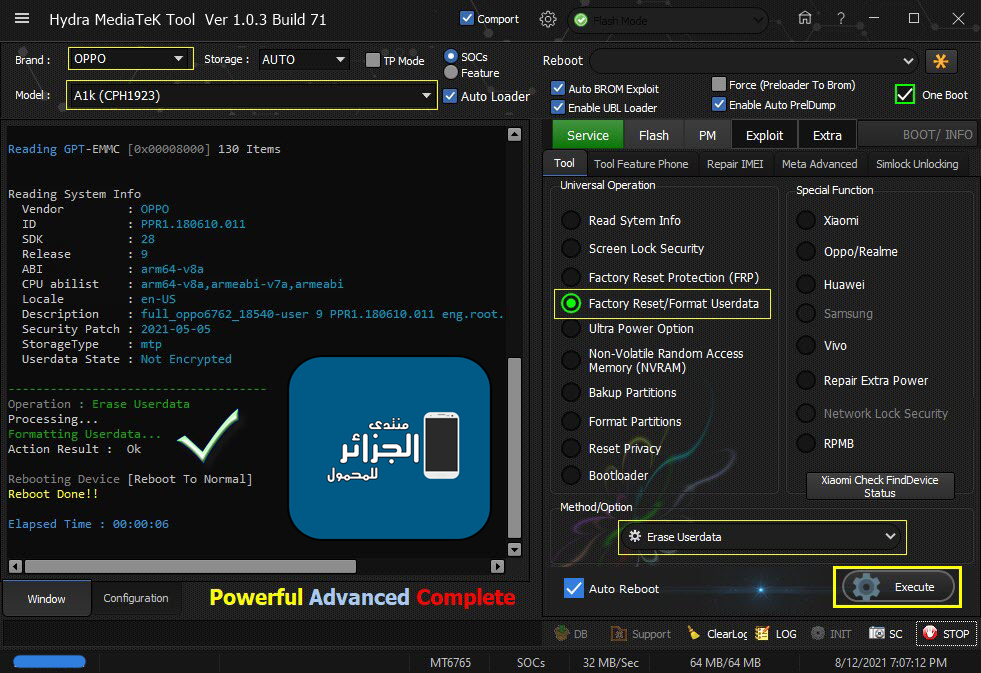
OPPO A1K (CPH1923) Erase Userdata Done

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1632 (COM6)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : FBF4DB2221D8C1AA6E1A727B9ED28752
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 150100514436334D42034B9B0616963D - QD63MB
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Vendor : OPPO
ID : PPR1.180610.011
SDK : 28
Release : 9
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_oppo6762_18540-user 9 PPR1.180610.011 eng.root.20210506.165532 release-keys
Security Patch : 2021-05-05
StorageType : mtp
Userdata State : Not Encrypted
-------------------------------------
Operation : Erase Userdata
Processing...
Formatting Userdata...
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:06
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
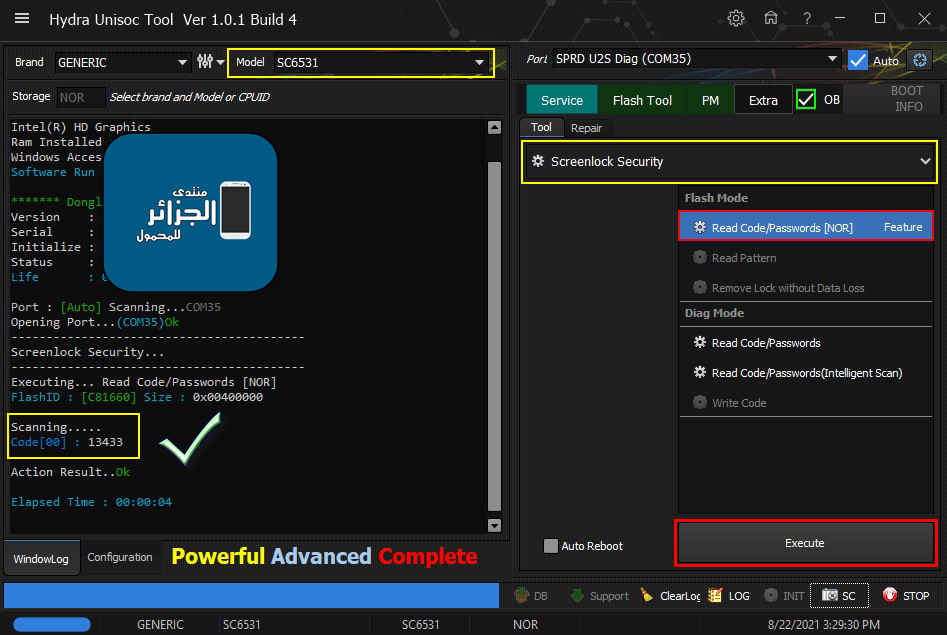
Condor Griffe T6 (SP631) Removing FRP
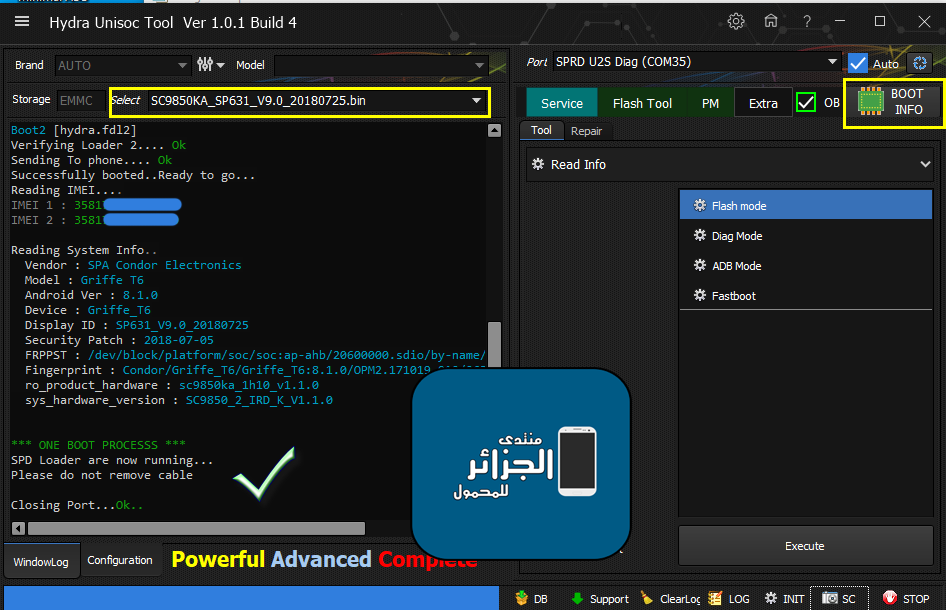
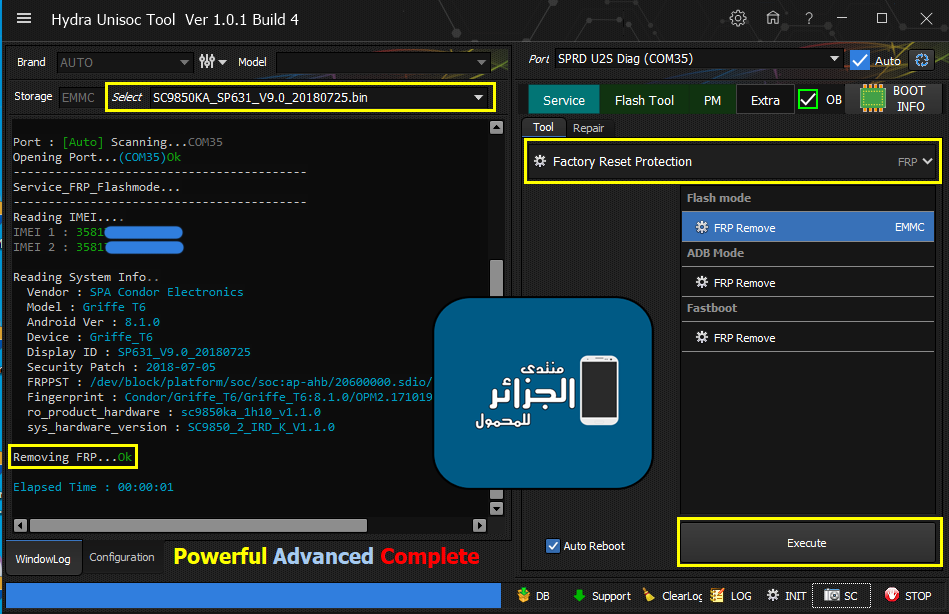
Condor Griffe T6 (SP631) Removing FRP

كود:
[B][FONT=Arial Black][SIZE=2]************* PRESS BOOT KEY *************
VOL + OR VOL - , OR Combination Vol - +
Feature Phone : Call Button
Please hold boot key until second boot..
*******************************************
Port : [Auto] Scanning...COM35
Opening Port...(COM35)Ok
Identifying... [SPRD3]
Sending Config Ok
Boot1 [hydra.fdl1] Ok
Spreadtrum Boot Block version 1.1
Boot2 [hydra.fdl2]
Verifying Loader 2.... Ok
Sending To phone.... Ok
Successfully booted..Ready to go...
Reading IMEI....
IMEI 1 : 3581XXXXXXXX
IMEI 2 : 3581XXXXXXXXX
Reading System Info..
Vendor : SPA Condor Electronics
Model : Griffe T6
Android Ver : 8.1.0
Device : Griffe_T6
Display ID : SP631_V9.0_20180725
Security Patch : 2018-07-05
