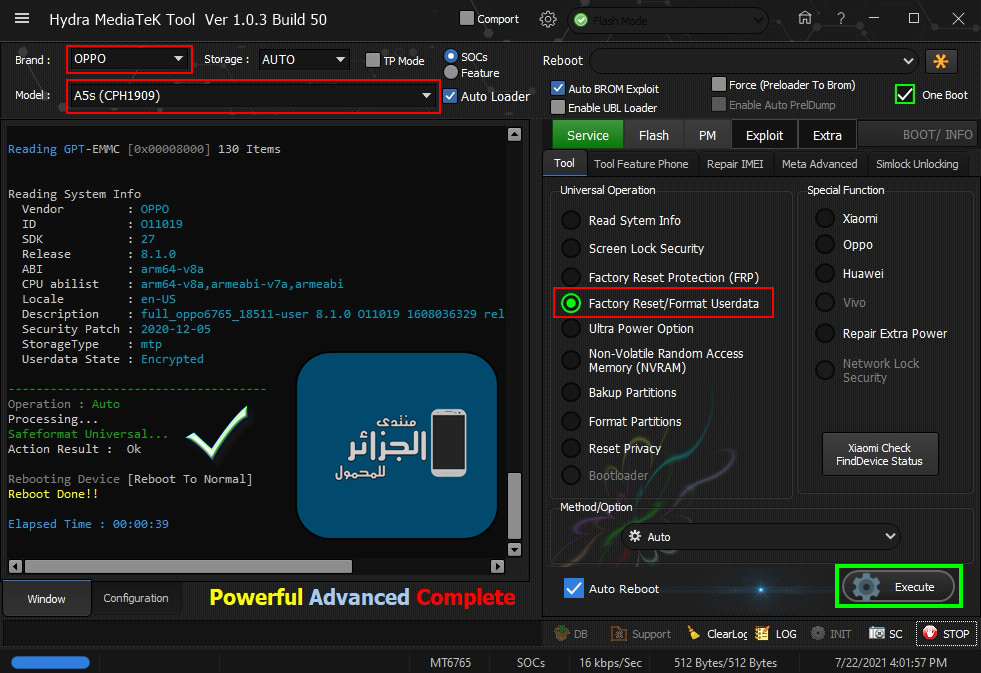
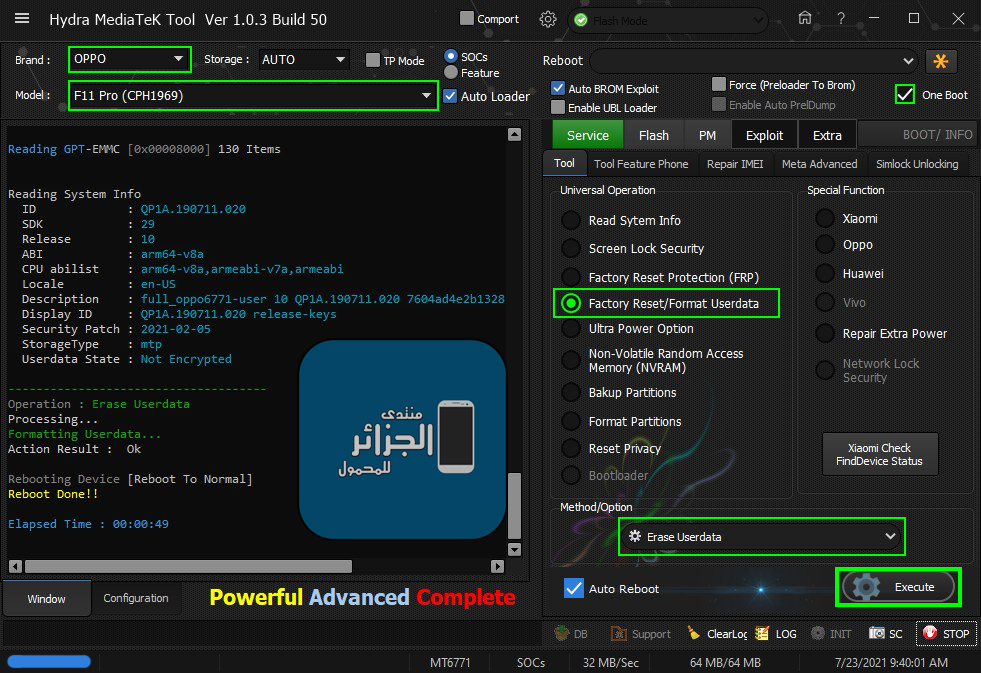
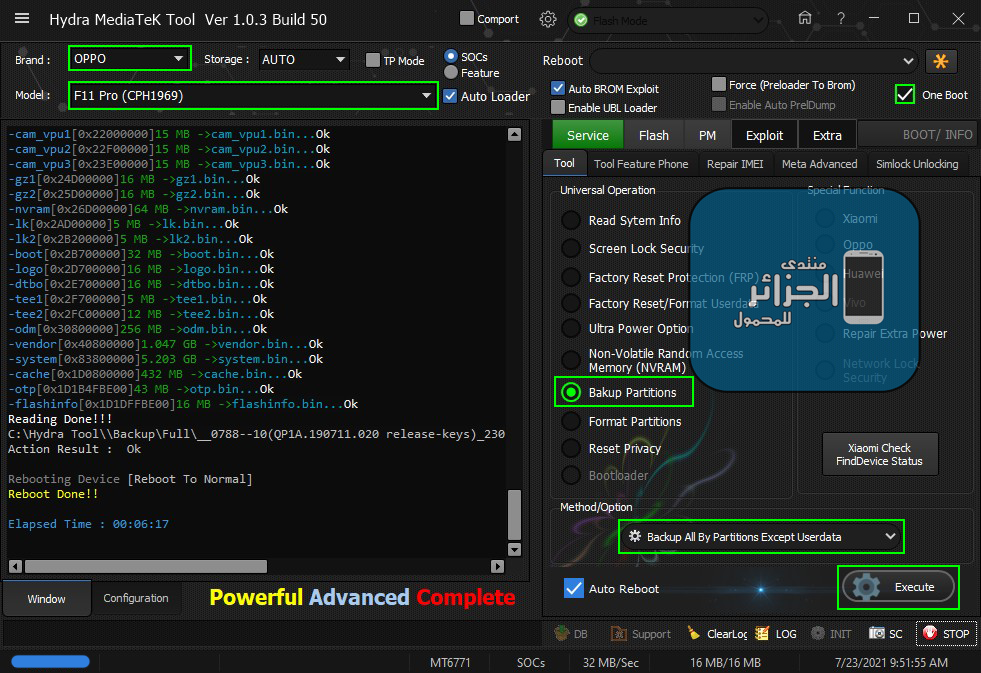
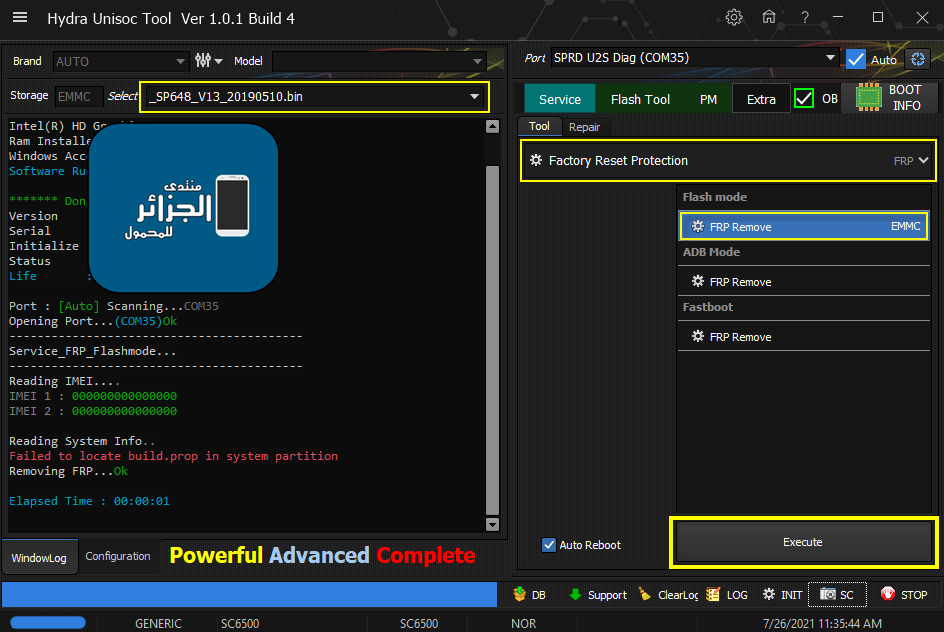
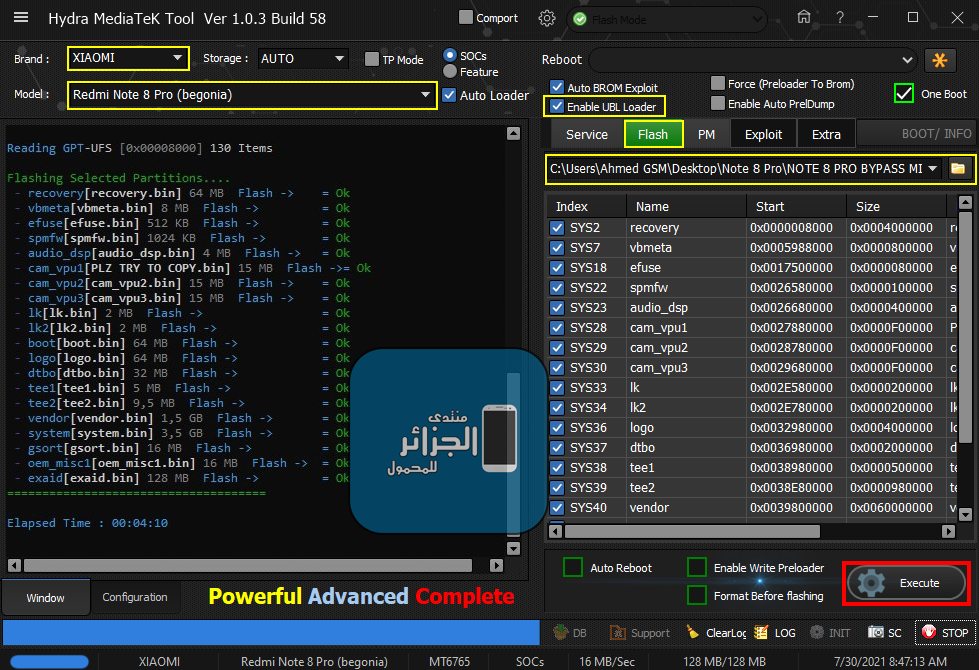
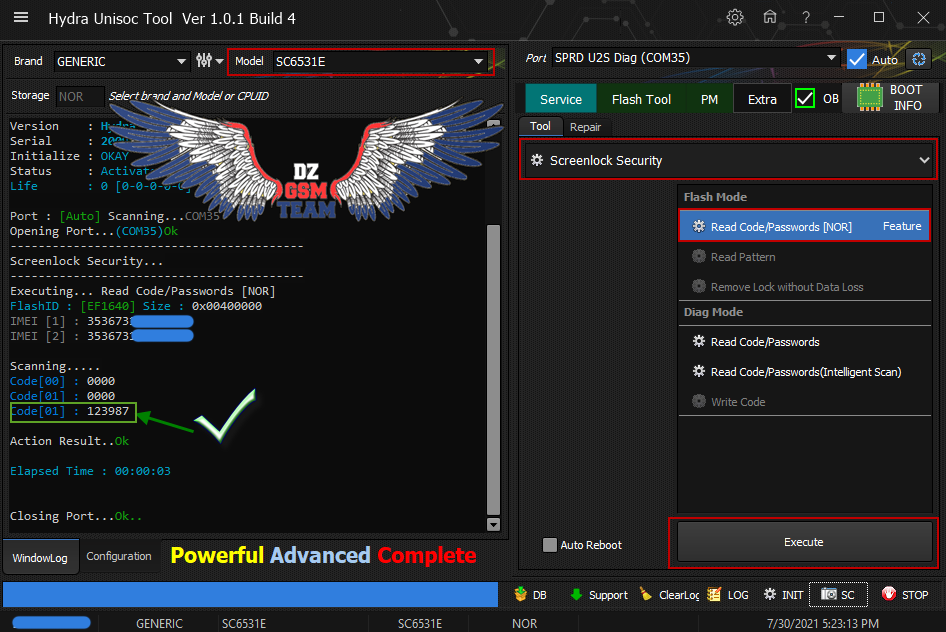
