تثبيت التطبيق
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
ملاحظة: This feature may not be available in some browsers.
أنت تستخدم أحد المتصفحات القديمة. قد لا يتم عرض هذا الموقع أو المواقع الأخرى بشكل صحيح.
يجب عليك ترقية متصفحك أو استخدام أحد المتصفحات البديلة.
يجب عليك ترقية متصفحك أو استخدام أحد المتصفحات البديلة.
تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
- بادئ الموضوع DZ-Developer
- تاريخ البدء
رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
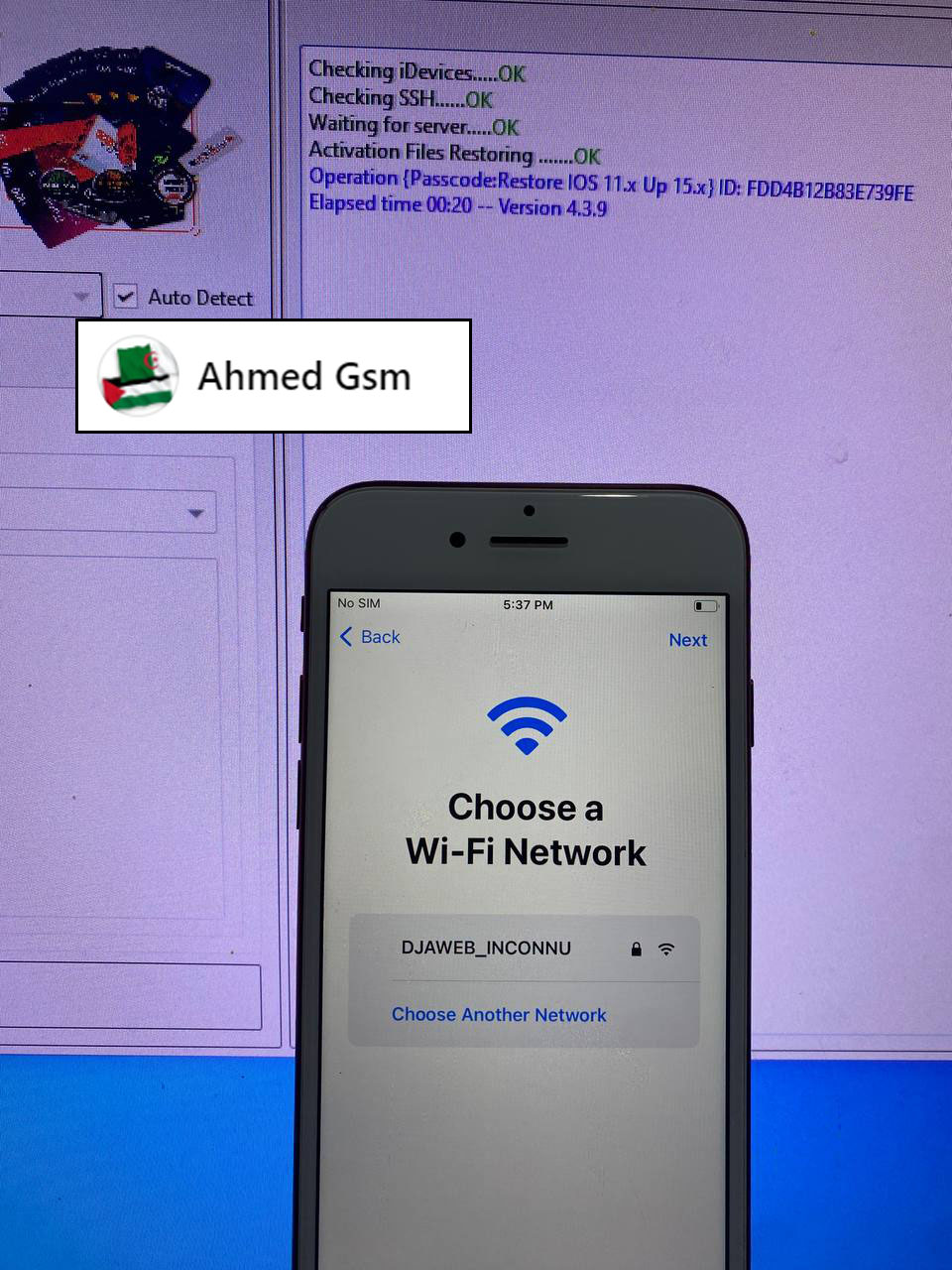
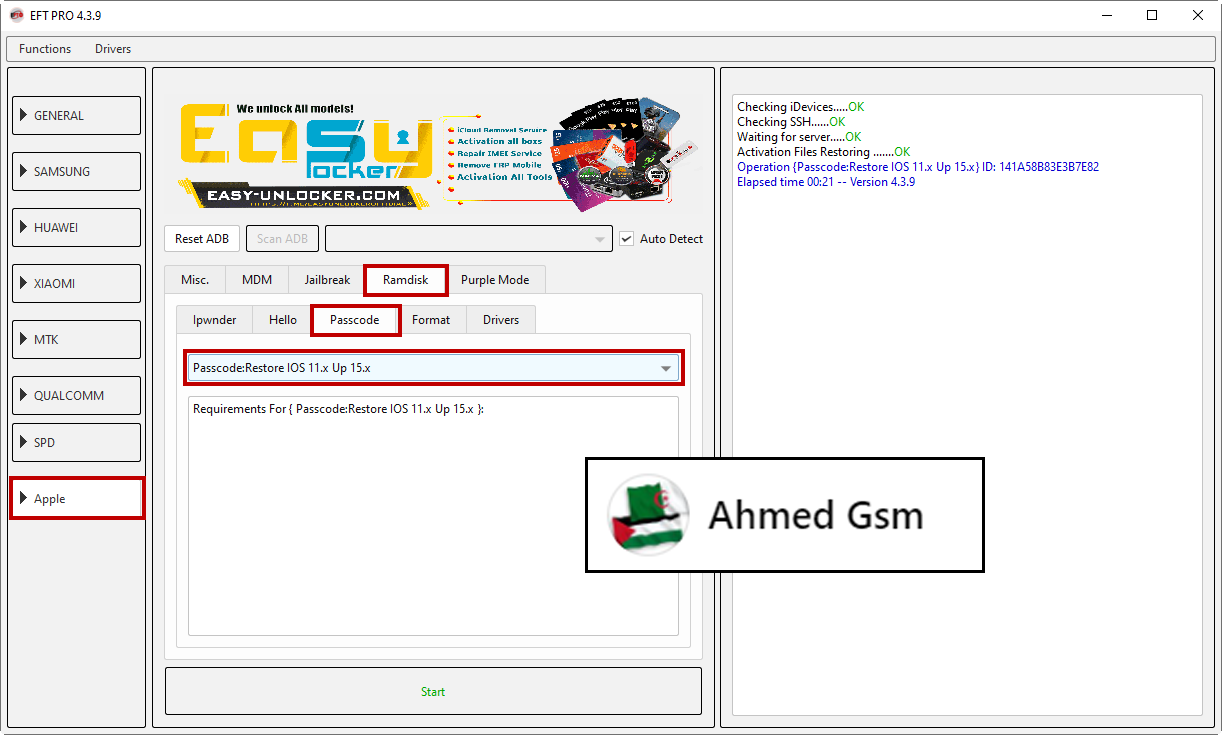
IPHONE 6s
IOS 15.7.1
BYPASS PASSCODE (WITH SIGNAL)
DONE BY EFT PRO 4.3.9
