أنت تستخدم أحد المتصفحات القديمة. قد لا يتم عرض هذا الموقع أو المواقع الأخرى بشكل صحيح.
يجب عليك ترقية متصفحك أو استخدام أحد المتصفحات البديلة.
يجب عليك ترقية متصفحك أو استخدام أحد المتصفحات البديلة.
تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
- بادئ الموضوع DZ-Djamel-GSM
- تاريخ البدء
رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
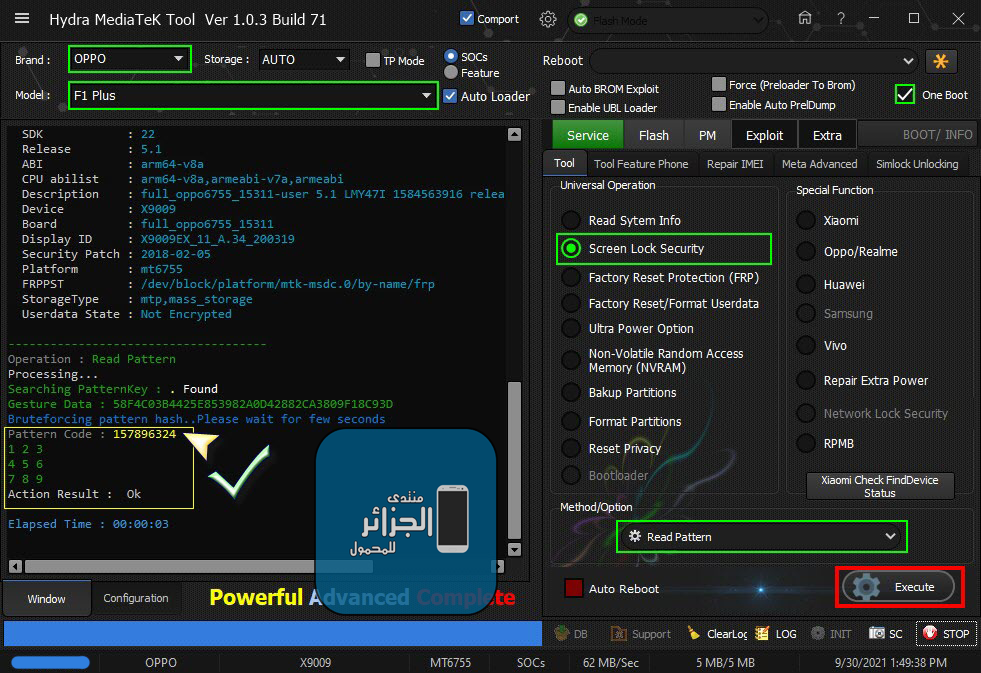
Xiaomi Redmi 9a (dandelion) Ultra Power Option
Safe Format + Erasing FRP
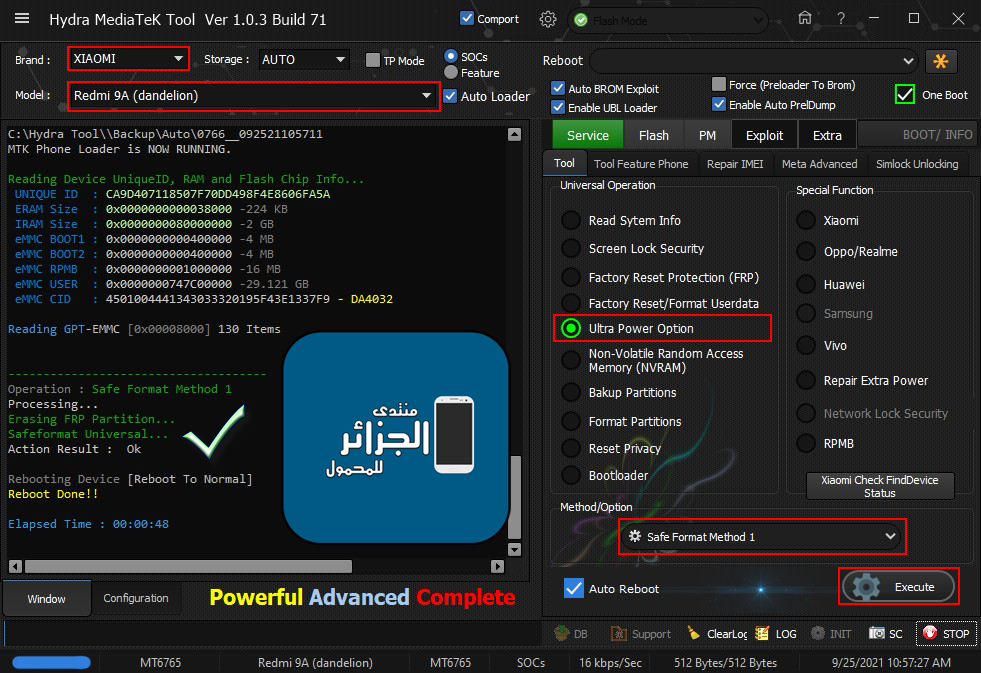
Xiaomi Redmi 9a (dandelion) Ultra Power Option
Safe Format + Erasing FRP

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1633 (COM21)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E7
SBC : 01 (True)
SLA : 02 (True)
DAA : 04 (True)
SWJTAG : 06 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking...Ok
C:\Hydra Tool\Backup\Preloader_dump\prel.tmp
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : E2E4E225A8924384B84CE31F0F10041A
Stage 1..[Size:216440]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Preloader Initialization...
Parsing prel.tmp
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : CA9D407118507F70DD498F4E8606FA5A
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 4501004441343033320195F43E1337F9 - DA4032
Executing : ACCEPTED...
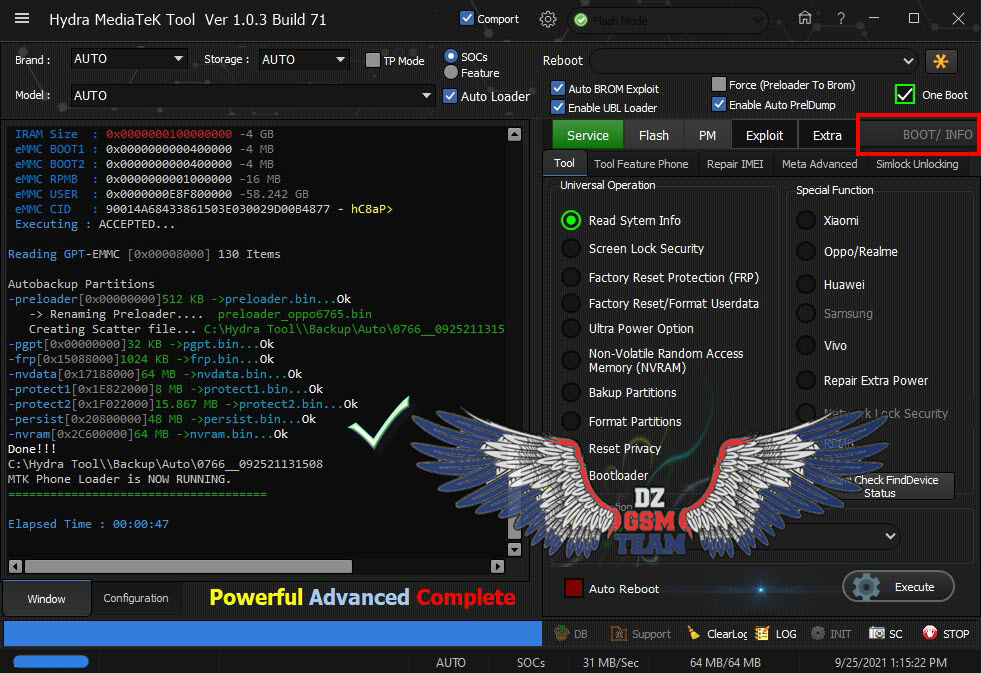
Reading GPT-EMMC [0x00008000] 130 Items
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader.... preloader_k62v1_64_bsp.bin
Creating Scatter file... C:\Hydra Tool\\Backup\Auto\0766__092521105711\MT6765_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x3BD88000]1024 KB ->frp.bin...Ok
-nvdata[0x3DE88000]64 MB ->nvdata.bin...Ok
-protect1[0x45522000]8 MB ->protect1.bin...Ok
-protect2[0x45D22000]10.867 MB ->protect2.bin...Ok
-persist[0x47000000]48 MB ->persist.bin...Ok
-nvram[0x52E80000]64 MB ->nvram.bin...Ok
Done!!!
C:\Hydra Tool\\Backup\Auto\0766__092521105711
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : CA9D407118507F70DD498F4E8606FA5A
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 4501004441343033320195F43E1337F9 - DA4032
Reading GPT-EMMC [0x00008000] 130 Items
-------------------------------------
Operation : Safe Format Method 1
Processing...
Erasing FRP Partition...
Safeformat Universal...
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:48
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
OPPO A54 (CPH2239) Ultra Power Option
Erase Userdata + Erasing FRP
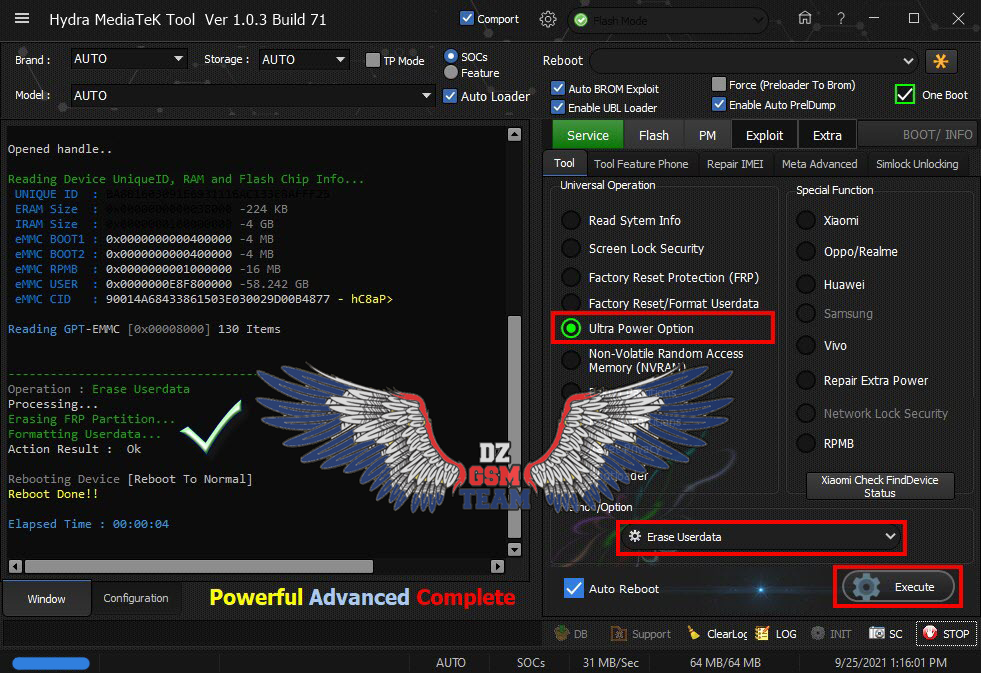
OPPO A54 (CPH2239) Ultra Power Option
Erase Userdata + Erasing FRP


كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1633 (COM21)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : BA8B1603091E6931116AC133EBAFFF25
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000100000000 -4 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000E8F800000 -58.242 GB
eMMC CID : 90014A68433861503E030029D00B4877 - hC8aP>
Reading GPT-EMMC [0x00008000] 130 Items
-------------------------------------
Operation : Erase Userdata
Processing...
Erasing FRP Partition...
Formatting Userdata...
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:04
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Starlight C_Note_Pro Ultra Power Option
ZeroWipe FRP + Safeformat
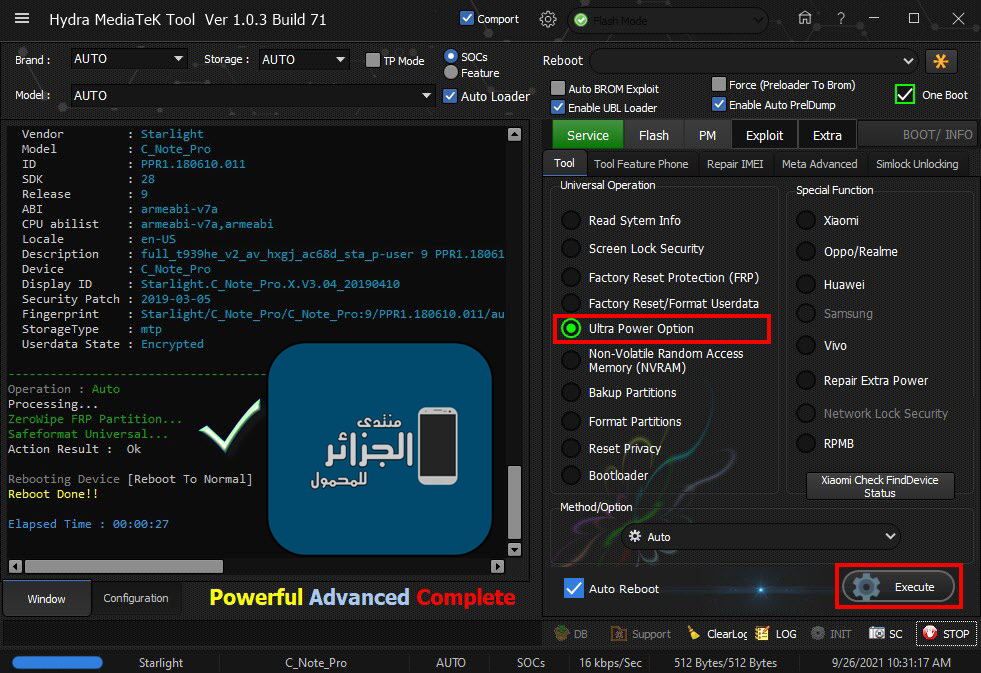
Starlight C_Note_Pro Ultra Power Option
ZeroWipe FRP + Safeformat

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1633 (Android) (COM3)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0699MT6739 [6739]
hw subcode : 8A00
hw version : CB00
sw version : 0002
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
FUSEID : 00000000
SECURE VERSION : FF
BL VERSION : 03
Preparing Download Agent..
DA : 6739.bin
Agent: MTK_DOWNLOAD_AGENT -HYDRA
Ver : MTK_AllInOne_DA_v3.3001.2020-11-03.22:07_536568
Init : Loader [1]
Sending : Accepted
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Mode : preloader
Execute Secondary Loader
Init : Loader [2]
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 14F07F560C6E7AFB9CD99EEC803BC3AF
ERAM Size : 0x0000000000020000 -128 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 90014A484247346132A404931C0E53DD - HBG4a2
DA Speed : high-speed
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Brand : Starlight
Vendor : Starlight
Model : C_Note_Pro
ID : PPR1.180610.011
SDK : 28
Release : 9
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-US
Description : full_t939he_v2_av_hxgj_ac68d_sta_p-user 9 PPR1.180610.011 eng.autoft.20190410.191855 release-keys
Device : C_Note_Pro
Display ID : Starlight.C_Note_Pro.X.V3.04_20190410
Security Patch : 2019-03-05
Fingerprint : Starlight/C_Note_Pro/C_Note_Pro:9/PPR1.180610.011/autoftp04101917:user/release-keys
StorageType : mtp
Userdata State : Encrypted
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader.... preloader_t939he_v2_av_hxgj_ac68d_sta_p.bin
Creating Scatter file... C:\Hydra Tool\\Backup\Auto\0699_Starlight_C_Note_Pro_C_Note_Pro_9_PPR1.180610.011_autoftp04101917_092621103103\MT6739_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x02D88000]1024 KB ->frp.bin...Ok
-nvdata[0x03688000]32 MB ->nvdata.bin...Ok
-protect1[0x07688000]8 MB ->protect1.bin...Ok
-protect2[0x07E88000]9.469 MB ->protect2.bin...Ok
-persist[0x09000000]48 MB ->persist.bin...Ok
-nvram[0x13700000]5 MB ->nvram.bin...Ok
Done!!!
C:\Hydra Tool\\Backup\Auto\0699_Starlight_C_Note_Pro_C_Note_Pro_9_PPR1.180610.011_autoftp04101917_092621103103
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 14F07F560C6E7AFB9CD99EEC803BC3AF
ERAM Size : 0x0000000000020000 -128 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 90014A484247346132A404931C0E53DD - HBG4a2
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Brand : Starlight
Vendor : Starlight
Model : C_Note_Pro
ID : PPR1.180610.011
SDK : 28
Release : 9
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-US
Description : full_t939he_v2_av_hxgj_ac68d_sta_p-user 9 PPR1.180610.011 eng.autoft.20190410.191855 release-keys
Device : C_Note_Pro
Display ID : Starlight.C_Note_Pro.X.V3.04_20190410
Security Patch : 2019-03-05
Fingerprint : Starlight/C_Note_Pro/C_Note_Pro:9/PPR1.180610.011/autoftp04101917:user/release-keys
StorageType : mtp
Userdata State : Encrypted
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition...
Safeformat Universal...
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:27
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Redmi Note 8 Pro (begonia) Ultra Power Option
(ZeroWipe FRP + Safeformat)
Done By Hydra Tool
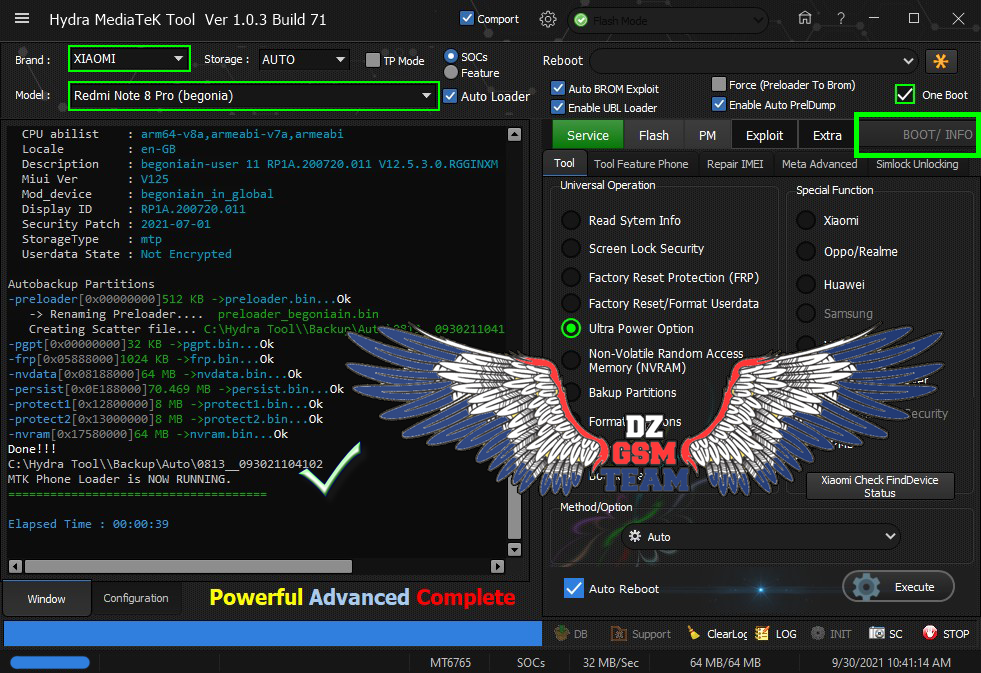
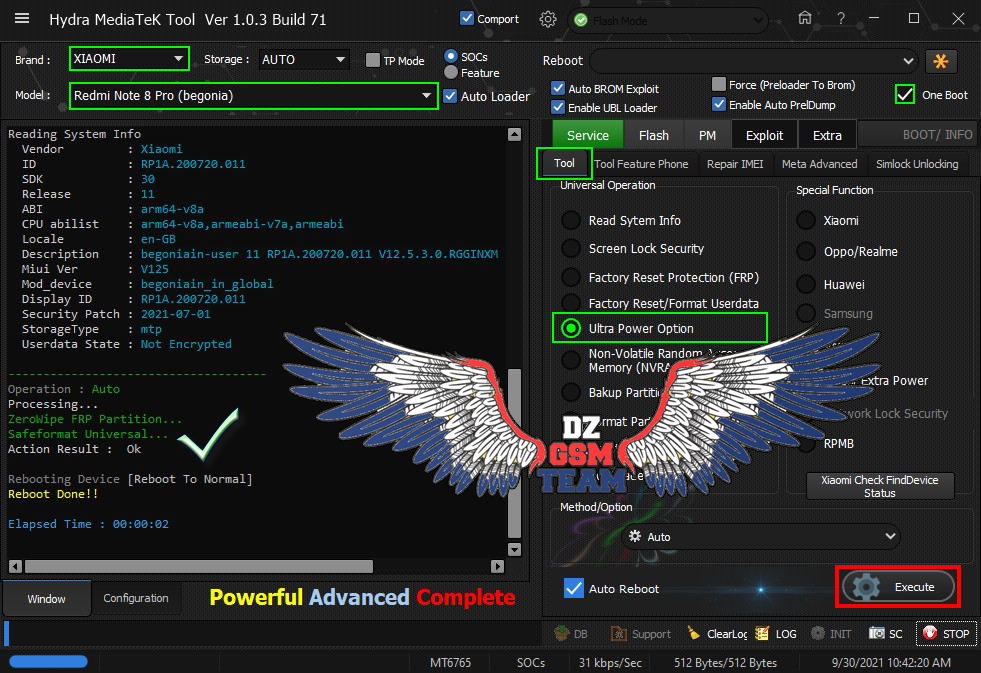
Redmi Note 8 Pro (begonia) Ultra Power Option
(ZeroWipe FRP + Safeformat)
Done By Hydra Tool