FRPPST : /dev/block/platform/soc/soc:ap-ahb/20600000.sdio/by-name/persist
Fingerprint : Condor/Griffe_T6/Griffe_T6:8.1.0/OPM2.171019.012/26309:user/release-keys
ro_product_hardware : sc9850ka_1h10_v1.1.0
sys_hardware_version : SC9850_2_IRD_K_V1.1.0
[COLOR="#FF0000"]*** ONE BOOT PROCESSS ***
SPD Loader are now running...
Please do not remove cable
[/COLOR]
Closing Port...Ok..
[/SIZE][/FONT][/B]
كود:
[B][FONT=Arial Black][SIZE=2]Port : [Auto] Scanning...COM35
Opening Port...(COM35)Ok
------------------------------------------
Service_FRP_Flashmode...
------------------------------------------
Reading IMEI....
IMEI 1 : 3581XXXXXXXX
IMEI 2 : 3581XXXXXXXXX
Reading System Info..
Vendor : SPA Condor Electronics
Model : Griffe T6
Android Ver : 8.1.0
Device : Griffe_T6
Display ID : SP631_V9.0_20180725
Security Patch : 2018-07-05
FRPPST : /dev/block/platform/soc/soc:ap-ahb/20600000.sdio/by-name/persist
Fingerprint : Condor/Griffe_T6/Griffe_T6:8.1.0/OPM2.171019.012/26309:user/release-keys
ro_product_hardware : sc9850ka_1h10_v1.1.0
sys_hardware_version : SC9850_2_IRD_K_V1.1.0
[COLOR="#FF0000"]Removing FRP...Ok
[/COLOR]
Elapsed Time : 00:00:01
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Condor Plume P5 (PGN516) Ultra Power Option
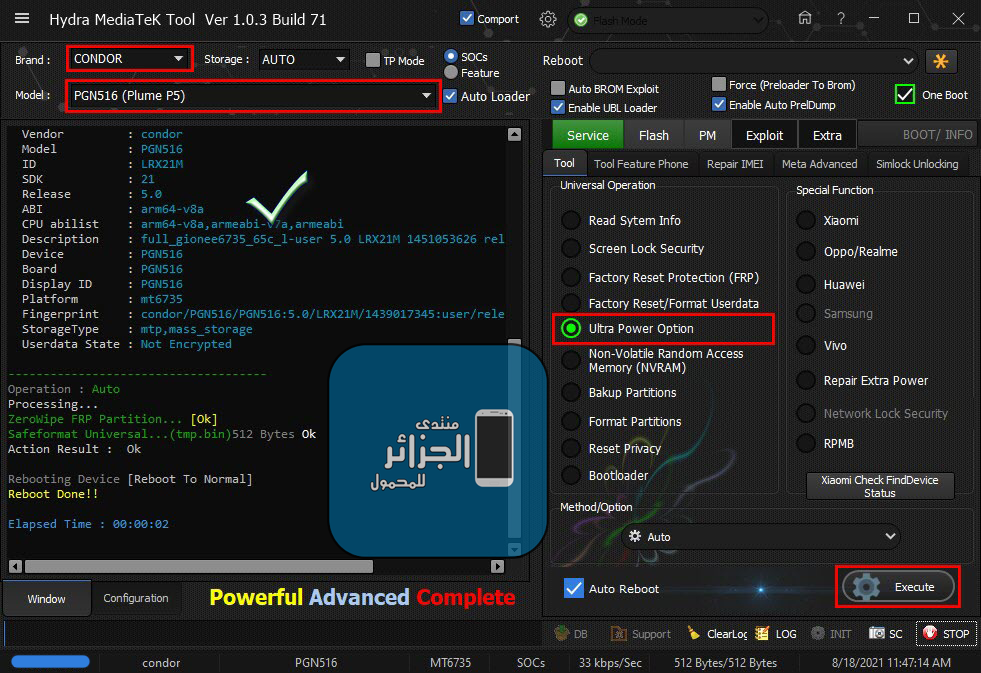
Condor Plume P5 (PGN516) Ultra Power Option

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1632 (Android) (COM4)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading System Info
Brand : condor
Vendor : condor
Model : PGN516
ID : LRX21M
SDK : 21
Release : 5.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Description : full_gionee6735_65c_l-user 5.0 LRX21M 1451053626 release-keys
Device : PGN516
Board : PGN516
Display ID : PGN516
Platform : mt6735