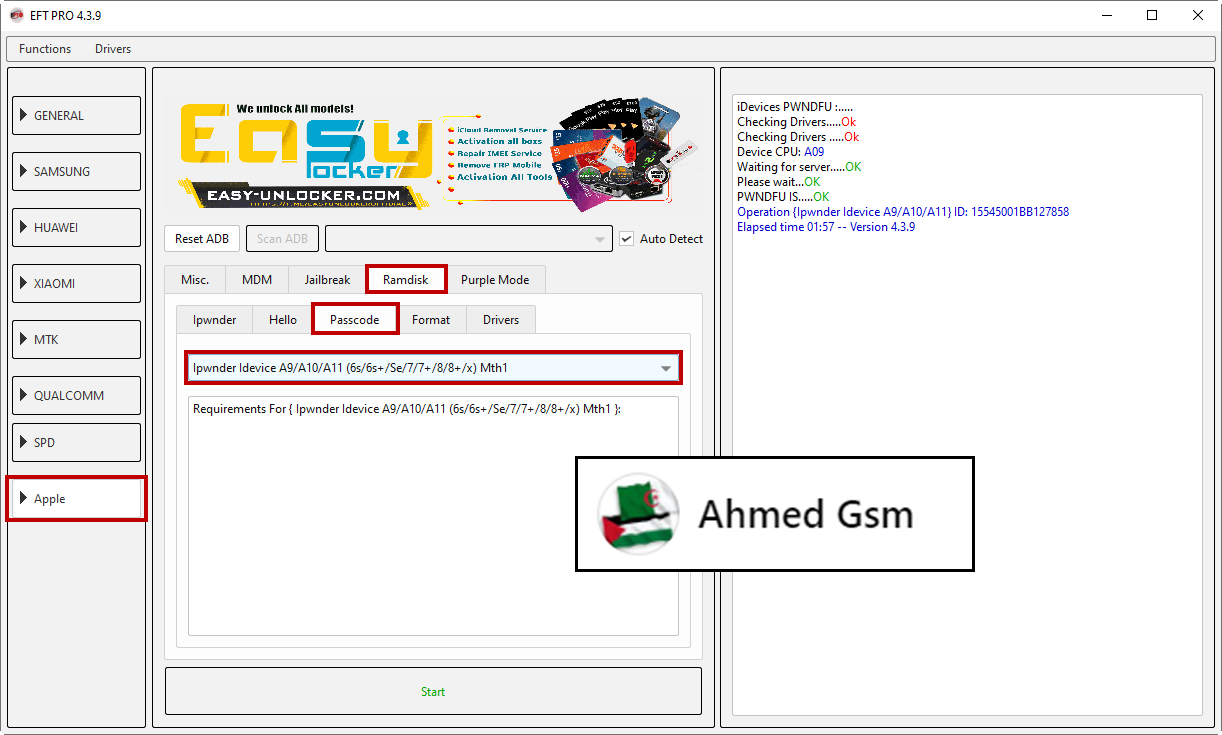
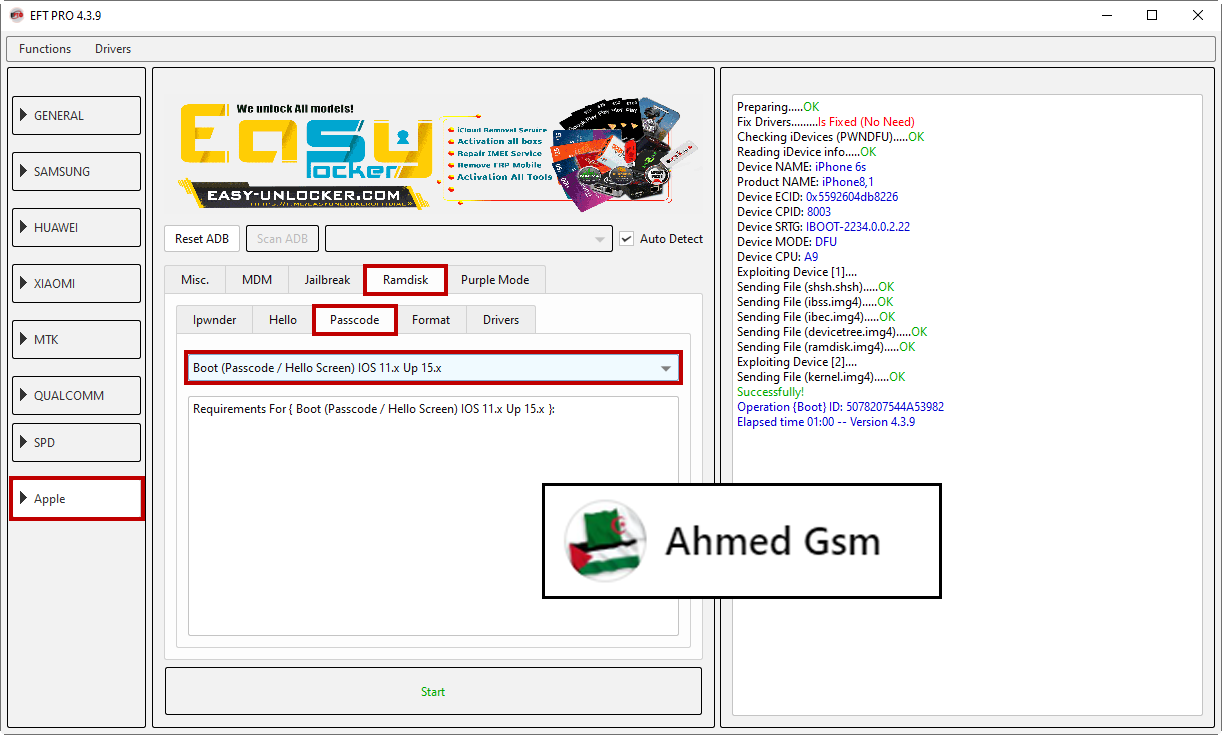
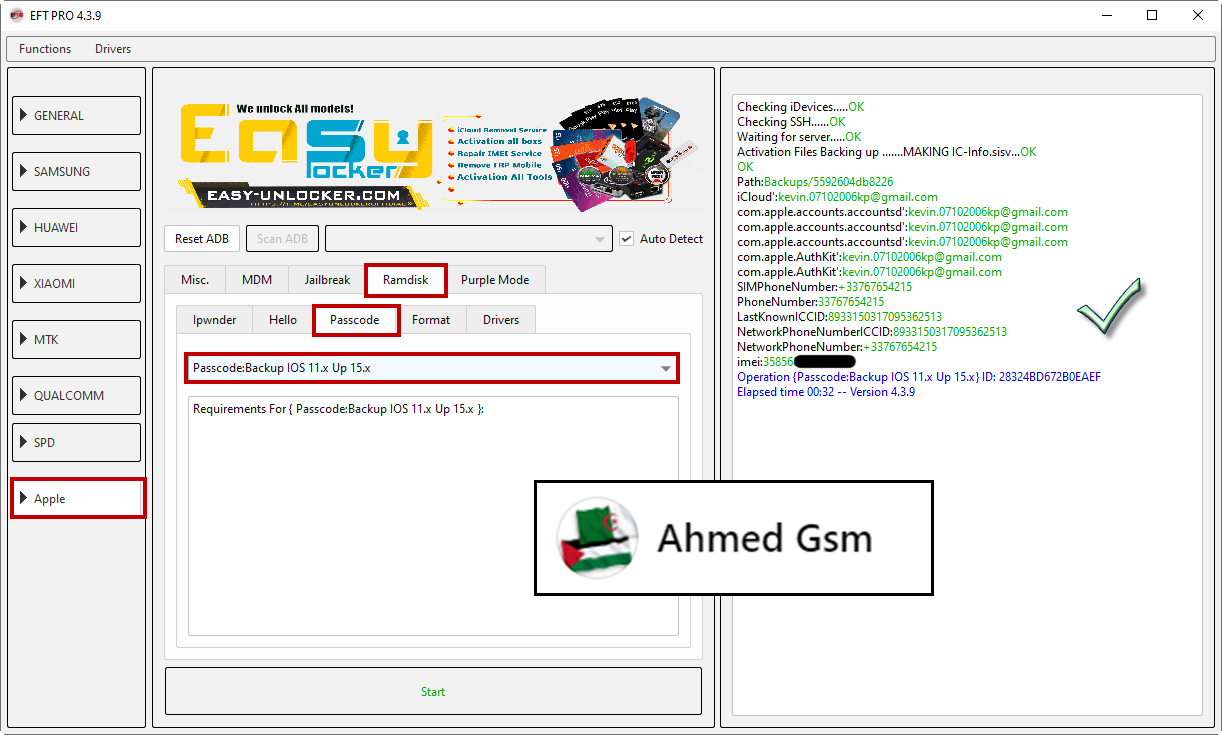
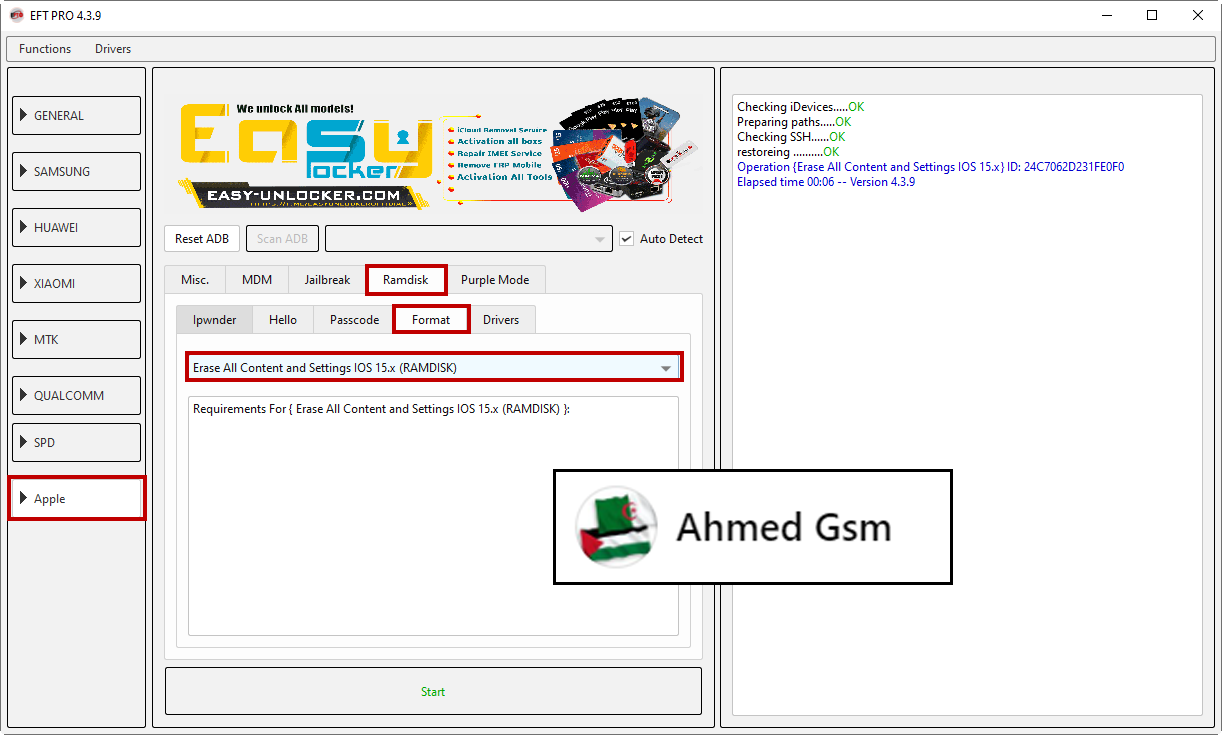
IPHONE 6s
IOS 15.7.1
BYPASS PASSCODE (WITH SIGNAL)
DONE BY EFT PRO 4.3.9

كود:
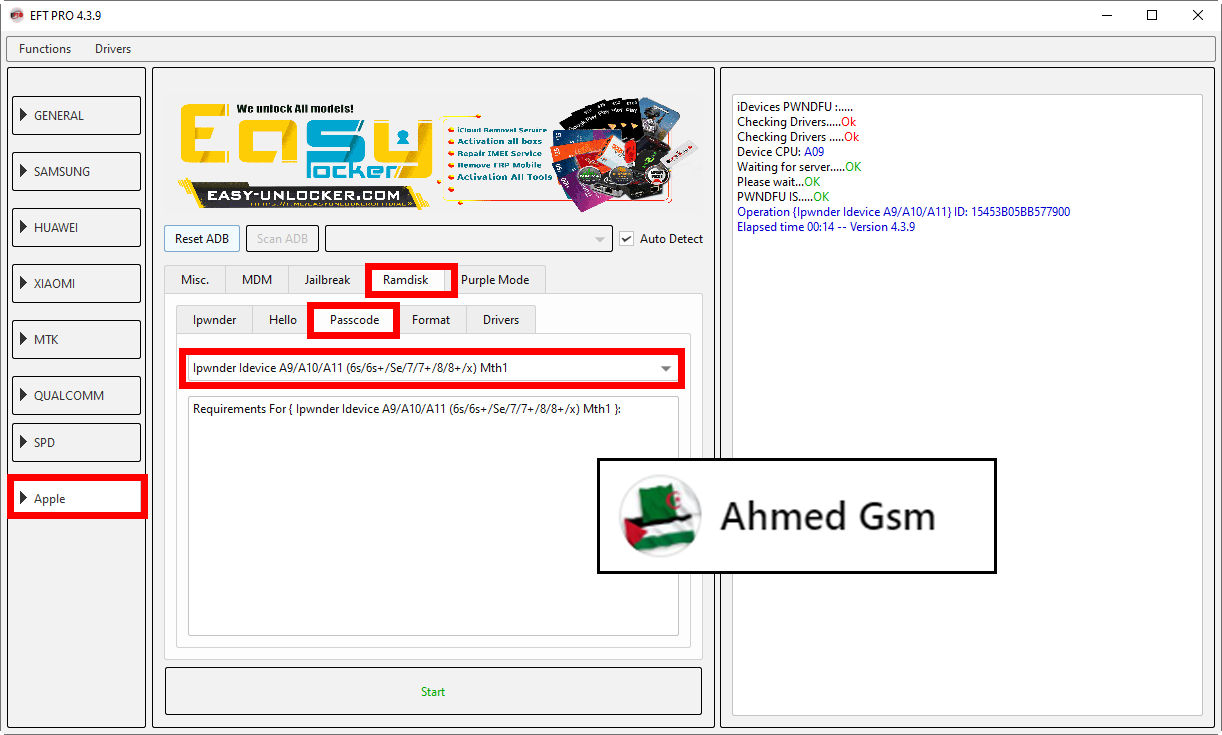
[B][FONT=Arial Black]iDevices PWNDFU :.....