كود:
[B][FONT=Arial Black][SIZE=2]Brand : XIAOMI Model : Redmi Note 8 Pro (begonia) Connection : Flash Mode
=====================================
How To Boot : Power off phone
* BROM Mode : Press VOL + or Press VOL -+
* Preloader Mode : Just Insert cable
Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1633 (COM21)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0813MT6785 [6785]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E7
SBC : 01 (True)
SLA : 02 (True)
DAA : 04 (True)
SWJTAG : 06 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking...Ok
C:\Hydra Tool\Backup\Preloader_dump\prel.tmp
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0813MT6785 [6785]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : 5F421864E8048714FE392A82F79C8BEA
Stage 1..[Size:234968]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Preloader Initialization...
Parsing prel.tmp
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 7D36670F8B2B9E30970127A654DFBBEC
ERAM Size : 0x0000000000080000 -512 KB
IRAM Size : 0x0000000180000000 -6 GB
UFS LU0 Size: 0x0000000000400000 -4 MB
UFS LU1 Size: 0x0000000000400000 -4 MB
UFS LU2 Size: 0x0000001DCB000000 -119.172 GB
UFS CID : ÎKM2V8001CM-B707
UFS UNIQID : 00330062003200310065003300610035
Executing : ACCEPTED...
Reading GPT-UFS [0x00008000] 130 Items
Reading System Info
Vendor : Xiaomi
ID : RP1A.200720.011
SDK : 30
Release : 11
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-GB
Description : begoniain-user 11 RP1A.200720.011 V12.5.3.0.RGGINXM release-keys
Miui Ver : V125
Mod_device : begoniain_in_global
Display ID : RP1A.200720.011
Security Patch : 2021-07-01
StorageType : mtp
Userdata State : Not Encrypted
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader.... preloader_begoniain.bin
Creating Scatter file... C:\Hydra Tool\\Backup\Auto\0813__093021104102\MT6785_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x05888000]1024 KB ->frp.bin...Ok
-nvdata[0x08188000]64 MB ->nvdata.bin...Ok
-persist[0x0E188000]70.469 MB ->persist.bin...Ok
-protect1[0x12800000]8 MB ->protect1.bin...Ok
-protect2[0x13000000]8 MB ->protect2.bin...Ok
-nvram[0x17580000]64 MB ->nvram.bin...Ok
Done!!!
C:\Hydra Tool\\Backup\Auto\0813__093021104102
MTK Phone Loader is NOW RUNNING.
=====================================
Elapsed Time : 00:00:39
[/SIZE][/FONT][/B]
كود:
[B][FONT=Arial Black][SIZE=2]=====================================
Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1633 (COM21)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 7D36670F8B2B9E30970127A654DFBBEC
ERAM Size : 0x0000000000080000 -512 KB
IRAM Size : 0x0000000180000000 -6 GB
UFS LU0 Size: 0x0000000000400000 -4 MB
UFS LU1 Size: 0x0000000000400000 -4 MB
UFS LU2 Size: 0x0000001DCB000000 -119.172 GB
UFS CID : ÎKM2V8001CM-B707
UFS UNIQID : 00330062003200310065003300610035
Reading GPT-UFS [0x00008000] 130 Items
Reading System Info
Vendor : Xiaomi
ID : RP1A.200720.011
SDK : 30
Release : 11
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-GB
Description : begoniain-user 11 RP1A.200720.011 V12.5.3.0.RGGINXM release-keys
Miui Ver : V125
Mod_device : begoniain_in_global
Display ID : RP1A.200720.011
Security Patch : 2021-07-01
StorageType : mtp
Userdata State : Not Encrypted
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition...
Safeformat Universal...
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:02
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Samsung A10S (SM-A107F) U8 FRP Remove
Format Selected Partition : Formatting [persistent] Ok
Done With Hydra Tool
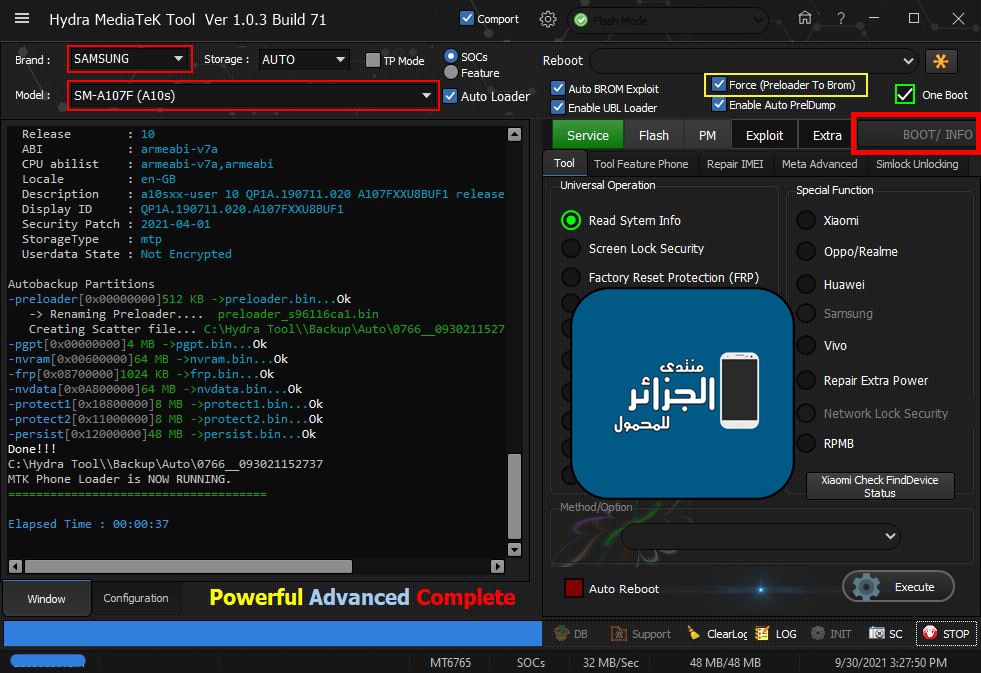
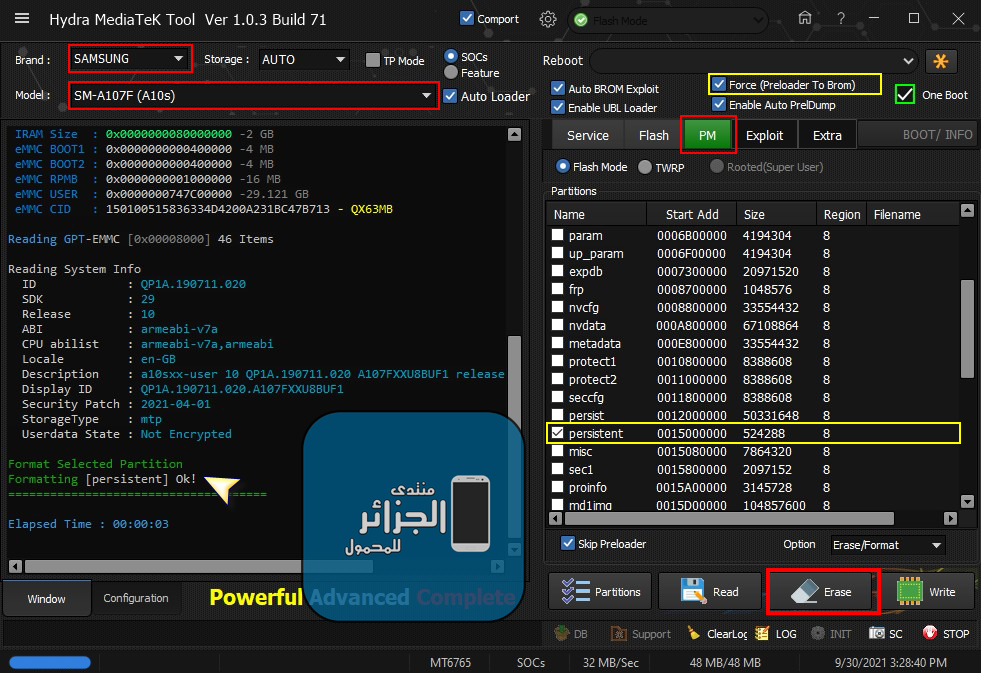
Samsung A10S (SM-A107F) U8 FRP Remove
Format Selected Partition : Formatting [persistent] Ok
Done With Hydra Tool


كود:
[B][FONT=Arial Black][SIZE=2]
Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1633 (COM21)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 753EA43DF97A9D6FFA0B176CA9522045
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 150100515836334D4200A231BC47B713 - QX63MB
Reading GPT-EMMC [0x00008000] 46 Items
Reading System Info
ID : QP1A.190711.020
SDK : 29
Release : 10
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-GB
Description : a10sxx-user 10 QP1A.190711.020 A107FXXU8BUF1 release-keys
Display ID : QP1A.190711.020.A107FXXU8BUF1
Security Patch : 2021-04-01
StorageType : mtp
Userdata State : Not Encrypted
Format Selected Partition
Formatting [persistent] Ok!
=====================================
Elapsed Time : 00:00[/SIZE][/FONT][/B]:[B][FONT=Arial Black][SIZE=2]03[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Starlight C Note Pro ZeroWipe FRP
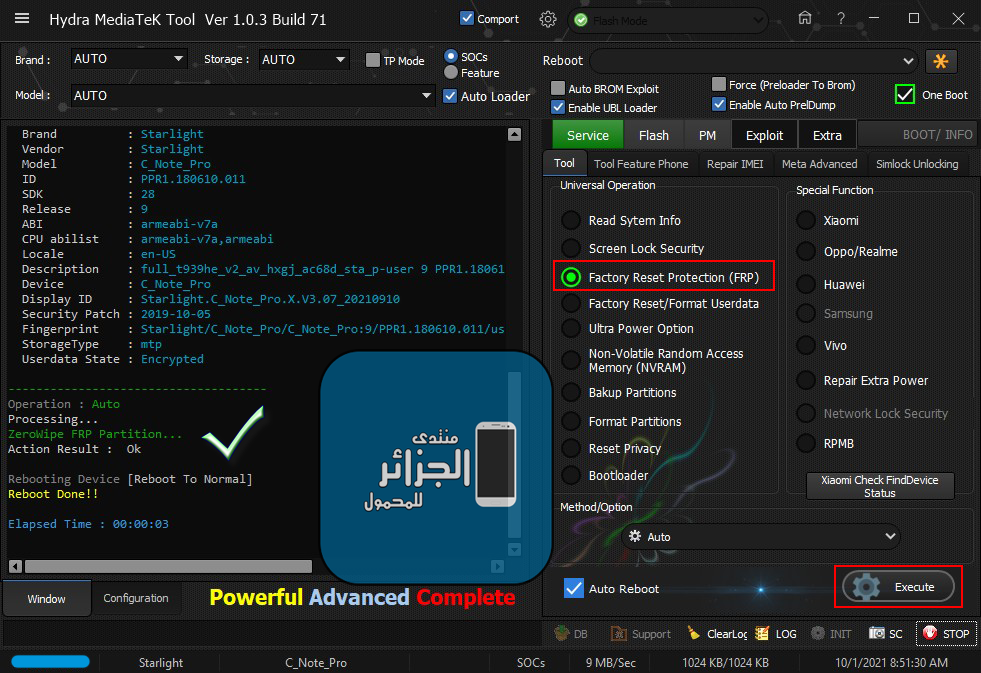
Starlight C Note Pro ZeroWipe FRP

