- إنضم
- 16 سبتمبر 2012
- المشاركات
- 3,136
- مستوى التفاعل
- 2,975
- النقاط
- 113
كود:
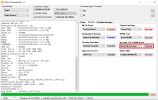
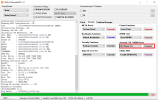
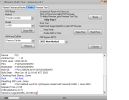
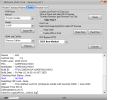
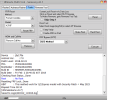
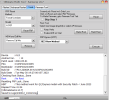
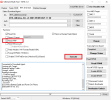
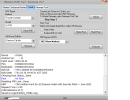
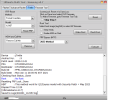
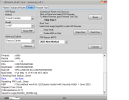
Brand/Model : *Auto* / *Auto Detect*
Operation : Reset Mi Account
Waiting for Device...Found
Port : MediaTek USB Port_V1633 (COM46)
Device Path : \\?\usb#vid_0e8d&pid_0003#5&21e739f&0&3#{86e0d1e0-8089-11d0-9ce4-08003e301f73}
Driver : MediaTek Inc., 3.0.1504.0 [usb2ser.sys]
Mode : BROM
Hw ID : MT6768 [0707] Helio P65/G85 k68v1
Details : 8A00,CA00,0000
Sec. Config : [SBA:True] [SLA:True] [DAA:True]
MEID : 4A141BCB8A57FE88B0BA97C3E7CA0BF5
SoC ID[0] : 780B11899DBA5A6D3A1580B14D809023
SoC ID[1] : 37919957490114ABB8D336D5DFE2604C
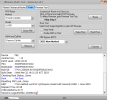
Running Exploit...Done
Downloading Preloader...OK
Saved as : preloader_merlin.bin
Loading EMI Config from Preloader...OK
Sec. Config : [SBA:False] [SLA:False] [DAA:False]
Using Internal DA!
DA Security Patched
Sending 1st DA...OK
Jump DA Address...OK
Syncing...OK
Checksum Level is Storage
Connection : brom
Speed : HIGH-SPEED
Reading RAM Configuration...OK
Reading EMI Configuration...OK
CID : 15010044563644414202231CDC0D37CB [EMMC]
Initializing Storage...OK
Sending 2nd DA...OK
Initialize DA Extension...OK
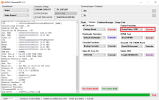
Int. RAM : 0x0000000000070000 [448.00 KB]
Ext. RAM : 0x0000000100000000 [4.00 GB]
Flash ID : DV6DAB
CID : 15010044563644414202231CDC0D37CB
BOOT1 : 0x0000000000400000 [4.00 MB]
BOOT2 : 0x0000000000400000 [4.00 MB]
RPMB : 0x0000000001000000 [16.00 MB]
USERAREA : 0x0000001D1EC00000 [116.48 GB]
PRE EOL : NORMAL
Life. Est.A : 0%-10% LIFE TIME USED
Life. Est.B : 0%-10% LIFE TIME USED
Reading Partition Table...OK
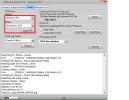
Manuf. : Xiaomi
And. Ver. : 11
Build Dt. : Wed Jul 28 21:03:41 CST 2021
Display ID : RP1A.200720.011
Ver. Inc. : V12.5.1.0.RJOMIXM
Locale : en-GB
Mod. Dev. : merlin_global
Patch : 2021-07-01
Bootloader : UNLOCKED
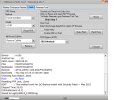
Reading Data...OK
Backup : Persist_Xiaomi_unknown_20240304_114006.zip
Resetting Mi Account Data...OK
Formatting Userdata (Safe Mode)...OKOK
Operation Finished.
[UltimateMTK2 v1.1]
Log Saved : 20240304_114017.log