Fingerprint : condor/PGN516/PGN516:5.0/LRX21M/1439017345:user/release-keys
StorageType : mtp,mass_storage
Userdata State : Not Encrypted
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition... [Ok]
Safeformat Universal...(tmp.bin)512 Bytes Ok
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:02
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Condor Griffe T8 [SP532] Removing FRP Done
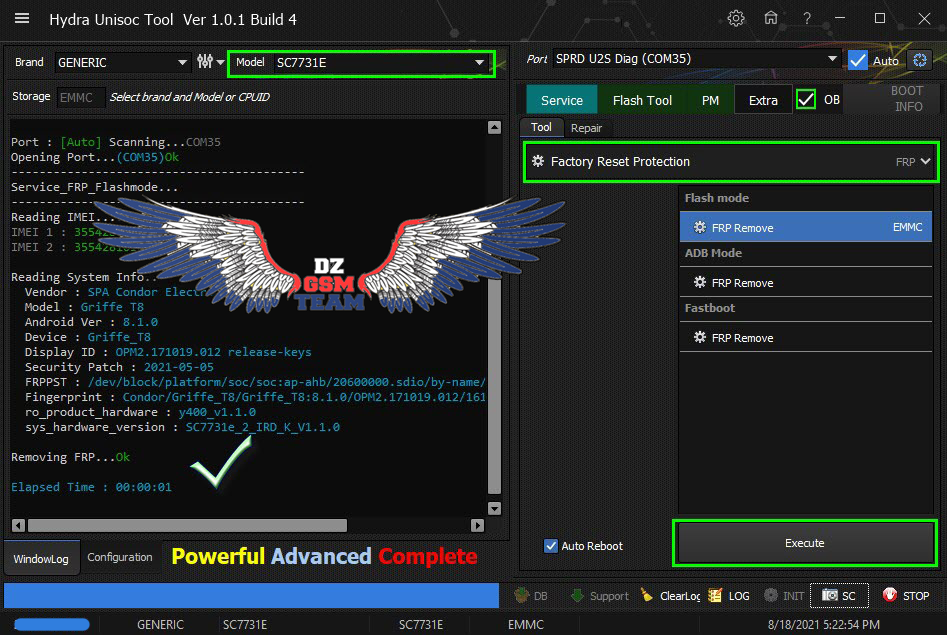
Condor Griffe T8 [SP532] Removing FRP Done

كود:
[B][FONT=Arial Black][SIZE=2]Port : [COLOR="#008000"][Auto][/COLOR] Scanning...COM35
Opening Port...([COLOR="#0000FF"]COM35[/COLOR])[COLOR="#008000"]Ok[/COLOR]
------------------------------------------
Service_FRP_Flashmode...
------------------------------------------
Reading IMEI....
IMEI 1 : [COLOR="#008000"]3554XXXXXXXXXXX[/COLOR]
IMEI 2 : [COLOR="#008000"]3554XXXXXXXXXXX[/COLOR]
Reading System Info..
Vendor : [COLOR="#0000FF"]SPA Condor Electronics[/COLOR]
Model : [COLOR="#0000FF"]Griffe T8[/COLOR]
Android Ver : [COLOR="#0000FF"]8.1.0[/COLOR]
Device : [COLOR="#0000FF"]Griffe_T8[/COLOR]
Display ID : [COLOR="#0000FF"]OPM2.171019.012 release-keys[/COLOR]
Security Patch : [COLOR="#0000FF"]2021-05-05[/COLOR]
FRPPST :[COLOR="#0000FF"] /dev/block/platform/soc/soc:ap-ahb/20600000.sdio/by-name/persist[/COLOR]
Fingerprint : [COLOR="#0000FF"]Condor/Griffe_T8/Griffe_T8:8.1.0/OPM2.171019.012/1619419820:user/release-keys[/COLOR]
ro_product_hardware : [COLOR="#0000FF"]y400_v1.1.0[/COLOR]
sys_hardware_version : [COLOR="#0000FF"]SC7731e_2_IRD_K_V1.1.0[/COLOR]
Removing FRP...[COLOR="#008000"]Ok[/COLOR]
[COLOR="#008080"]Elapsed Time : 00:00:01
[/COLOR][/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
ACE BUZZ 1 Factory Reset + Removing FRP
Factory Reset/Format Userdata
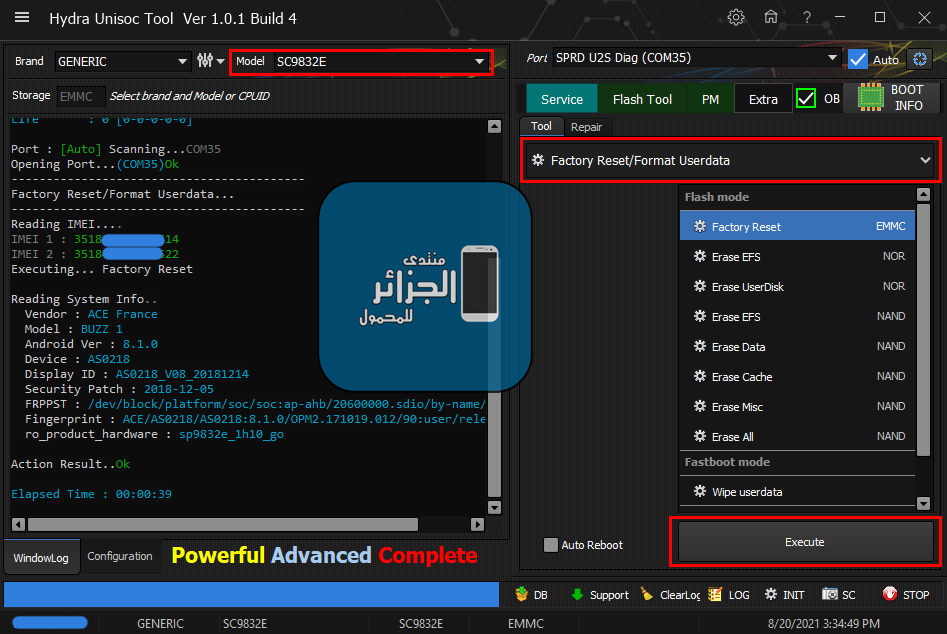