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1633 (Android) (COM3)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : F7849C3C46B814049D74634ABF776E47
ERAM Size : 0x0000000000020000 -128 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 13014E53304A394237100AA979D3C5B5 - S0J9B7
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Brand : Starlight
Vendor : Starlight
Model : C_Note_Pro
ID : PPR1.180610.011
SDK : 28
Release : 9
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-US
Description : full_t939he_v2_av_hxgj_ac68d_sta_p-user 9 PPR1.180610.011 eng.user.20210910.153203 release-keys
Device : C_Note_Pro
Display ID : Starlight.C_Note_Pro.X.V3.07_20210910
Security Patch : 2019-10-05
Fingerprint : Starlight/C_Note_Pro/C_Note_Pro:9/PPR1.180610.011/user09101531:user/release-keys
StorageType : mtp
Userdata State : Encrypted
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition...
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:03
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
OPPO A5S (CPH1909) Ultra Power Option
(ZeroWipe FRP + Safeformat)
Done By Hydra Tool
OPPO A5S (CPH1909) Ultra Power Option
(ZeroWipe FRP + Safeformat)
Done By Hydra Tool


كود:
[B][FONT=Arial Black][SIZE=2]Brand : OPPO Model : A5s (CPH1909) Connection : Flash Mode
=====================================
How To Boot : Power off phone
* BROM Mode : Press VOL + or Press VOL -+
* Preloader Mode : Just Insert cable
Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1633 (COM21)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E5
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking...Ok
C:\Hydra Tool\Backup\Preloader_dump\prel.tmp
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : 5136E3C2B360382611E2201F25F74EB9
Stage 1..[Size:216440]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Preloader Initialization...
Parsing prel.tmp
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : EEEBFEC38EBAED10E79ED09E230A7BAC
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 150100474436424D420123DD9BD776F7 - GD6BMB
Executing : ACCEPTED...
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
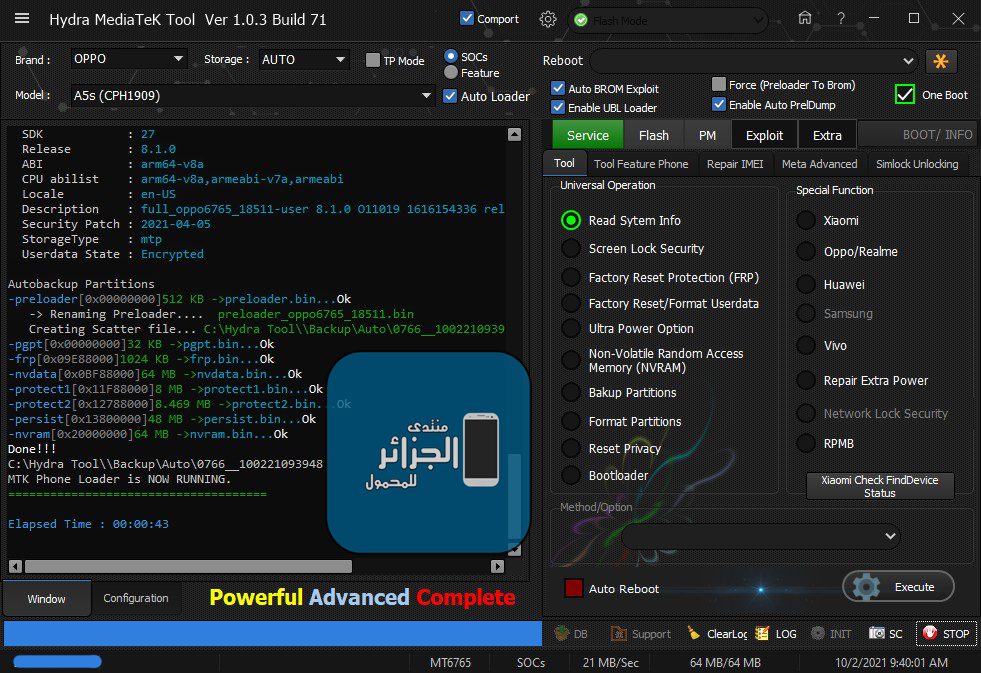
Vendor : OPPO
ID : O11019
SDK : 27
Release : 8.1.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_oppo6765_18511-user 8.1.0 O11019 1616154336 release-keys
Security Patch : 2021-04-05
StorageType : mtp
Userdata State : Encrypted
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader.... preloader_oppo6765_18511.bin
Creating Scatter file... C:\Hydra Tool\\Backup\Auto\0766__100221093948\MT6765_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x09E88000]1024 KB ->frp.bin...Ok
-nvdata[0x0BF88000]64 MB ->nvdata.bin...Ok
-protect1[0x11F88000]8 MB ->protect1.bin...Ok
-protect2[0x12788000]8.469 MB ->protect2.bin...Ok
-persist[0x13800000]48 MB ->persist.bin...Ok
-nvram[0x20000000]64 MB ->nvram.bin...Ok
Done!!!
C:\Hydra Tool\\Backup\Auto\0766__100221093948
MTK Phone Loader is NOW RUNNING.
=====================================
Elapsed Time : 00:00:43
[/SIZE][/FONT][/B]
كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1633 (COM21)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : EEEBFEC38EBAED10E79ED09E230A7BAC
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 150100474436424D420123DD9BD776F7 - GD6BMB
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Vendor : OPPO
ID : O11019
SDK : 27
Release : 8.1.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_oppo6765_18511-user 8.1.0 O11019 1616154336 release-keys
Security Patch : 2021-04-05
StorageType : mtp
Userdata State : Encrypted
-------------------------------------
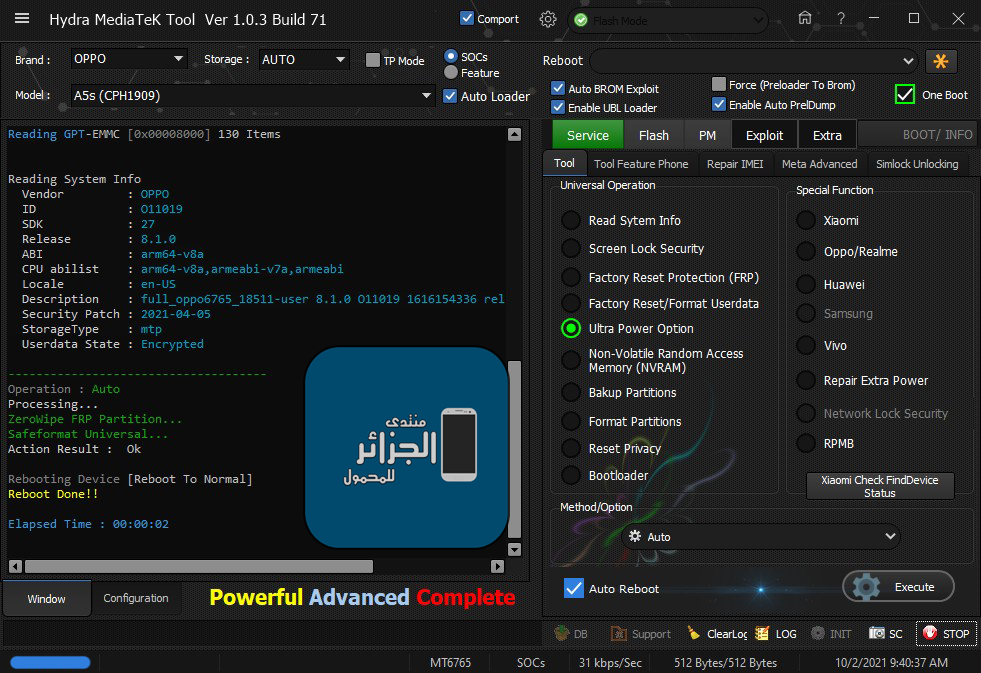
Operation : Auto
Processing...
ZeroWipe FRP Partition...
Safeformat Universal...
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:02
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
IRIS IS2S Stuck On Logo Done By Ultra Power Option
(ZeroWipe FRP + Safeformat Universal)
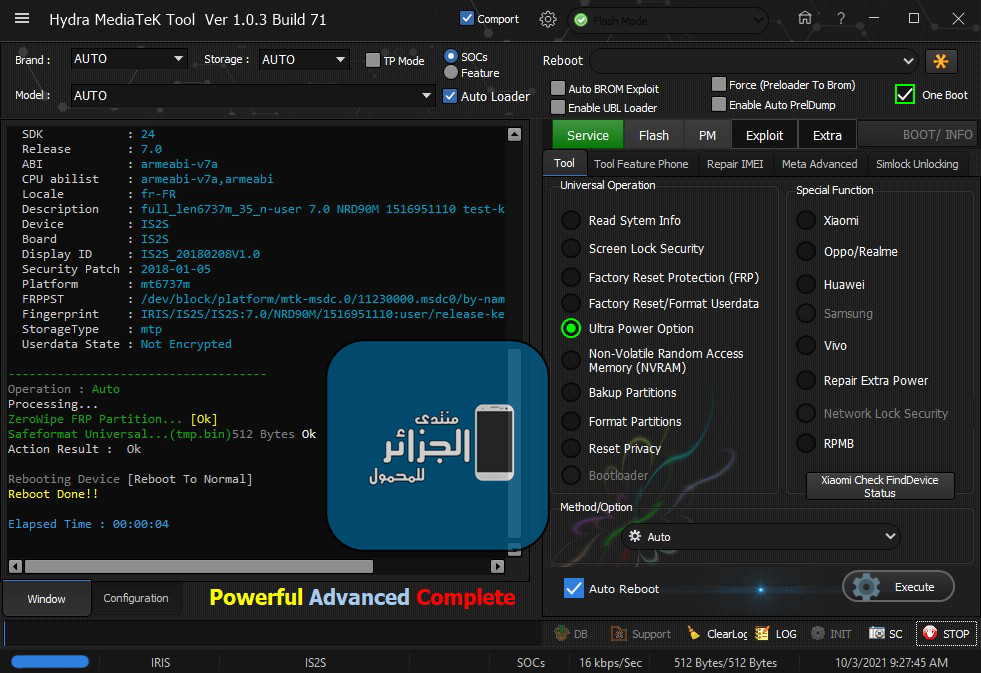
IRIS IS2S Stuck On Logo Done By Ultra Power Option
(ZeroWipe FRP + Safeformat Universal)