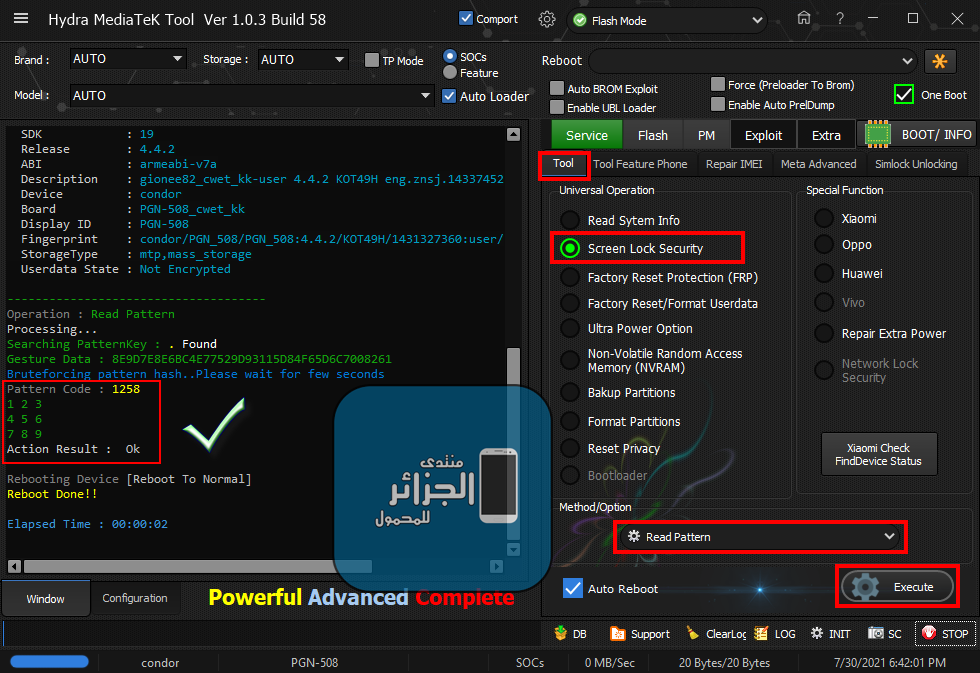
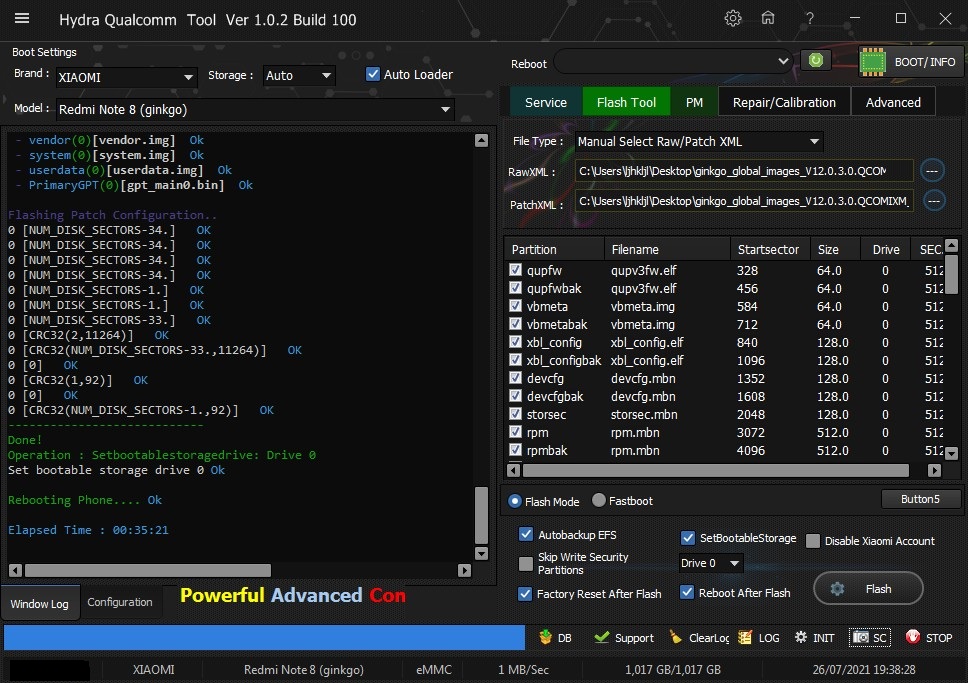
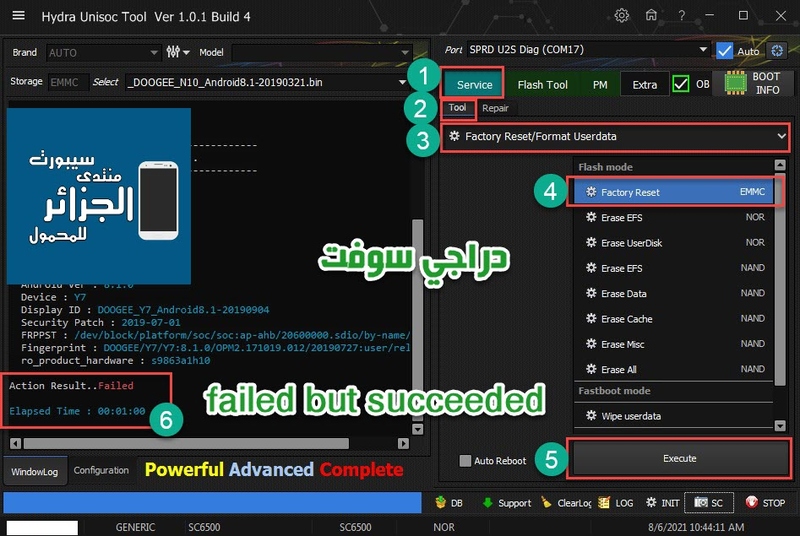
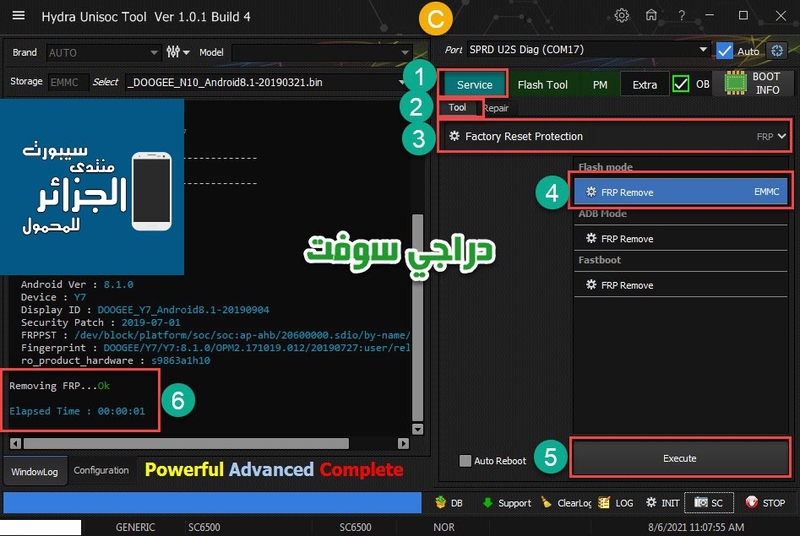
رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Benzo G-PADLITE (K708) IMEI REPAIR