Service_FRP_Flashmode
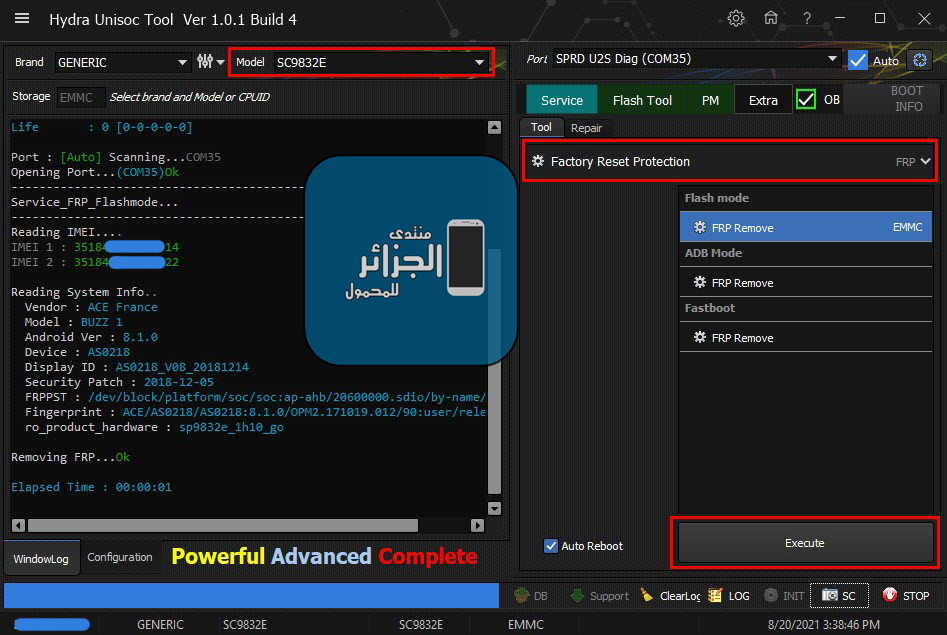
ACE BUZZ 1 Factory Reset + Removing FRP
Factory Reset/Format Userdata

كود:
[B][FONT=Arial Black][SIZE=2]Port : [Auto] Scanning...COM35
Opening Port...(COM35)Ok
------------------------------------------
Factory Reset/Format Userdata...
------------------------------------------
Reading IMEI....
IMEI 1 : 3518XXXXXXXXX14
IMEI 2 : 3518XXXXXXXXX22
Executing... Factory Reset
Reading System Info..
Vendor : ACE France
Model : BUZZ 1
Android Ver : 8.1.0
Device : AS0218
Display ID : AS0218_V08_20181214
Security Patch : 2018-12-05
FRPPST : /dev/block/platform/soc/soc:ap-ahb/20600000.sdio/by-name/persist
Fingerprint : ACE/AS0218/AS0218:8.1.0/OPM2.171019.012/90:user/release-keys
ro_product_hardware : sp9832e_1h10_go
Action Result..Ok
Elapsed Time : 00:00:39
[/SIZE][/FONT][/B]Service_FRP_Flashmode

كود:
[B][FONT=Arial Black][SIZE=2]Port : [Auto] Scanning...COM35
Opening Port...(COM35)Ok
------------------------------------------
Service_FRP_Flashmode...
------------------------------------------
Reading IMEI....
IMEI 1 : 3518XXXXXXXXX14
IMEI 2 : 3518XXXXXXXXX22
Reading System Info..
Vendor : ACE France
Model : BUZZ 1
Android Ver : 8.1.0
Device : AS0218
Display ID : AS0218_V08_20181214
Security Patch : 2018-12-05
FRPPST : /dev/block/platform/soc/soc:ap-ahb/20600000.sdio/by-name/persist
Fingerprint : ACE/AS0218/AS0218:8.1.0/OPM2.171019.012/90:user/release-keys
ro_product_hardware : sp9832e_1h10_go
Removing FRP...Ok
Elapsed Time : 00:00:01
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
IRIS TAB G7060 ZeroWipe FRP
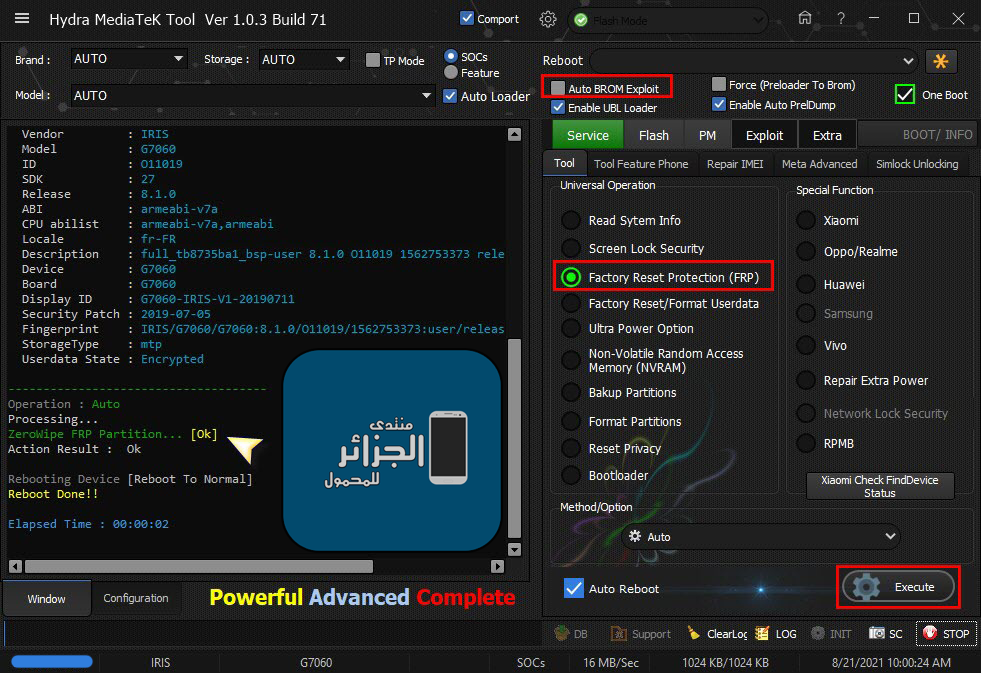
IRIS TAB G7060 ZeroWipe FRP

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1632 (Android) (COM4)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading System Info