Checking Drivers.....Ok
Checking Drivers .....Ok
Device CPU: A09
Waiting for server.....OK
Please wait...OK
PWNDFU IS.....OK
Operation {Ipwnder Idevice A9/A10/A11} ID: 15545001BB127858
Elapsed time 01:57 -- Version 4.3.9
[/FONT][/B]
كود:
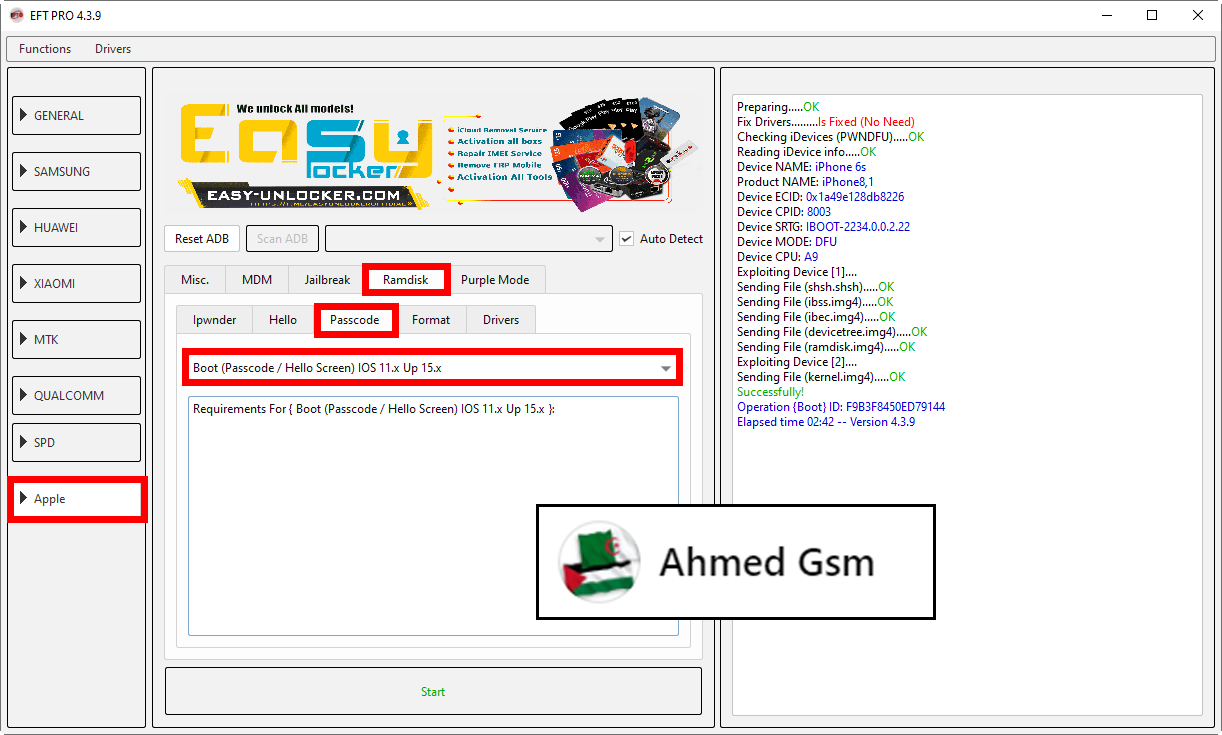
[B][FONT=Arial Black]Preparing.....OK
Fix Drivers.........Is Fixed (No Need)
Checking iDevices (PWNDFU).....OK
Reading iDevice info.....OK
Device NAME: iPhone 6s
Product NAME: iPhone8,1
Device ECID: 0x5592604db8226
Device CPID: 8003
Device SRTG: IBOOT-2234.0.0.2.22
Device MODE: DFU
Device CPU: A9
Exploiting Device [1]....
Sending File (shsh.shsh).....OK
Sending File (ibss.img4).....OK
Sending File (ibec.img4).....OK
Sending File (devicetree.img4).....OK
Sending File (ramdisk.img4).....OK
Exploiting Device [2]....
Sending File (kernel.img4).....OK
Successfully!
Operation {Boot} ID: 5078207544A53982
Elapsed time 01:00 -- Version 4.3.9
[/FONT][/B]
كود:
[B][FONT=Arial Black]Checking iDevices.....OK
Checking SSH......OK
Waiting for server.....OK
Activation Files Backing up .......MAKING IC-Info.sisv...OK
OK
Path:Backups/5592604db8226
iCloud':kevin.07102006kp@gmail.com