كود:
[B][FONT=Arial Black][SIZE=2]=====================================
Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1633 (Android) (COM3)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
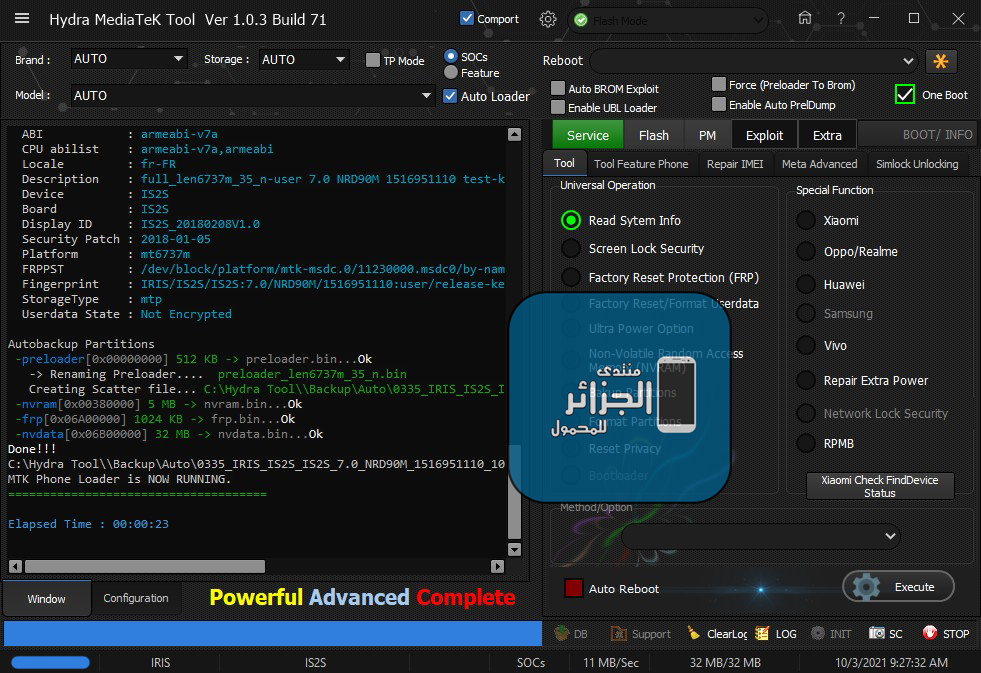
Reading System Info
Brand : IRIS
Vendor : IRIS
Model : IS2S
ID : NRD90M
SDK : 24
Release : 7.0
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : fr-FR
Description : full_len6737m_35_n-user 7.0 NRD90M 1516951110 test-keys
Device : IS2S
Board : IS2S
Display ID : IS2S_20180208V1.0
Security Patch : 2018-01-05
Platform : mt6737m
FRPPST : /dev/block/platform/mtk-msdc.0/11230000.msdc0/by-name/frp
Fingerprint : IRIS/IS2S/IS2S:7.0/NRD90M/1516951110:user/release-keys
StorageType : mtp
Userdata State : Not Encrypted
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition... [Ok]
Safeformat Universal...(tmp.bin)512 Bytes Ok
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:04
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Samsung Galaxy J4+ (SM-J415F) Remove FRP ADB Mode
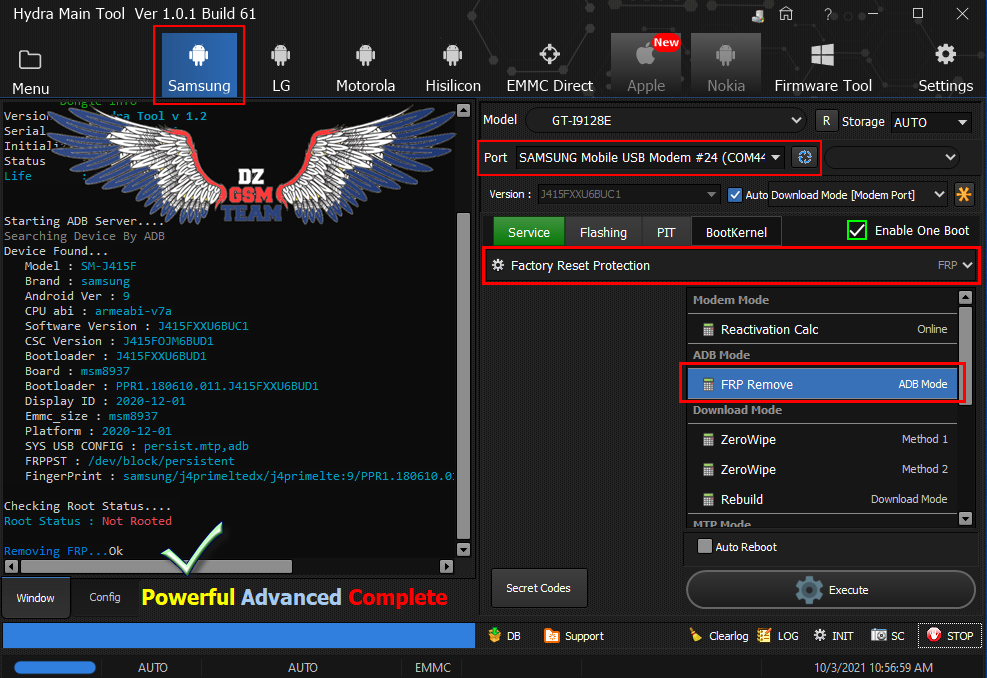
Samsung Galaxy J4+ (SM-J415F) Remove FRP ADB Mode

كود:
[B][FONT=Arial Black][SIZE=2]Starting ADB Server....
Searching Device By ADB
Device Found...
Model : SM-J415F
Brand : samsung
Android Ver : 9
CPU abi : armeabi-v7a
Software Version : J415FXXU6BUC1
CSC Version : J415FOJM6BUD1
Bootloader : J415FXXU6BUD1
Board : msm8937
Bootloader : PPR1.180610.011.J415FXXU6BUD1
Display ID : 2020-12-01
Emmc_size : msm8937
Platform : 2020-12-01
SYS USB CONFIG : persist.mtp,adb
FRPPST : /dev/block/persistent
FingerPrint : samsung/j4primeltedx/j4primelte:9/PPR1.180610.011/J415FXXU6BUD1:user/release-keys
Checking Root Status....
Root Status : Not Rooted
Removing FRP...Ok
[/SIZE][/FONT][/B]mounirblidaa
عضو أساسي
رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
motorola G4 _ xt1622 Remove frp 7.0
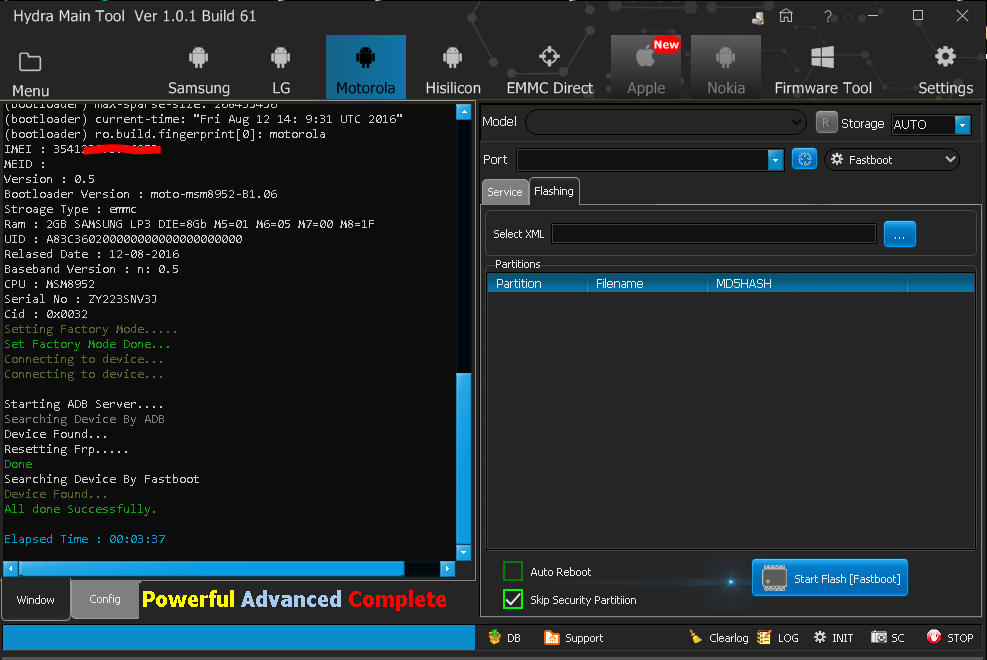
motorola G4 _ xt1622 Remove frp 7.0

رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
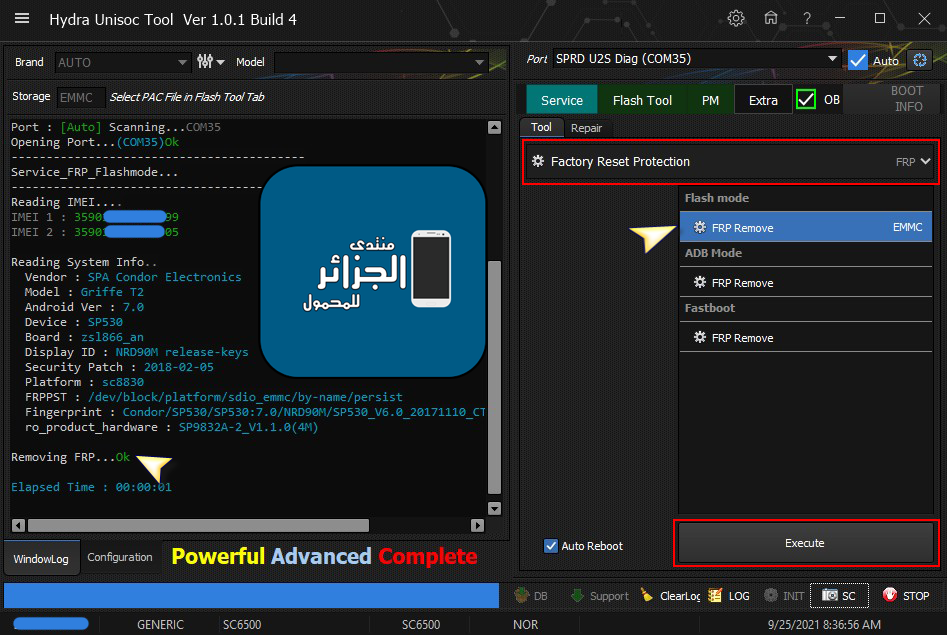
Redmi 9A (dandelion) ZeroWipe FRP Done
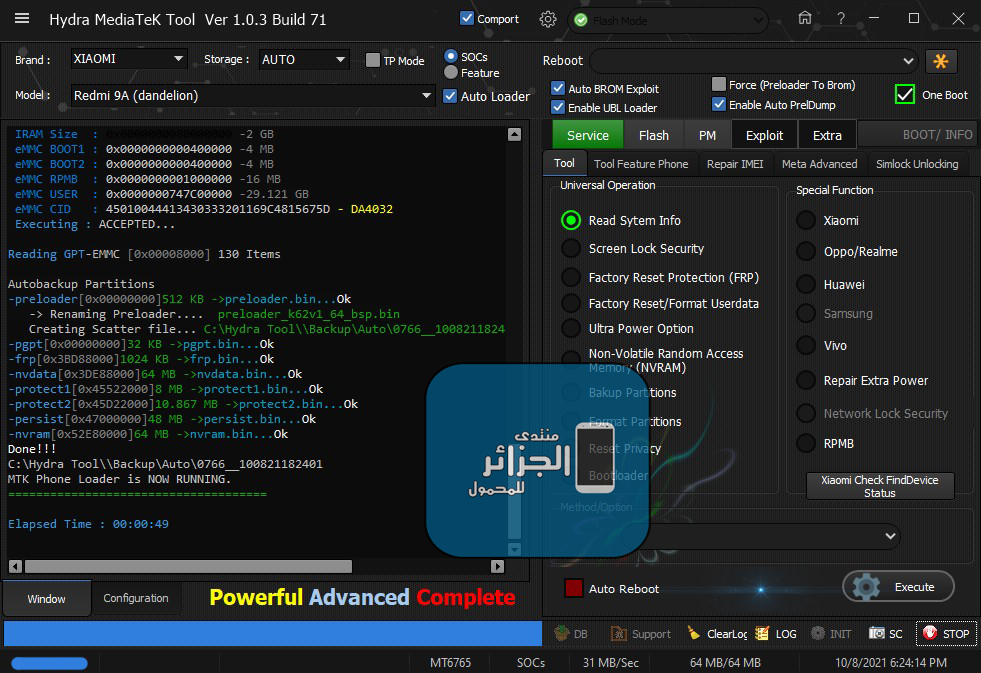
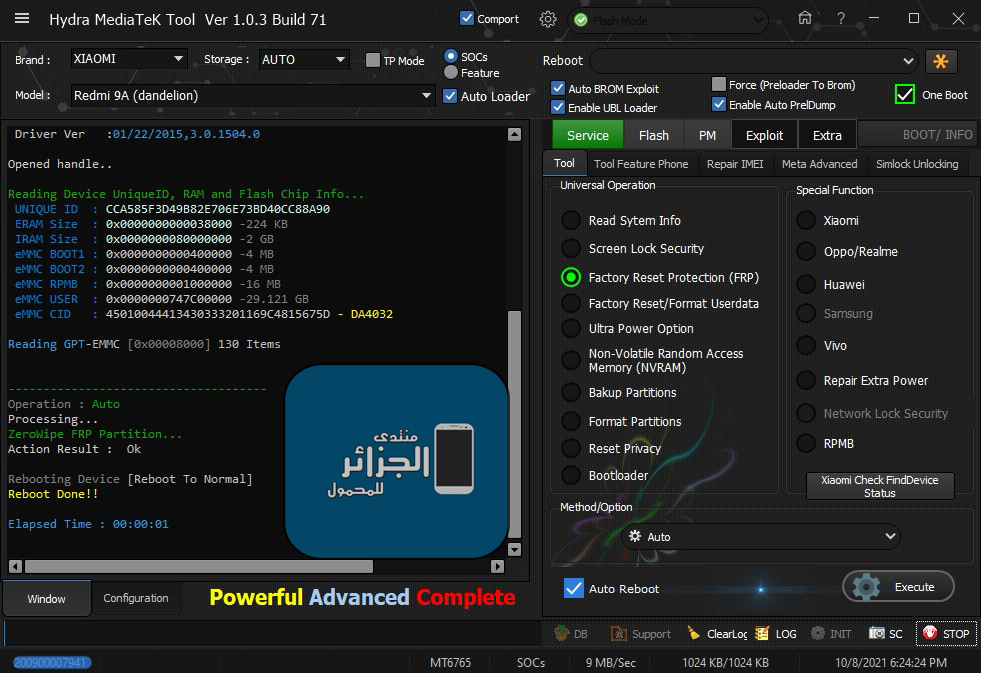
Redmi 9A (dandelion) ZeroWipe FRP Done


كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1633 (COM21)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : CCA585F3D49B82E706E73BD40CC88A90
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 45010044413430333201169C4815675D - DA4032
Reading GPT-EMMC [0x00008000] 130 Items
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition...
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:01
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Starlight C Note Pro (Touch and Red Writing) Problem
هاتف Starlight C Note Pro مشكل التاتش و الكتابة الحمراء
الزبون محتاج بياناته صور و فيديوهات
تم سحب ملف userdata بحجم 26.34 جيقا باستخدام Hydra
تفليش الهاتف بفلاشة لحل مشكل التاتش و الكتابة الحمراء باستخدام SP Flash Tool
ارجاع ملف Userdata للهاتف باستخدام Hydra
[/SIZE][/FONT][/B]
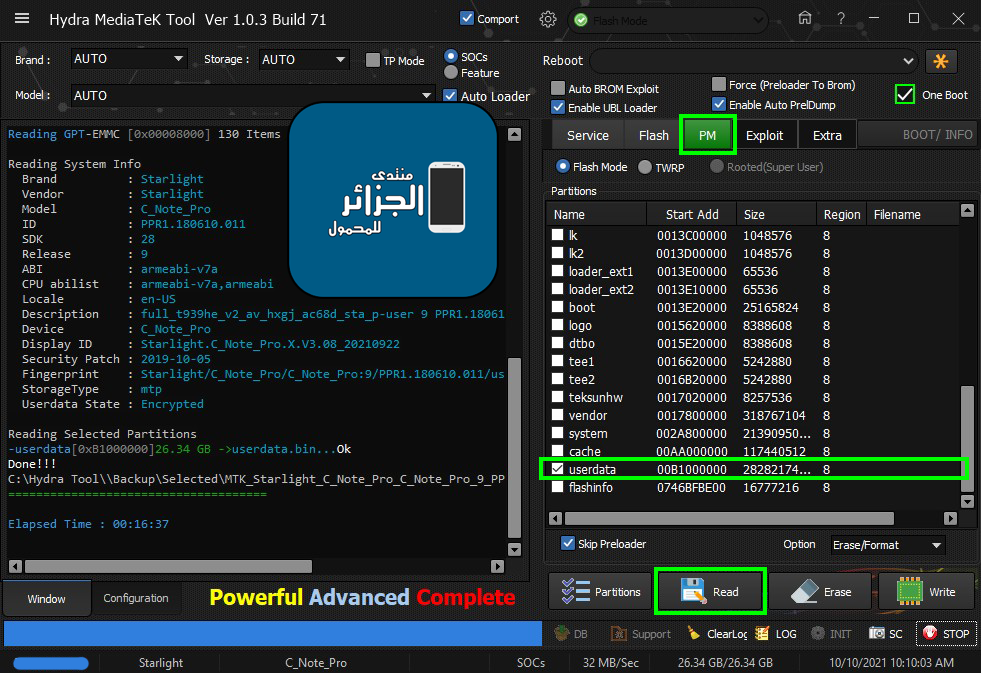
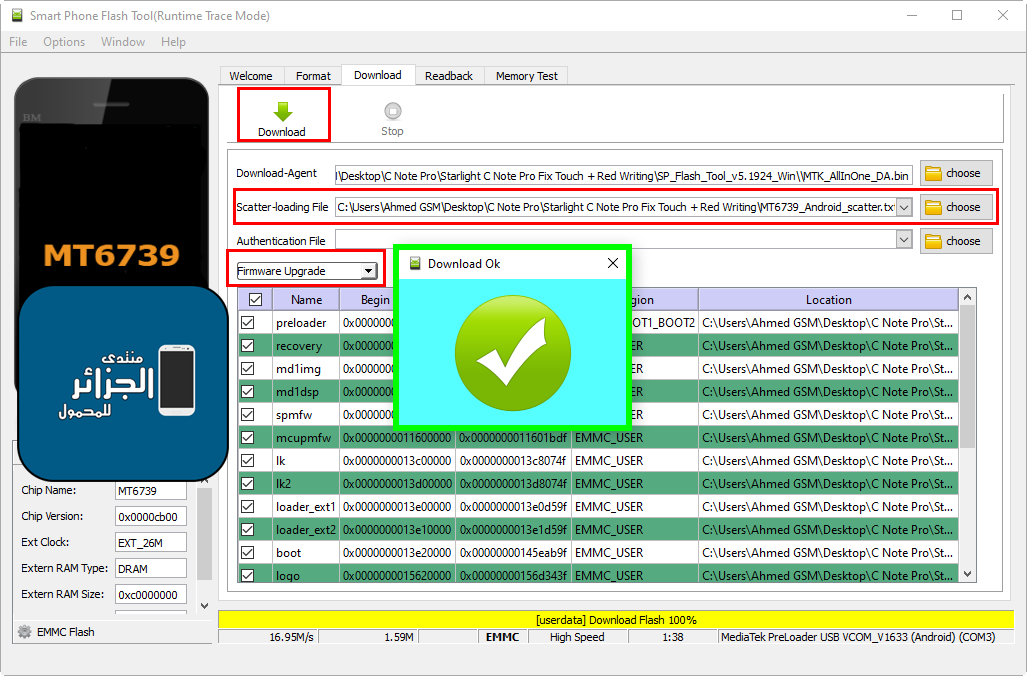
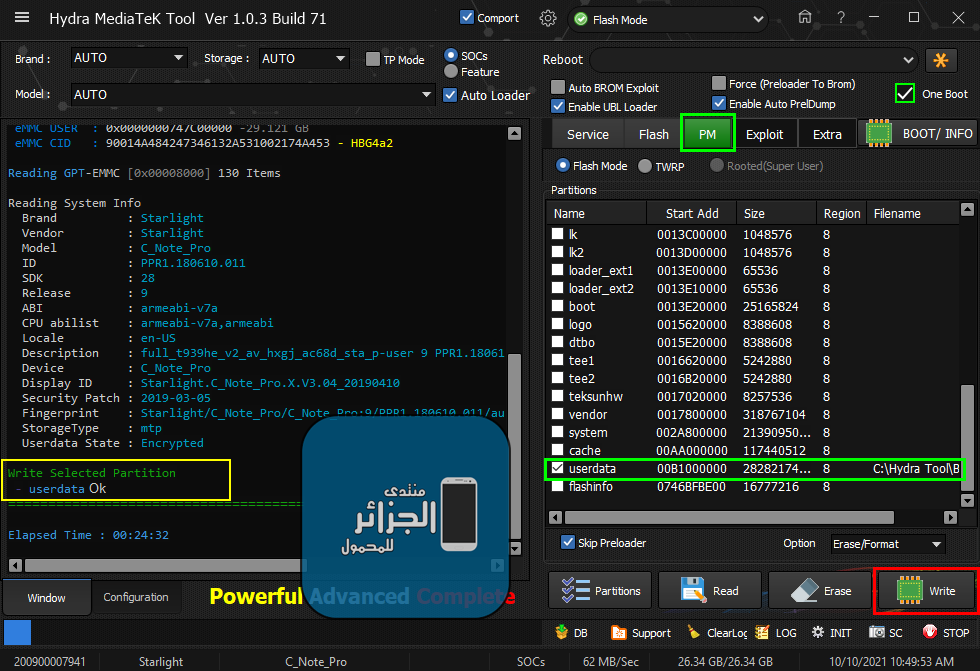
Starlight C Note Pro (Touch and Red Writing) Problem
هاتف Starlight C Note Pro مشكل التاتش و الكتابة الحمراء
الزبون محتاج بياناته صور و فيديوهات
تم سحب ملف userdata بحجم 26.34 جيقا باستخدام Hydra
تفليش الهاتف بفلاشة لحل مشكل التاتش و الكتابة الحمراء باستخدام SP Flash Tool
ارجاع ملف Userdata للهاتف باستخدام Hydra
[/SIZE][/FONT][/B]
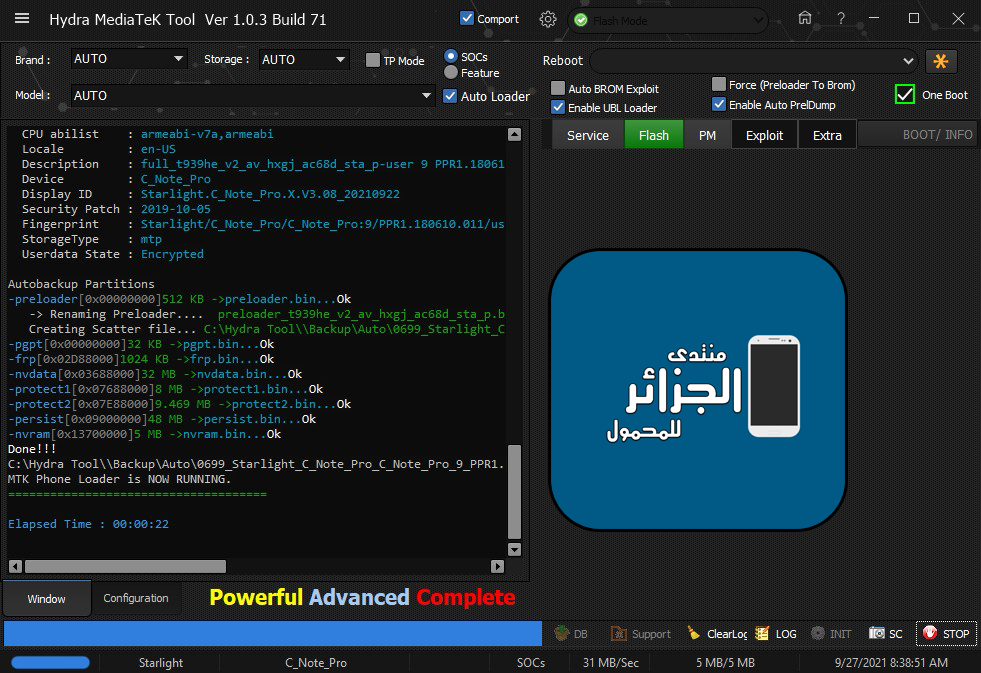
Backup Userdata (26.34 GB)