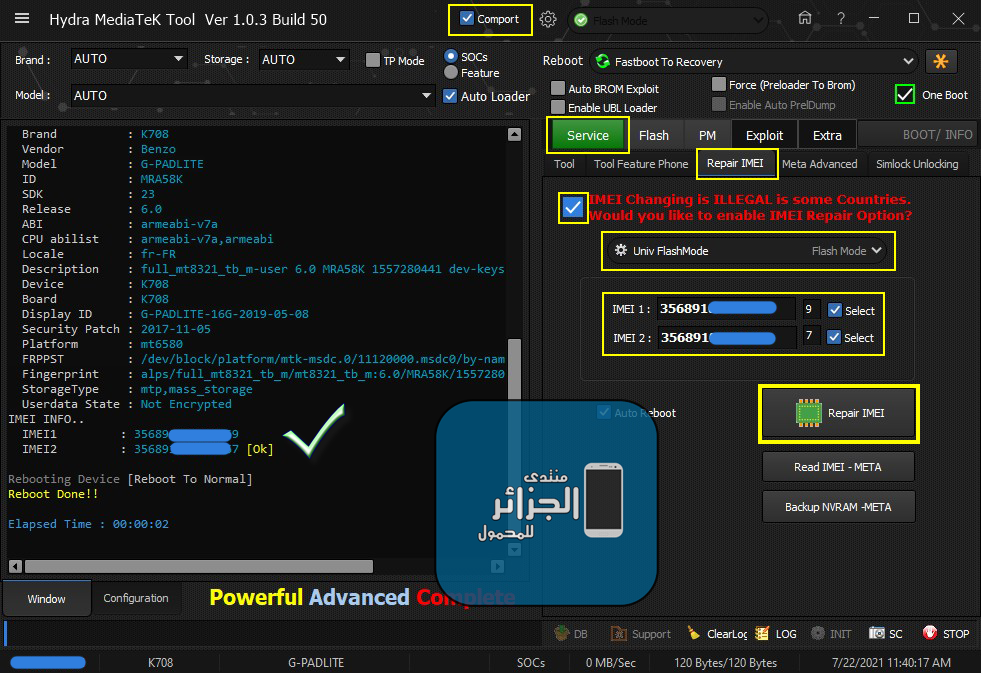
Benzo G-PADLITE (K708) IMEI REPAIR

كود:
[B][FONT=Arial Black][SIZE=2]***IMEI REPAIR FUNCTION****
Univ FlashMode
Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1632 (Android) (COM4)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
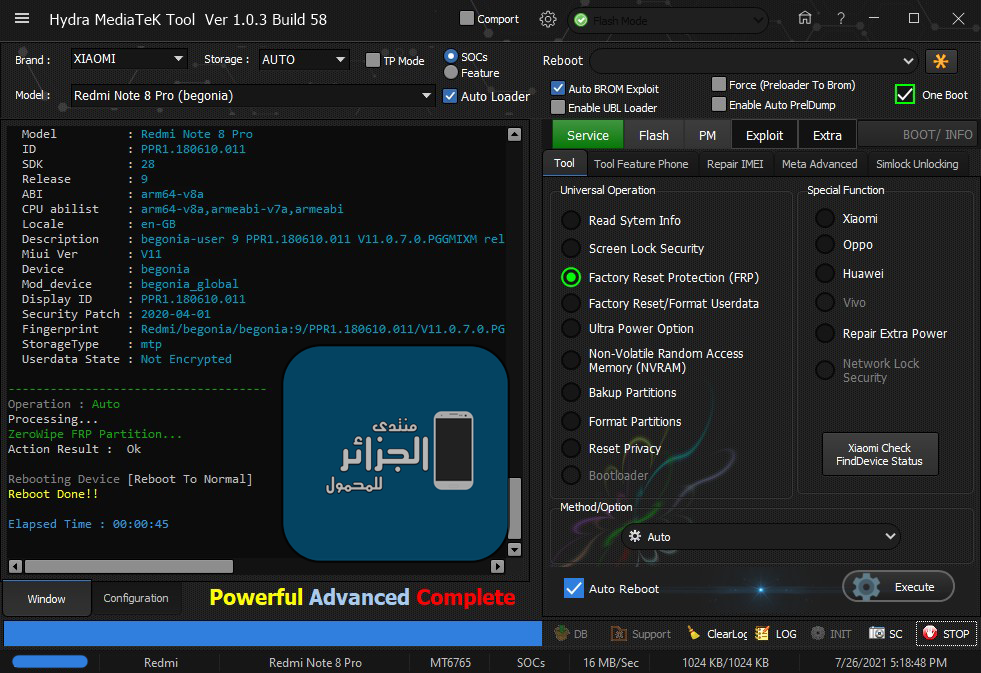
Reading System Info
Brand : K708
Vendor : Benzo
Model : G-PADLITE
ID : MRA58K
SDK : 23
Release : 6.0