com.apple.accounts.accountsd':kevin.07102006kp@gmail.com
com.apple.accounts.accountsd':kevin.07102006kp@gmail.com
com.apple.accounts.accountsd':kevin.07102006kp@gmail.com
com.apple.AuthKit':kevin.07102006kp@gmail.com
com.apple.AuthKit':kevin.07102006kp@gmail.com
SIMPhoneNumber:+33767654215
PhoneNumber:33767654215
LastKnownICCID:8933150317095362513
NetworkPhoneNumberICCID:8933150317095362513
NetworkPhoneNumber:+33767654215
imei:358568XXXXXXX
Operation {Passcode:Backup IOS 11.x Up 15.x} ID: 28324BD672B0EAEF
Elapsed time 00:32 -- Version 4.3.9
[/FONT][/B]
كود:
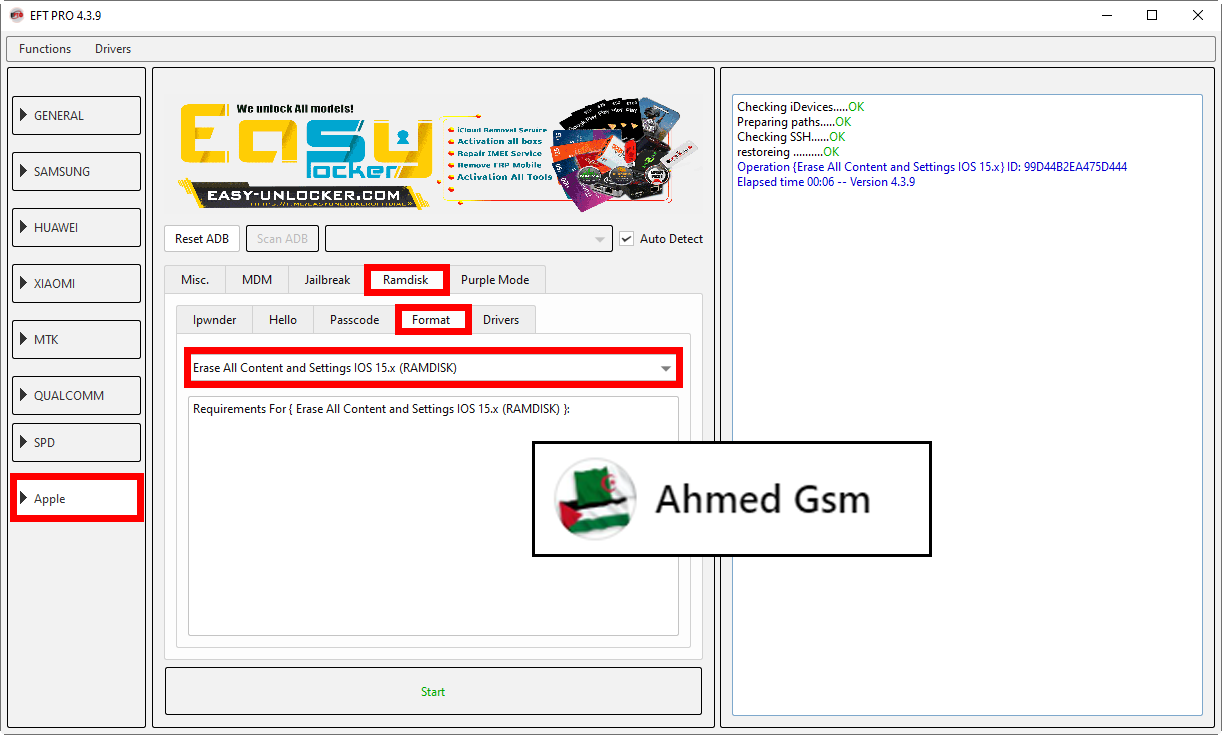
[B][FONT=Arial Black]Checking iDevices.....OK
Preparing paths.....OK
Checking SSH......OK
restoreing ..........OK
Operation {Erase All Content and Settings IOS 15.x} ID: 24C7062D231FE0F0
Elapsed time 00:06 -- Version 4.3.9
[/FONT][/B]
كود:
[B][FONT=Arial Black]Checking iDevices.....OK
Checking SSH......OK
Waiting for server.....OK
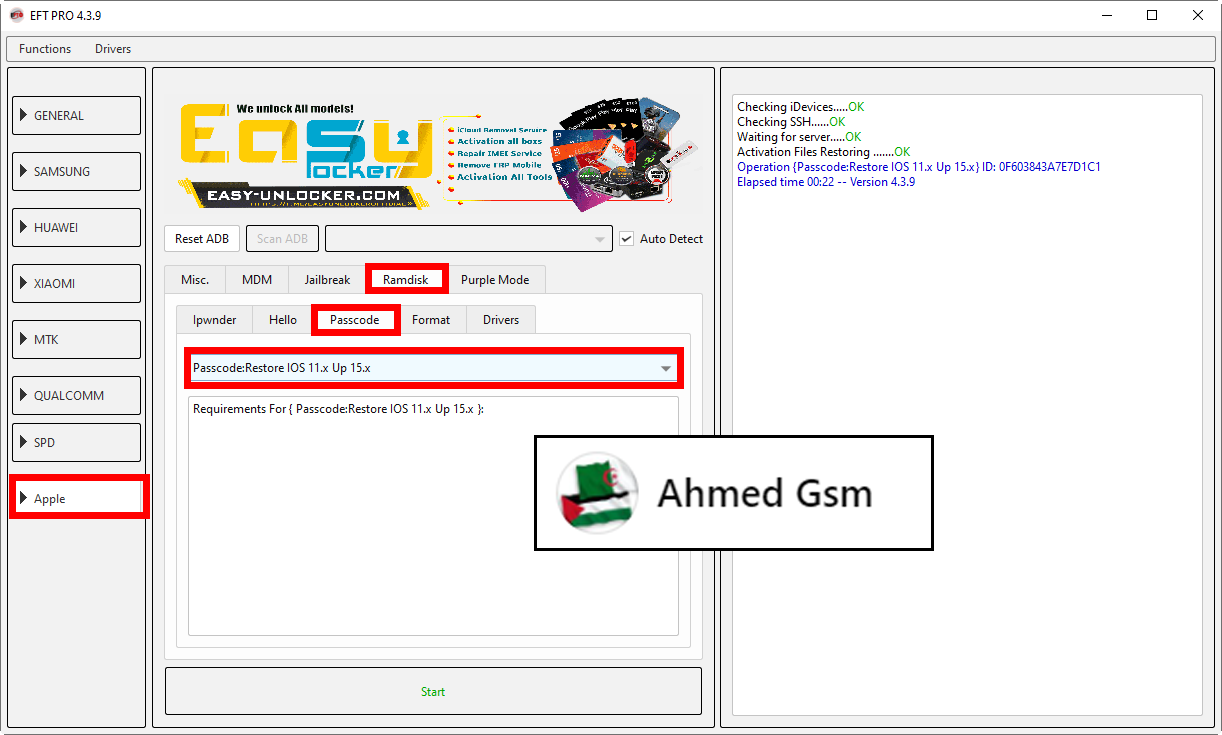
Activation Files Restoring .......OK
Operation {Passcode:Restore IOS 11.x Up 15.x} ID: 141A58B83E3B7E82
Elapsed time 00:21 -- Version 4.3.9
[/FONT][/B]
رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
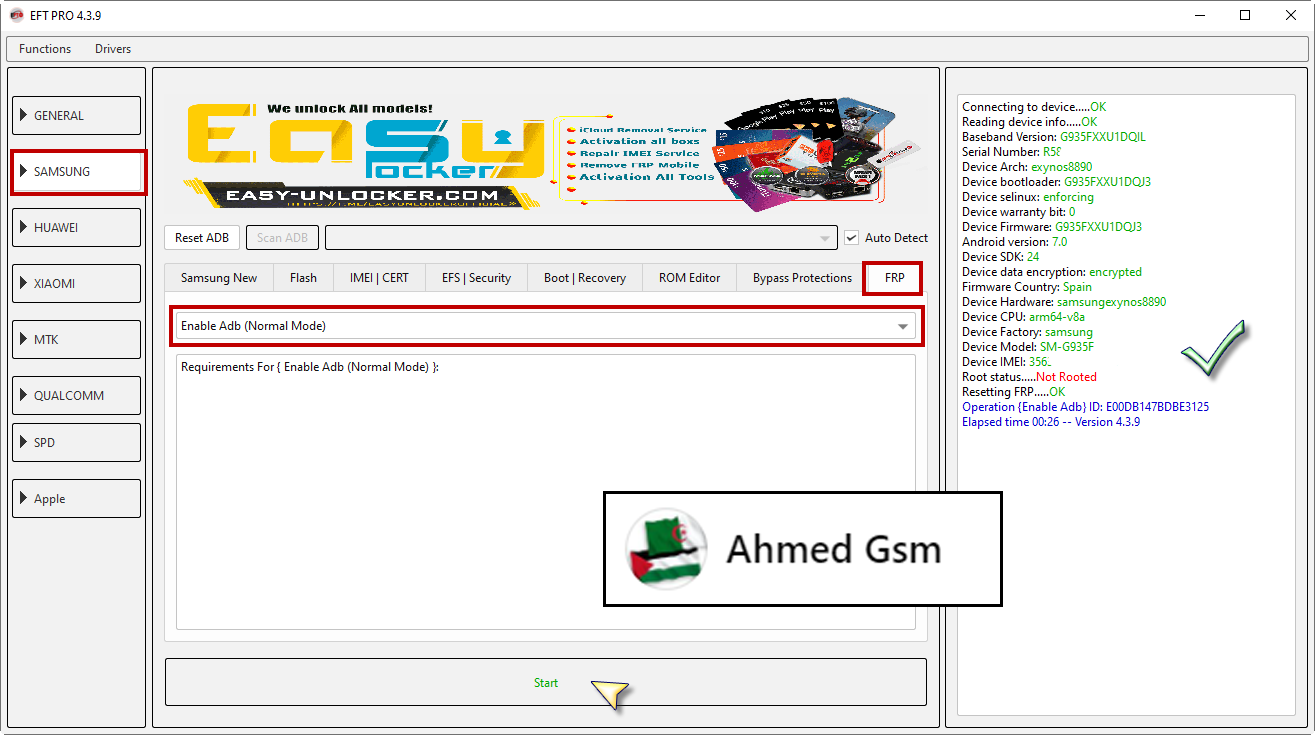
Samsung A20 (SM-A205F) Resetting FRP Done By EFT Pro

Samsung A20 (SM-A205F) Resetting FRP Done By EFT Pro

كود:
[B][FONT=Arial Black]Connecting to device.....OK
Reading device info.....OK
Baseband Version: A205FDDU1ASE1,A205FDDU1ASE1
Serial Number: RZ8XXXXVT
Device Arch: exynos7885
Device bootloader: A205FXXU1ASE4
Device selinux: enforcing
Device warranty bit: 0
Device Firmware: A205FXXU1ASE4
Android version: 9
Device SDK: 28
Device data encryption: encrypted
Firmware Country: UAE
Device Hardware: exynos7885
Device CPU: arm64-v8a
Device Factory: samsung
Device Model: SM-A205F
Device IMEI: 3569XXXXXXXX57
Root status.....Not Rooted
Resetting FRP.....OK
Operation {Enable Adb} ID: 6B1F738F80C3C0AF
Elapsed time 00:24 -- Version 4.3.9
[/FONT][/B]رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
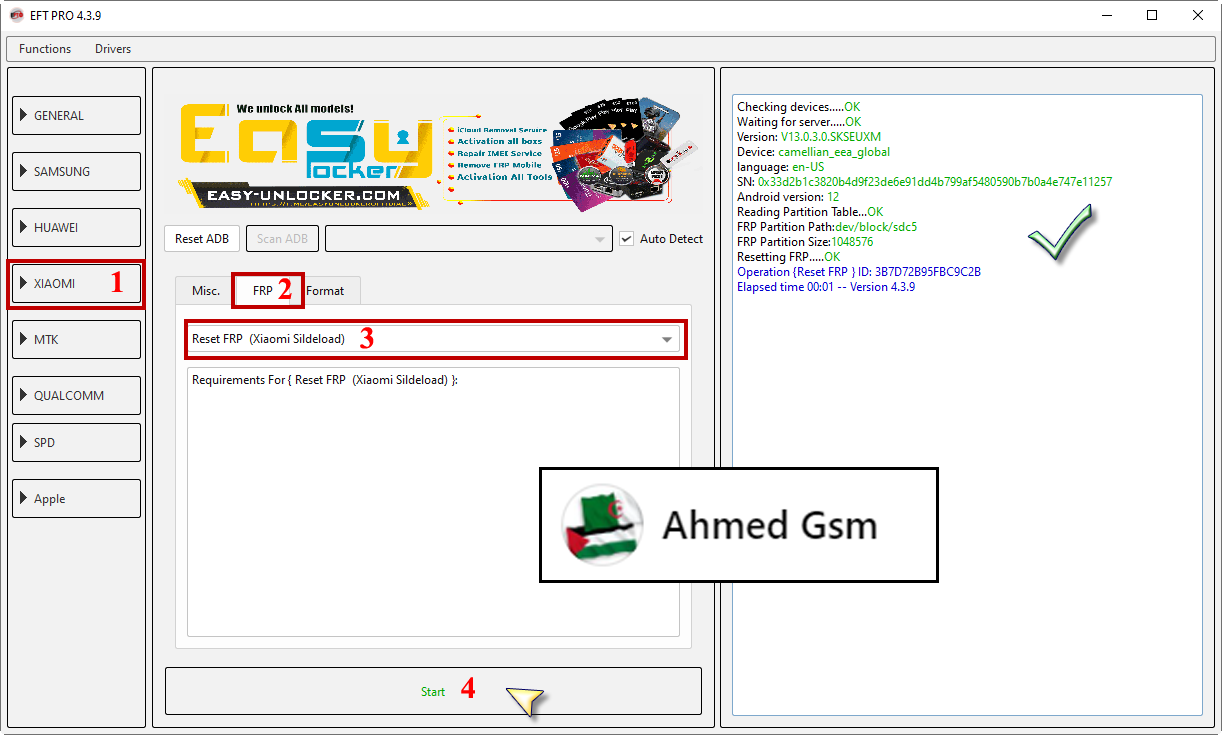
Poco M3 Pro 5G ResetFRP SildeLoad Mode EFT Pro 4.3
[video=youtube;-yJcs_nWmS0]https://www.youtube.com/watch?v=-yJcs_nWmS0&ab_channel=EFTDongle[/video]
Poco M3 Pro 5G ResetFRP SildeLoad Mode EFT Pro 4.3

كود:
[B][FONT=Arial Black]Checking devices.....OK
Waiting for server.....OK
Version: V13.0.3.0.SKSEUXM
Device: camellian_eea_global
language: en-US
SN: 0x33d2b1c3820b4d9f23de6e91dd4b799af5480590b7b0a4e7 47e11257
Android version: 12
Reading Partition Table...OK
FRP Partition Path:dev/block/sdc5
FRP Partition Size:1048576
Resetting FRP.....OK
Operation {Reset FRP } ID: 3B7D72B95FBC9C2B
Elapsed time 00:01 -- Version 4.3.9
[/FONT][/B][video=youtube;-yJcs_nWmS0]https://www.youtube.com/watch?v=-yJcs_nWmS0&ab_channel=EFTDongle[/video]
رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
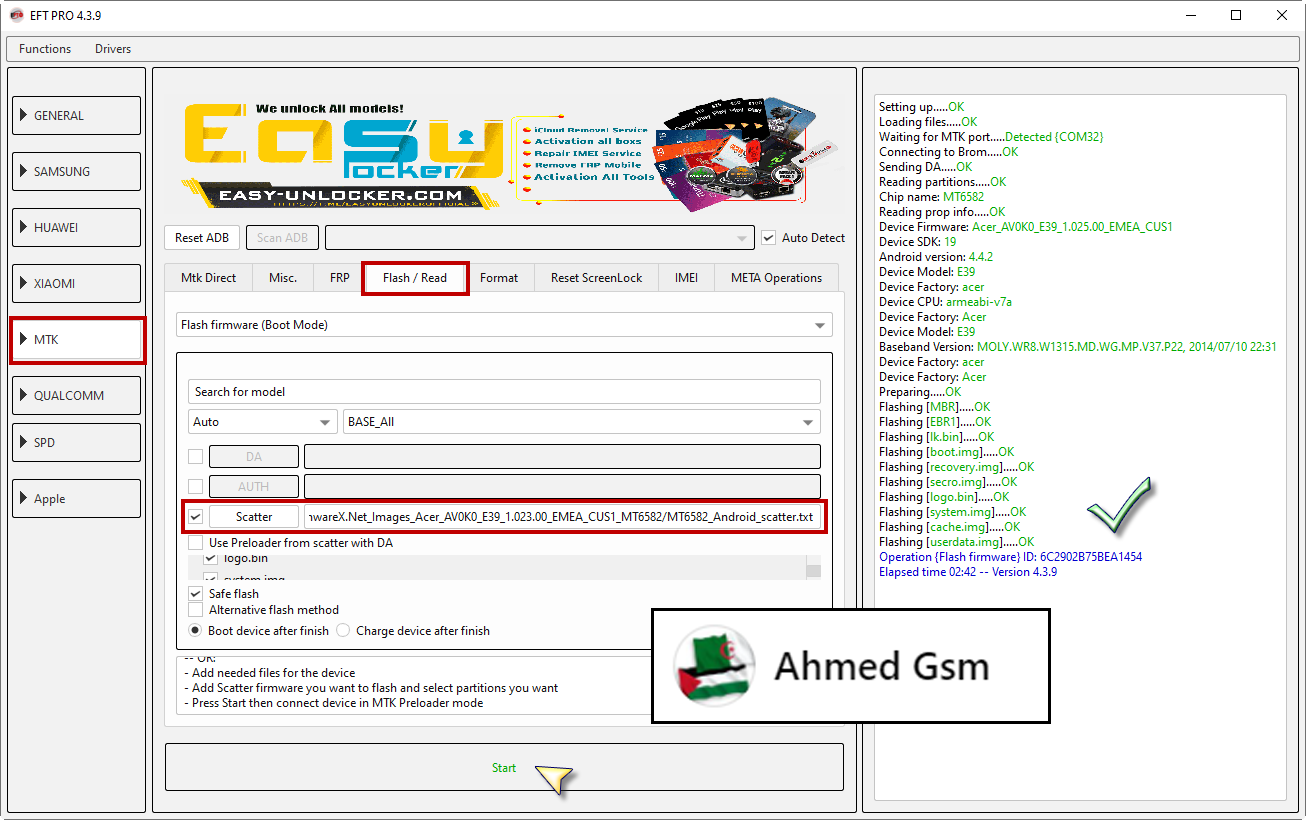
Acer Liquid E700 E39 Flash firmware Done By EFT Pro
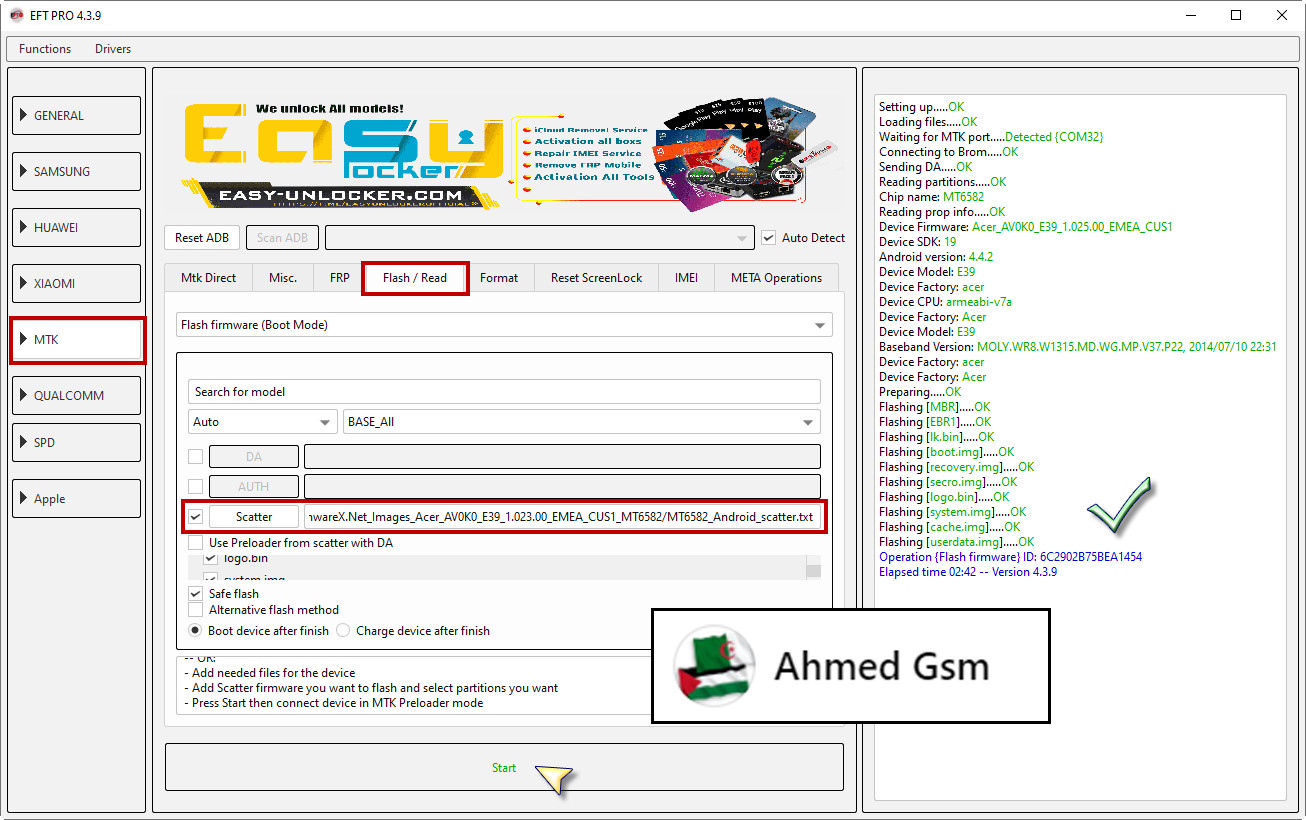
Acer Liquid E700 E39 Flash firmware Done By EFT Pro

كود:
[B][FONT=Arial Black]Setting up.....OK
Loading files.....OK
Waiting for MTK port.....Detected {COM32}
Connecting to Brom.....OK
Sending DA.....OK
Reading partitions.....OK
Chip name: MT6582
Reading prop info.....OK
Device Firmware: Acer_AV0K0_E39_1.025.00_EMEA_CUS1
Device SDK: 19
Android version: 4.4.2
Device Model: E39
Device Factory: acer
Device CPU: armeabi-v7a
Device Factory: Acer