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1633 (Android) (COM3)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 90DC0726B45209A5B980D14C386F1531
ERAM Size : 0x0000000000020000 -128 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 90014A484247346132A531002174A453 - HBG4a2
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Brand : Starlight
Vendor : Starlight
Model : C_Note_Pro
ID : PPR1.180610.011
SDK : 28
Release : 9
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-US
Description : full_t939he_v2_av_hxgj_ac68d_sta_p-user 9 PPR1.180610.011 eng.user.20210922.221112 release-keys
Device : C_Note_Pro
Display ID : Starlight.C_Note_Pro.X.V3.08_20210922
Security Patch : 2019-10-05
Fingerprint : Starlight/C_Note_Pro/C_Note_Pro:9/PPR1.180610.011/user09222210:user/release-keys
StorageType : mtp
Userdata State : Encrypted
[COLOR="#FF0000"]Reading Selected Partitions
-userdata[0xB1000000]26.34 GB ->userdata.bin...Ok
Done!!!
[/COLOR]C:\Hydra Tool\\Backup\Selected\MTK_Starlight_C_Note_Pro_C_Note_Pro_9_PPR1.180610.011_user09222210_101021095329
=====================================
[COLOR="#008000"]Elapsed Time : 00:16:37
[/COLOR][/SIZE][/FONT][/B]Flash Firmware To (Fix Touch + Red Writing) With SP Flash Tool

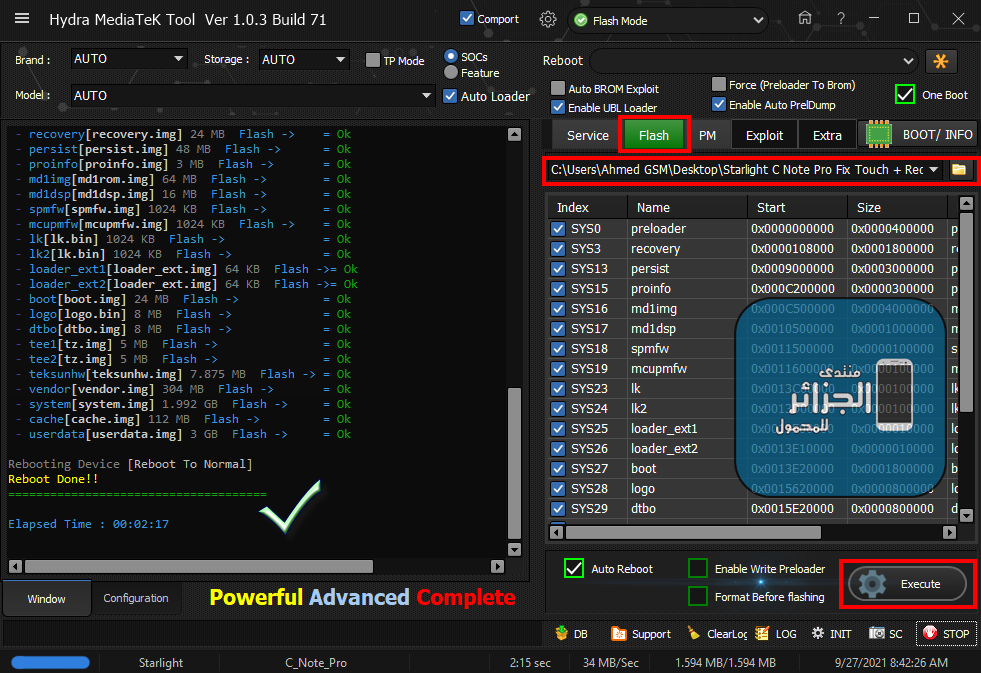
Write Backup Userdata (26.34 GB)

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1633 (Android) (COM3)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 90DC0726B45209A5B980D14C386F1531
ERAM Size : 0x0000000000020000 -128 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 90014A484247346132A531002174A453 - HBG4a2
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Brand : Starlight
Vendor : Starlight
Model : C_Note_Pro
ID : PPR1.180610.011
SDK : 28
Release : 9
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-US
Description : full_t939he_v2_av_hxgj_ac68d_sta_p-user 9 PPR1.180610.011 eng.autoft.20190410.191855 release-keys
Device : C_Note_Pro
Display ID : Starlight.C_Note_Pro.X.V3.04_20190410
Security Patch : 2019-03-05
Fingerprint : Starlight/C_Note_Pro/C_Note_Pro:9/PPR1.180610.011/autoftp04101917:user/release-keys
StorageType : mtp
Userdata State : Encrypted
[COLOR="#FF0000"]Write Selected Partition
- userdata Ok
[/COLOR]=====================================
[COLOR="#008000"]Elapsed Time : 00:24:32
[/COLOR][/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
STREAM B2Plus HT28 ZeroWipe FRP
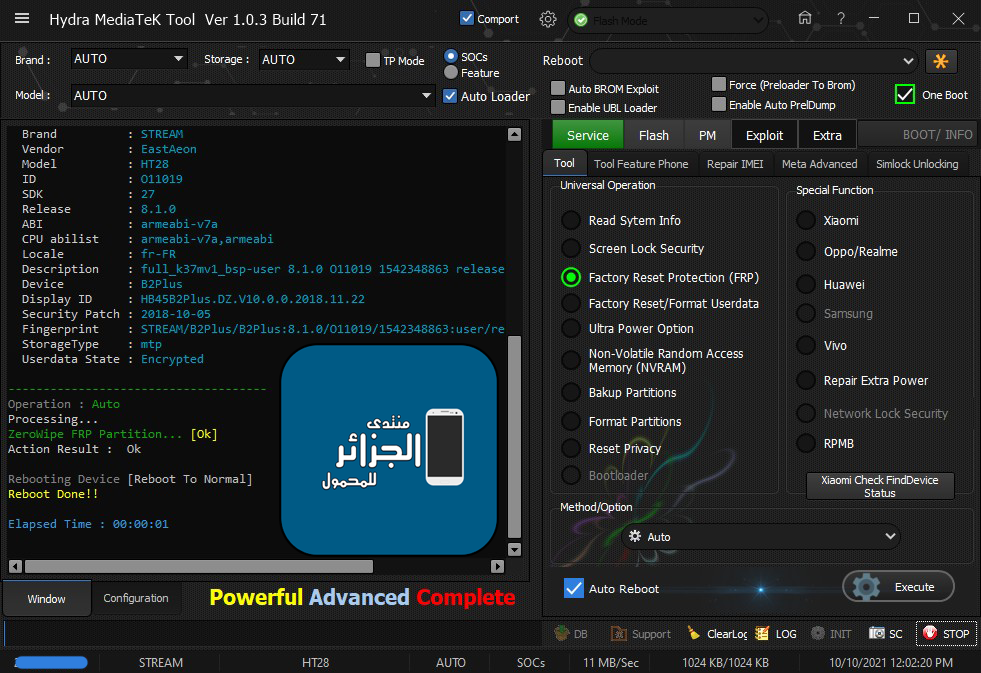
STREAM B2Plus HT28 ZeroWipe FRP

كود:
[B][FONT=Arial Black][SIZE=2]Searching for MTK Device...Found
Port Identification :DA_HIGHSPEED_VCOM
FriendlyName :MediaTek DA USB VCOM (Android) (COM4)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2001#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Opened handle..
Reading System Info
Brand : STREAM
Vendor : EastAeon
Model : HT28
ID : O11019
SDK : 27
Release : 8.1.0
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : fr-FR
Description : full_k37mv1_bsp-user 8.1.0 O11019 1542348863 release-keys
Device : B2Plus
Display ID : HB45B2Plus.DZ.V10.0.0.2018.11.22
Security Patch : 2018-10-05
Fingerprint : STREAM/B2Plus/B2Plus:8.1.0/O11019/1542348863:user/release-keys
StorageType : mtp
Userdata State : Encrypted
-------------------------------------
Operation : Auto
Processing...
[COLOR="#FF0000"]ZeroWipe FRP Partition... [Ok]
Action Result : Ok
[/COLOR]
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:01
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Samsung Galaxy A11 (SM-A115F) Removing FRP [Zero Wipe]
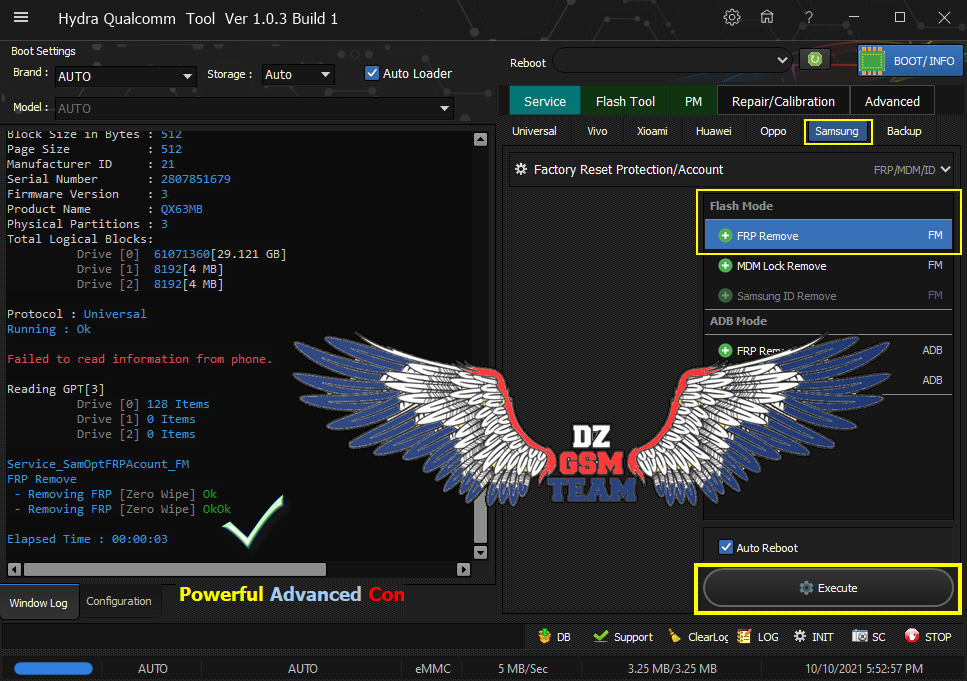
Samsung Galaxy A11 (SM-A115F) Removing FRP [Zero Wipe]