Brand : IRIS
Vendor : IRIS
Model : G7060
ID : O11019
SDK : 27
Release : 8.1.0
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : fr-FR
Description : full_tb8735ba1_bsp-user 8.1.0 O11019 1562753373 release-keys
Device : G7060
Board : G7060
Display ID : G7060-IRIS-V1-20190711
Security Patch : 2019-07-05
Fingerprint : IRIS/G7060/G7060:8.1.0/O11019/1562753373:user/release-keys
StorageType : mtp
Userdata State : Encrypted
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition... [Ok]
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:02
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Starlight Star Plus Plus ZeroWipe FRP
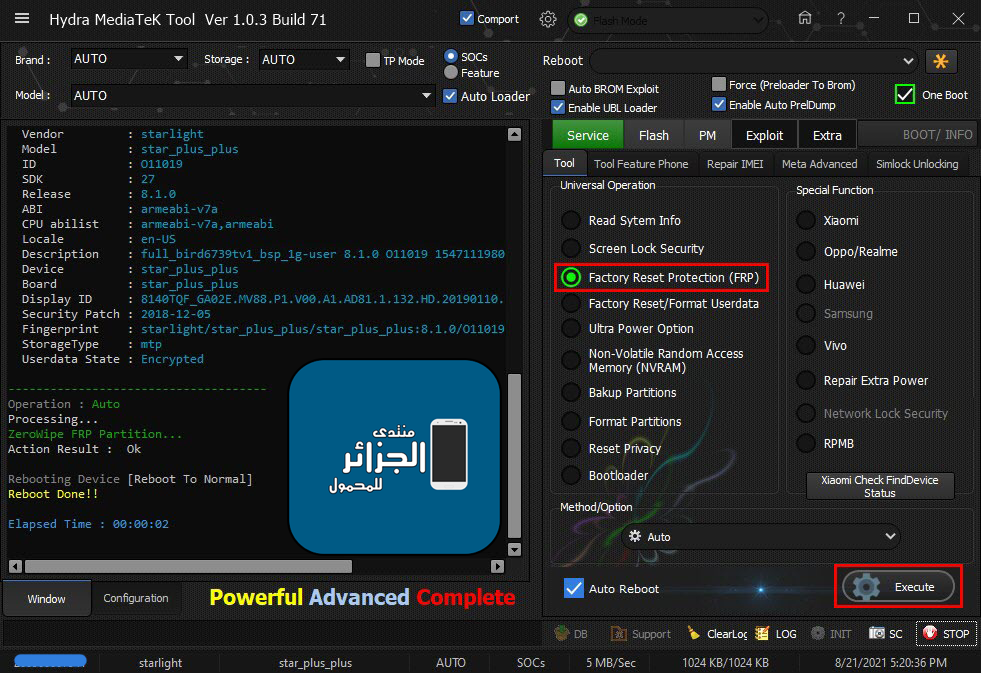
Starlight Star Plus Plus ZeroWipe FRP

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1632 (Android) (COM4)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : B26F2A486683C16A49CA20EA44F39298
ERAM Size : 0x0000000000020000 -128 KB
IRAM Size : 0x0000000040000000 -1024 MB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x00000001D2000000 -7.281 GB
eMMC CID : 90014A48384731650507F0A1721F923B - H8G1e
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Brand : starlight
Vendor : starlight
Model : star_plus_plus
ID : O11019
SDK : 27
Release : 8.1.0
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-US
Description : full_bird6739tv1_bsp_1g-user 8.1.0 O11019 1547111980 release-keys
Device : star_plus_plus
Board : star_plus_plus
Display ID : 8140TQF_GA02E.MV88.P1.V00.A1.AD81.1.132.HD.20190110.TST.EN
Security Patch : 2018-12-05
Fingerprint : starlight/star_plus_plus/star_plus_plus:8.1.0/O11019/1547111980:user/release-keys
StorageType : mtp
Userdata State : Encrypted
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition...