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : fr-FR
Description : full_mt8321_tb_m-user 6.0 MRA58K 1557280441 dev-keys
Device : K708
Board : K708
Display ID : G-PADLITE-16G-2019-05-08
Security Patch : 2017-11-05
Platform : mt6580
FRPPST : /dev/block/platform/mtk-msdc.0/11120000.msdc0/by-name/frp
Fingerprint : alps/full_mt8321_tb_m/mt8321_tb_m:6.0/MRA58K/1557280441:user/dev-keys
StorageType : mtp,mass_storage
Userdata State : Not Encrypted
IMEI INFO..
IMEI1 : [COLOR="#40E0D0"]35689XXXXXXXXX9[/COLOR]
IMEI2 : [COLOR="#40E0D0"]35689XXXXXXXXX7 [/COLOR][COLOR="#FF0000"][Ok][/COLOR]
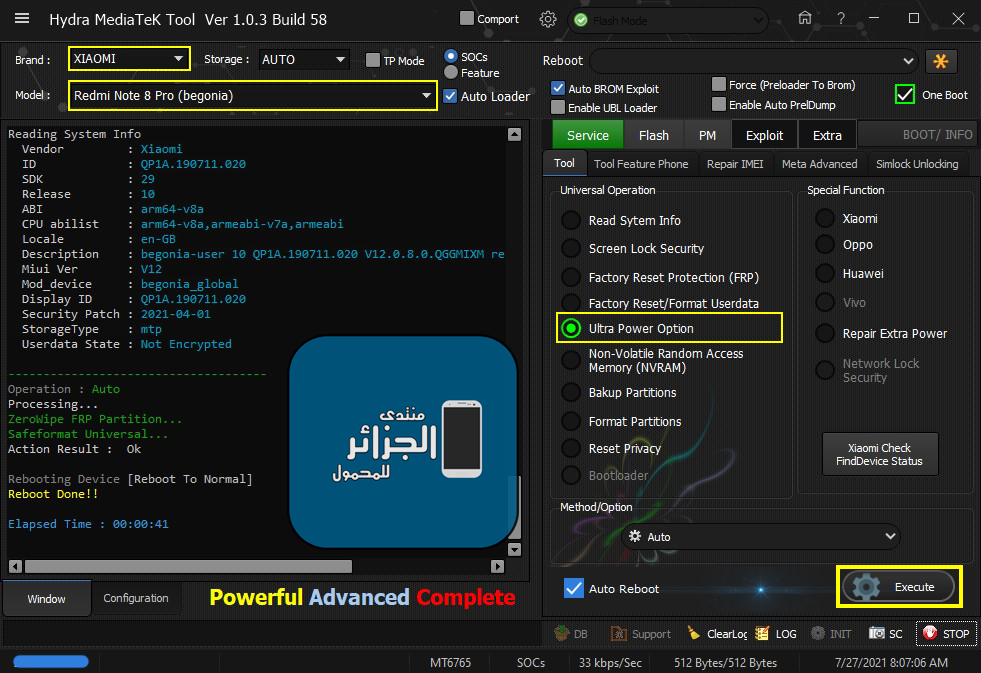
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:02
[/SIZE][/FONT][/B]