كود:
[B][FONT=Arial Black][SIZE=2]PreOperation Configuration
Brand : AUTO Model : AUTO Storage : Auto
Loader: Auto
Port : Auto
Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM5)
SymbolicName :\??\USB#VID_05C6&PID_9008#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :08/31/2015,2.1.2.0
Getting device info..Ok
Device MODE : Firehose
Connecting to Firehose...
Ping.. Ok
Configuration......
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8953
Version : 1
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 21
Serial Number : 2807851679
Firmware Version : 3
Product Name : QX63MB
Physical Partitions : 3
Total Logical Blocks:
Drive [0] 61071360[29.121 GB]
Drive [1] 8192[4 MB]
Drive [2] 8192[4 MB]
Protocol : Universal
Running : Ok
Failed to read information from phone.
Reading GPT[3]
Drive [0] 128 Items
Drive [1] 0 Items
Drive [2] 0 Items
[COLOR="#FF0000"]Service_SamOptFRPAcount_FM
FRP Remove
- Removing FRP [Zero Wipe] Ok
- Removing FRP [Zero Wipe] OkOk
[/COLOR]
Elapsed Time : 00:00:03
[/SIZE][/FONT][/B]
رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Stream B1S Safe Format Done
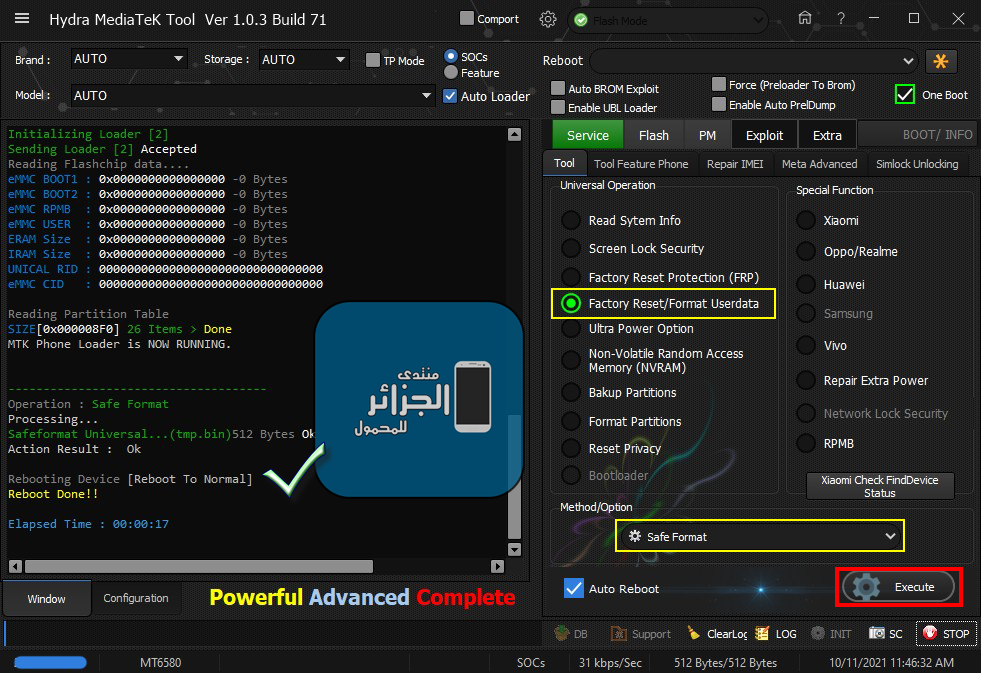
Stream B1S Safe Format Done

كود:
[B][FONT=Arial Black][SIZE=2]=====================================
Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1633 (Android) (COM3)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 6580MT6580 [6580]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
FUSEID : 02100040
FUSEID : 02100040
SECURE VERSION : 00
BL VERSION : 01
Preparing Download Agent..
DA : 6580.bin
Agent: MTK_DOWNLOAD_AGENT -HYDRA
Ver : MTK_AllInOne_DA_v3.3001.2020-11-03.22:07_536568
Init : Loader [1]
Sending : Accepted
Identifying Protocol...
Protocol : Old
C4 - eMMC
0007
0000000000000000000000000000
PRMMCCID : 700100543232373038010F1209FF9537
Init Configuration
Running DA 4.2 on BBID : 0x00 Ok
Initializing Loader [2]
Sending Loader [2] Accepted
Reading Flashchip data....
eMMC BOOT1 : 0x0000000000000000 -0 Bytes
eMMC BOOT2 : 0x0000000000000000 -0 Bytes
eMMC RPMB : 0x0000000000000000 -0 Bytes
eMMC USER : 0x0000000000000000 -0 Bytes
ERAM Size : 0x0000000000000000 -0 Bytes
IRAM Size : 0x0000000000000000 -0 Bytes
UNICAL RID : 00000000000000000000000000000000
eMMC CID : 00000000000000000000000000000000
Reading Partition Table
SIZE[0x000008F0] 26 Items > Done
MTK Phone Loader is NOW RUNNING.
-------------------------------------
[COLOR="#FF0000"]Operation : Safe Format
Processing...
Safeformat Universal...(tmp.bin)512 Bytes Ok
Action Result : Ok
[/COLOR]
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:17
[/SIZE][/FONT][/B]رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Xiaomi Redmi Note 5 (Whyred) Ultra Power
Removing FRP [Zero Wipe] + Formatting Userdata [Safe Format - eMMc]
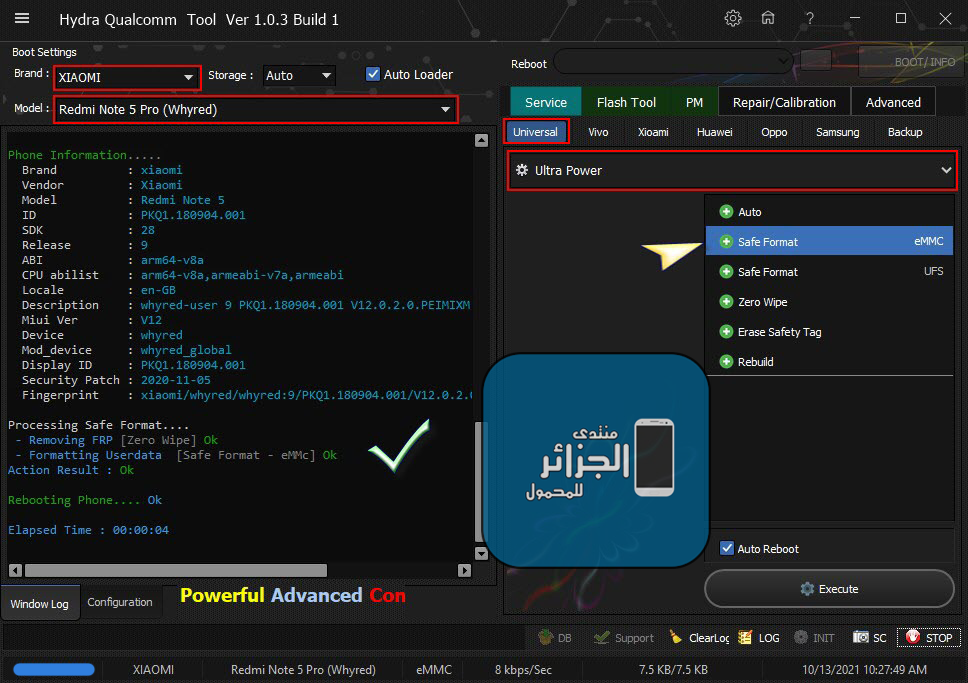
Xiaomi Redmi Note 5 (Whyred) Ultra Power
Removing FRP [Zero Wipe] + Formatting Userdata [Safe Format - eMMc]

كود:
[B][FONT=Arial Black][SIZE=2]PreOperation Configuration
Brand : XIAOMI Model : Redmi Note 5 Pro (Whyred) Storage : Auto
Loader: mi_2_9.elf
Port : Auto
Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM5)
SymbolicName :\??\USB#VID_05C6&PID_9008#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :08/31/2015,2.1.2.0
Getting device info..Ok
Device MODE : Firehose
Connecting to Firehose...
Ping...... Ok
Configuration......
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : MSM8996
Version : 1
DateTime : Aug 2 2018 - 22:27:53
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 21
Serial Number : 2676665404
Firmware Version : 2
Product Name : DD68MB
Physical Partitions : 4
Total Logical Blocks:
Drive [0] 61071360[29.121 GB]
Drive [1] 8192[4 MB]
Drive [2] 8192[4 MB]
Drive [3] 8192[4 MB]
Protocol : Universal
Running : Ok
Reading GPT[4]
Drive [0] 64 Items
Drive [1] 0 Items
Drive [2] 0 Items
Drive [3]
Phone Information.....
Brand : xiaomi
Vendor : Xiaomi
Model : Redmi Note 5
ID : PKQ1.180904.001
SDK : 28
Release : 9
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-GB
Description : whyred-user 9 PKQ1.180904.001 V12.0.2.0.PEIMIXM release-keys
Miui Ver : V12
Device : whyred
Mod_device : whyred_global
Display ID : PKQ1.180904.001
Security Patch : 2020-11-05
Fingerprint : xiaomi/whyred/whyred:9/PKQ1.180904.001/V12.0.2.0.PEIMIXM:user/release-keys
Processing Safe Format....
[COLOR="#008000"] - Removing FRP [Zero Wipe] Ok
- Formatting Userdata [Safe Format - eMMc] Ok
Action Result : Ok
[/COLOR]
Rebooting Phone.... Ok
Elapsed Time : 00:00:04
[/SIZE][/FONT][/B]