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:02
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Xiaomi Poco M3 (citrus) DEAD Flashing + Removing FRP
Done By Hydra Tool

Flashing Done
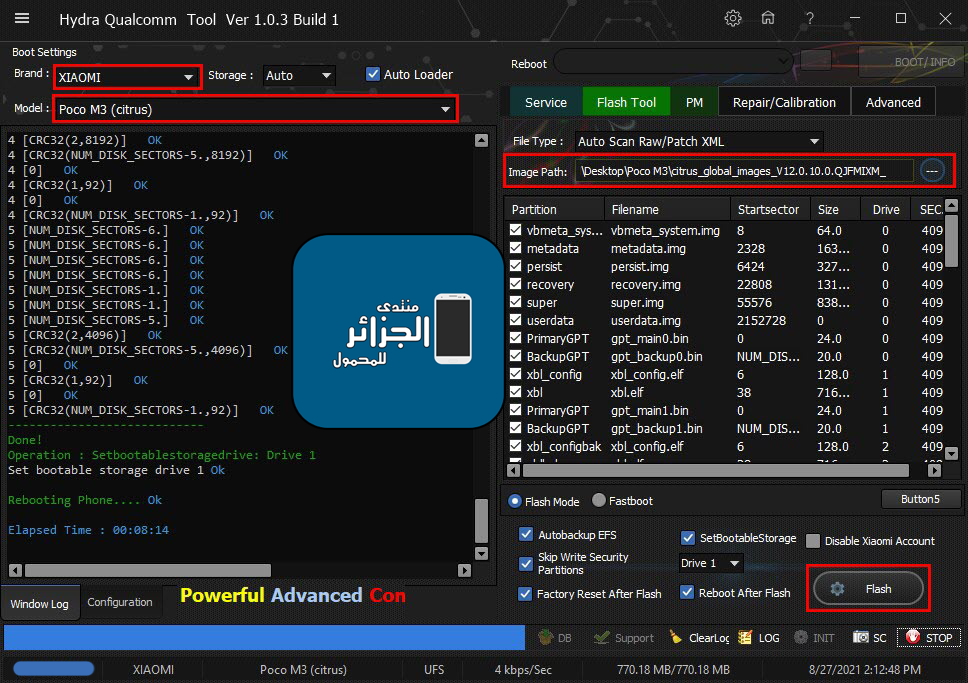
Removing FRP Done
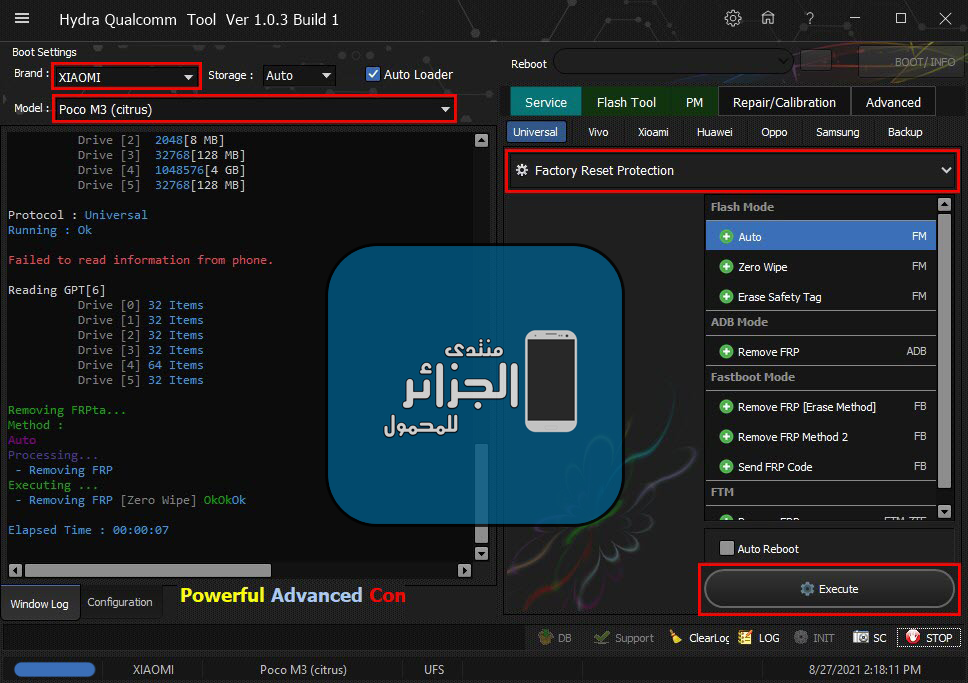

Xiaomi Poco M3 (citrus) DEAD Flashing + Removing FRP
Done By Hydra Tool

Flashing Done

كود:
[B][FONT=Arial Black][SIZE=2] Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM5)
SymbolicName :\??\USB#VID_05C6&PID_9008#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :03/25/2016,2.1.2.2
Getting device info......
Serial No.: 0xE4880CC3
HW_ID : 0014D0E100720000
MSM ID : 0x0014D0E1, SM_KAMORTA_H-
MODEL_ID : 0x0000
OEM_ID : 0x0072 - XIAOMI
PBL Ver : 00000001
PK HASH : 1bebe3863a6781db4b01086063007334de9e5ca14971c7c4f4358ec9d79cda46
Firehose Loader[0000000000720000_1bebe3863a6781db_159eb52f_XIAOMI.fhprg]
--------------------------------------------------
Header Type : New
TargetMSM :
Tag :
Version : 6
Code_size : 816
Signature_size : 256
fhVendor : XIAOMI
HW_ID : 0000000000720000
Vendor : XIAOMI
OEM_ID : 0072
MODEL_ID : 0000
SW_ID : 00000003
APP_ID : 00000000
pk_hash : 1bebe3863a6781db4b01086063007334de9e5ca14971c7c4f4358ec9d79cda4692ce5e948c6fd409408f4c919fcadfe3
OEM_VERSION : f2f760038334
IMAGE_VARIANT : KamortaPkgLAA
QC_VERSION : BOOT.XF.4.1-00187-KAMORTALAZ-2
--------------------------------------------------
SaharaBoot... Ok
Sending .................................Ok
Connecting to Firehose...
Ping...................... Ok
Configuration........
Identifying Chip........UFS
Ok
Chip Configuration :
MemoryName : UFS
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes :
MaxXMLSizeInBytes : 4096
TargetName :
Version : 1
DateTime : Nov 16 2020 - 01:25:39
*** STORAGE DEVICE INFO ***
Memory Type : UFS
Block Size in Bytes : 4096
Page Size : 4096
Manufacturer ID : 429
Serial Number : 2037279096
Firmware Version : 002
Product Name : H9HQ15ACPMBDAR
Physical Partitions : 6
Total Logical Blocks:
Drive [0] 30119936[114.898 GB]
Drive [1] 2048[8 MB]
Drive [2] 2048[8 MB]
Drive [3] 32768[128 MB]
Drive [4] 1048576[4 GB]
Drive [5] 32768[128 MB]
Protocol : Universal
Running : Ok
Failed to read information from phone.
Reading GPT[6]
Drive [0] 32 Items
Drive [1] 32 Items
Drive [2] 32 Items
Drive [3] 32 Items
Drive [4] 64 Items
Drive [5] 32 Items
Backup Security partitions...
Reading Security Items....
> modemst1
> modemst2
> fsg
> fsc
C:\Hydra Tool\Backup\Security_Backup\___Security_082721140440.sec
Backup Security Success....
----------------------------
Flashing Selected Partitions....
- vbmeta_system(0)[vbmeta_system.img] Ok
- metadata(0)[metadata.img] Ok
- persist(0)[persist.img] Ok
- recovery(0)[recovery.img] Ok
- super(0)[super.img] Ok
- userdata(0)[userdata.img] Ok
- PrimaryGPT(0)[gpt_main0.bin] Ok
- xbl_config(1)[xbl_config.elf] Ok
- xbl(1)[xbl.elf] Ok
- PrimaryGPT(1)[gpt_main1.bin] Ok
- xbl_configbak(2)[xbl_config.elf] Ok
- xblbak(2)[xbl.elf] Ok
- PrimaryGPT(2)[gpt_main2.bin] Ok
- PrimaryGPT(3)[gpt_main3.bin] Ok
- multiimgoem(4)[multi_image.mbn] Ok
- vbmeta(4)[vbmeta.img] Ok
- qupfw(4)[qupv3fw.elf] Ok
- devcfg(4)[devcfg.mbn] Ok
- storsec(4)[storsec.mbn] Ok
- hyp(4)[hyp.mbn] Ok
- hypbak(4)[hyp.mbn] Ok
- cmnlib(4)[cmnlib.mbn] Ok
- cmnlibbak(4)[cmnlib.mbn] Ok
- cmnlib64(4)[cmnlib64.mbn] Ok
- cmnlib64bak(4)[cmnlib64.mbn] Ok
- keymaster(4)[km4.mbn] Ok
- keymasterbak(4)[km4.mbn] Ok
- bluetooth(4)[BTFM.bin] Ok
- abl(4)[abl.elf] Ok
- ablbak(4)[abl.elf] Ok
- imagefv(4)[imagefv.elf] Ok
- imagefvbak(4)[imagefv.elf] Ok
- uefisecapp(4)[uefi_sec.mbn] Ok
- uefisecappbak(4)[uefi_sec.mbn] Ok
- featenabler(4)[featenabler.mbn] Ok
- featenablerbak(4)[featenabler.mbn] Ok
- misc(4)[misc.img] Ok
- rpm(4)[rpm.mbn] Ok
- rpmbak(4)[rpm.mbn] Ok
- tz(4)[tz.mbn] Ok
- tzbak(4)[tz.mbn] Ok
- logfs(4)[logfs_ufs_8mb.bin] Ok
- dtbo(4)[dtbo.img] Ok
- dsp(4)[dspso.bin] Ok
- boot(4)[boot.img] Ok
- modem(4)[NON-HLOS.bin] Ok
- cache(4)[cache.img] Ok
- cust(4)[cust.img] Ok
- PrimaryGPT(4)[gpt_main4.bin] Ok
- PrimaryGPT(5)[gpt_main5.bin] Ok
Flashing Patch Configuration..
0 [NUM_DISK_SECTORS-6.] OK
0 [NUM_DISK_SECTORS-6.] OK
0 [NUM_DISK_SECTORS-6.] OK
0 [NUM_DISK_SECTORS-6.] OK
0 [NUM_DISK_SECTORS-1.] OK
0 [NUM_DISK_SECTORS-1.] OK
0 [NUM_DISK_SECTORS-5.] OK
0 [CRC32(2,4096)] OK
0 [CRC32(NUM_DISK_SECTORS-5.,4096)] OK
0 [0] OK
0 [CRC32(1,92)] OK
0 [0] OK
0 [CRC32(NUM_DISK_SECTORS-1.,92)] OK
1 [NUM_DISK_SECTORS-6.] OK
1 [NUM_DISK_SECTORS-6.] OK
1 [NUM_DISK_SECTORS-6.] OK
1 [NUM_DISK_SECTORS-6.] OK
1 [NUM_DISK_SECTORS-1.] OK
1 [NUM_DISK_SECTORS-1.] OK
1 [NUM_DISK_SECTORS-5.] OK
1 [CRC32(2,4096)] OK
1 [CRC32(NUM_DISK_SECTORS-5.,4096)] OK
1 [0] OK
1 [CRC32(1,92)] OK
1 [0] OK
1 [CRC32(NUM_DISK_SECTORS-1.,92)] OK
2 [NUM_DISK_SECTORS-6.] OK
2 [NUM_DISK_SECTORS-6.] OK
2 [NUM_DISK_SECTORS-6.] OK
2 [NUM_DISK_SECTORS-6.] OK
2 [NUM_DISK_SECTORS-1.] OK
2 [NUM_DISK_SECTORS-1.] OK
2 [NUM_DISK_SECTORS-5.] OK
2 [CRC32(2,4096)] OK
2 [CRC32(NUM_DISK_SECTORS-5.,4096)] OK
2 [0] OK
2 [CRC32(1,92)] OK
2 [0] OK
2 [CRC32(NUM_DISK_SECTORS-1.,92)] OK
3 [NUM_DISK_SECTORS-6.] OK
3 [NUM_DISK_SECTORS-6.] OK
3 [NUM_DISK_SECTORS-6.] OK
3 [NUM_DISK_SECTORS-6.] OK
3 [NUM_DISK_SECTORS-1.] OK
3 [NUM_DISK_SECTORS-1.] OK
3 [NUM_DISK_SECTORS-5.] OK
3 [CRC32(2,4096)] OK
3 [CRC32(NUM_DISK_SECTORS-5.,4096)] OK
3 [0] OK
3 [CRC32(1,92)] OK
3 [0] OK
3 [CRC32(NUM_DISK_SECTORS-1.,92)] OK
4 [NUM_DISK_SECTORS-6.] OK
4 [NUM_DISK_SECTORS-6.] OK
4 [NUM_DISK_SECTORS-6.] OK
4 [NUM_DISK_SECTORS-6.] OK
4 [NUM_DISK_SECTORS-1.] OK
4 [NUM_DISK_SECTORS-1.] OK
4 [NUM_DISK_SECTORS-5.] OK
4 [CRC32(2,8192)] OK
4 [CRC32(NUM_DISK_SECTORS-5.,8192)] OK
4 [0] OK
4 [CRC32(1,92)] OK
4 [0] OK
4 [CRC32(NUM_DISK_SECTORS-1.,92)] OK
5 [NUM_DISK_SECTORS-6.] OK
5 [NUM_DISK_SECTORS-6.] OK
5 [NUM_DISK_SECTORS-6.] OK
5 [NUM_DISK_SECTORS-6.] OK
5 [NUM_DISK_SECTORS-1.] OK
5 [NUM_DISK_SECTORS-1.] OK
5 [NUM_DISK_SECTORS-5.] OK
5 [CRC32(2,4096)] OK
5 [CRC32(NUM_DISK_SECTORS-5.,4096)] OK
5 [0] OK
5 [CRC32(1,92)] OK
5 [0] OK
5 [CRC32(NUM_DISK_SECTORS-1.,92)] OK
----------------------------
Done!
Operation : Setbootablestoragedrive: Drive 1
Set bootable storage drive 1 Ok
Rebooting Phone.... Ok
Elapsed Time : 00:08:14
[/SIZE][/FONT][/B]Removing FRP Done

كود:
[B][FONT=Arial Black][SIZE=2]PreOperation Configuration
Brand : XIAOMI Model : Poco M3 (citrus) Storage : Auto
Loader: 0000000000720000_1bebe3863a6781db_159eb52f_XIAOMI.fhprg
Port : Auto
Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM5)
SymbolicName :\??\USB#VID_05C6&PID_9008#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :03/25/2016,2.1.2.2
Getting device info......
Serial No.: 0xE4880CC3
HW_ID : 0014D0E100720000
MSM ID : 0x0014D0E1, SM_KAMORTA_H-
MODEL_ID : 0x0000
OEM_ID : 0x0072 - XIAOMI
PBL Ver : 00000001
PK HASH : 1bebe3863a6781db4b01086063007334de9e5ca14971c7c4f4358ec9d79cda46
Firehose Loader[0000000000720000_1bebe3863a6781db_159eb52f_XIAOMI.fhprg]
--------------------------------------------------
Header Type : New
TargetMSM :
Tag :
Version : 6
Code_size : 816
Signature_size : 256
fhVendor : XIAOMI
HW_ID : 0000000000720000
Vendor : XIAOMI
OEM_ID : 0072
MODEL_ID : 0000
SW_ID : 00000003
APP_ID : 00000000
pk_hash : 1bebe3863a6781db4b01086063007334de9e5ca14971c7c4f4358ec9d79cda4692ce5e948c6fd409408f4c919fcadfe3
OEM_VERSION : f2f760038334
IMAGE_VARIANT : KamortaPkgLAA
QC_VERSION : BOOT.XF.4.1-00187-KAMORTALAZ-2
--------------------------------------------------
SaharaBoot... Ok
Sending .................................Ok
Connecting to Firehose...
Ping...................... Ok
Configuration........
Identifying Chip........UFS
Ok
Chip Configuration :
MemoryName : UFS
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes :
MaxXMLSizeInBytes : 4096
TargetName :
Version : 1
DateTime : Nov 16 2020 - 01:25:39
*** STORAGE DEVICE INFO ***
Memory Type : UFS
Block Size in Bytes : 4096
Page Size : 4096
Manufacturer ID : 429
Serial Number : 2037279096
Firmware Version : 002
Product Name : H9HQ15ACPMBDAR
Physical Partitions : 6
Total Logical Blocks:
Drive [0] 30119936[114.898 GB]
Drive [1] 2048[8 MB]
Drive [2] 2048[8 MB]
Drive [3] 32768[128 MB]
Drive [4] 1048576[4 GB]
Drive [5] 32768[128 MB]
Protocol : Universal
Running : Ok
Failed to read information from phone.
Reading GPT[6]
Drive [0] 32 Items
Drive [1] 32 Items
Drive [2] 32 Items
Drive [3] 32 Items
Drive [4] 64 Items
Drive [5] 32 Items
Removing FRPta...
Method :
Auto
Processing...
- Removing FRP
Executing ...
- Removing FRP [Zero Wipe] OkOkOk
Elapsed Time : 00:00:07
[/SIZE][/FONT][/B]
رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
STREAM B2Plus (HT28) ZeroWipe FRP
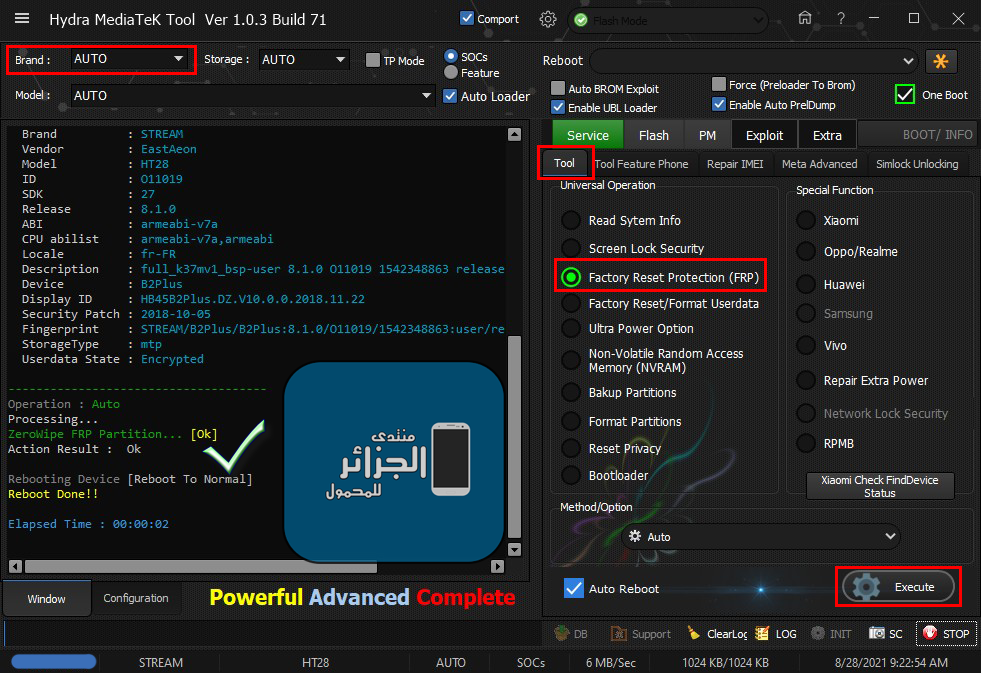
STREAM B2Plus (HT28) ZeroWipe FRP

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :DA_HIGHSPEED_VCOM
FriendlyName :MediaTek DA USB VCOM (Android) (COM7)
Device :6&944c330&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2001#6&944c330&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading System Info
Brand : STREAM
Vendor : EastAeon
Model : HT28
ID : O11019
SDK : 27
Release : 8.1.0
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : fr-FR
Description : full_k37mv1_bsp-user 8.1.0 O11019 1542348863 release-keys
Device : B2Plus
Display ID : HB45B2Plus.DZ.V10.0.0.2018.11.22
Security Patch : 2018-10-05
Fingerprint : STREAM/B2Plus/B2Plus:8.1.0/O11019/1542348863:user/release-keys
StorageType : mtp
Userdata State : Encrypted
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition... [Ok]
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:02
[/SIZE][/FONT][/B]