Device Model: E39
Baseband Version: MOLY.WR8.W1315.MD.WG.MP.V37.P22, 2014/07/10 22:31
Device Factory: acer
Device Factory: Acer
Preparing.....OK
Flashing [MBR].....OK
Flashing [EBR1].....OK
Flashing [lk.bin].....OK
Flashing [boot.img].....OK
Flashing [recovery.img].....OK
Flashing [secro.img].....OK
Flashing [logo.bin].....OK
Flashing [system.img].....OK
Flashing [cache.img].....OK
Flashing [userdata.img].....OK
Operation {Flash firmware} ID: 6C2902B75BEA1454
Elapsed time 02:42 -- Version 4.3.9
[/FONT][/B]رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
Infinix Hot 11 (X662) Resetting FRP Done By EFT Pro
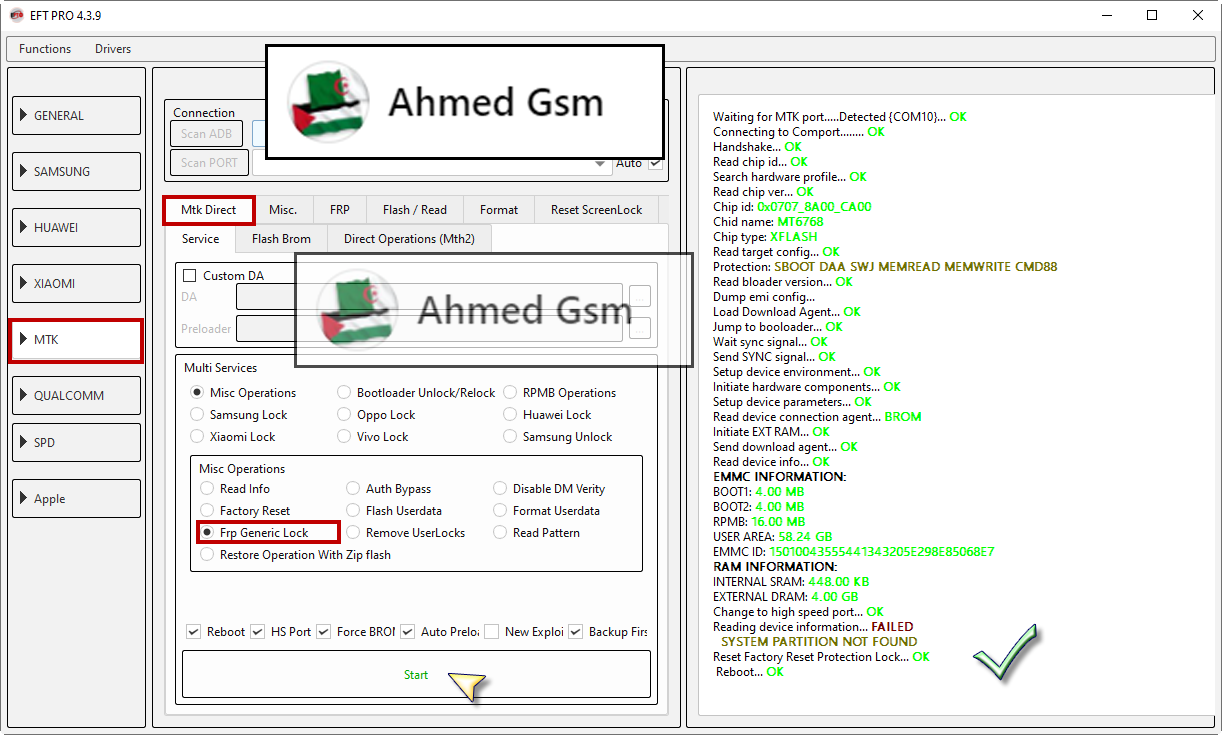
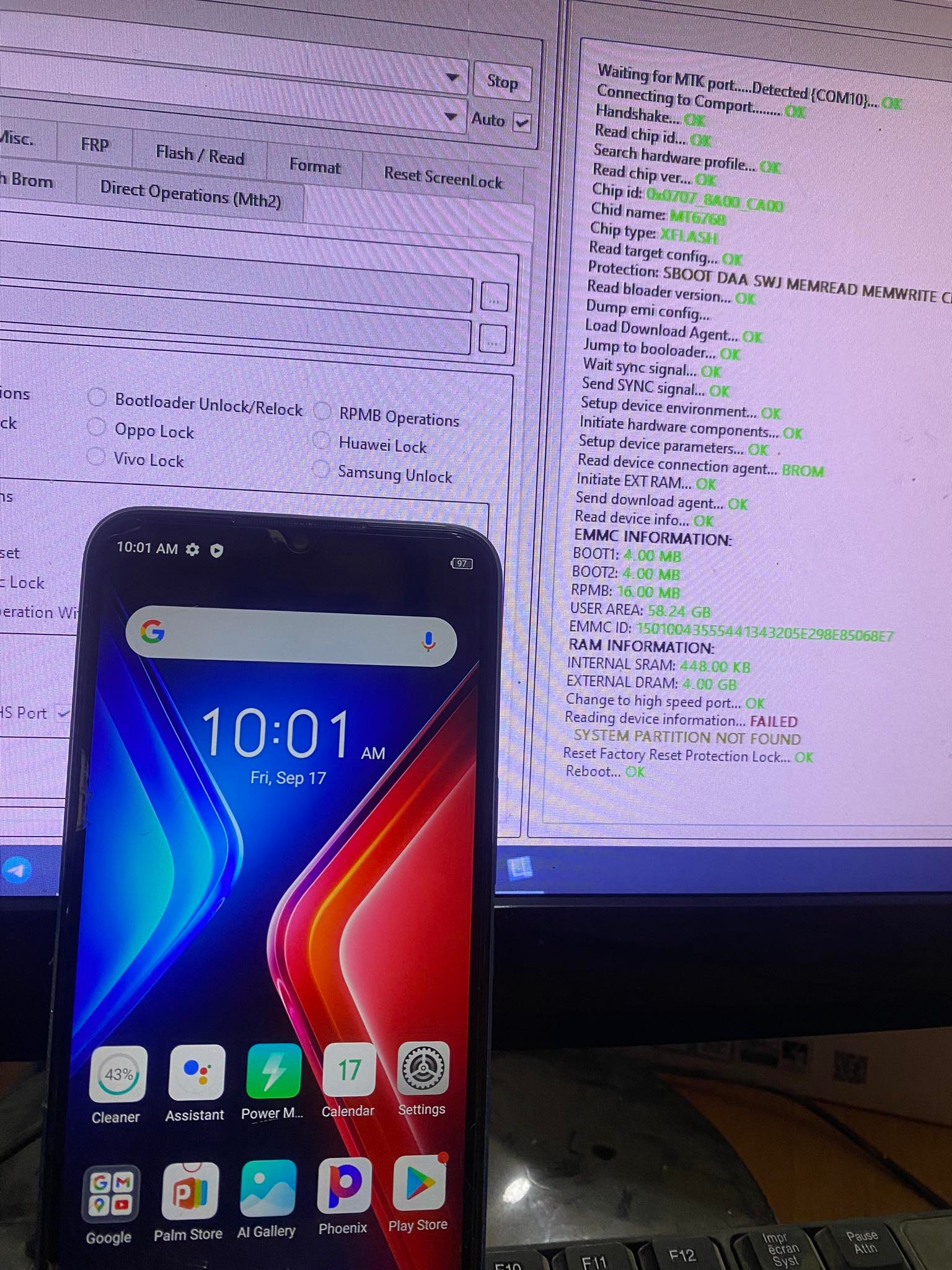
Infinix Hot 11 (X662) Resetting FRP Done By EFT Pro

كود:
[B][FONT=Arial Black]Waiting for MTK port.....Detected {COM10}... OK
Connecting to Comport........ OK
Handshake... OK
Read chip id... OK
Search hardware profile... OK
Read chip ver... OK
Chip id: 0x0707_8A00_CA00
Chid name: MT6768
Chip type: XFLASH
Read target config... OK
Protection: SBOOT DAA SWJ MEMREAD MEMWRITE CMD88
Read bloader version... OK
Dump emi config...
Load Download Agent... OK
Jump to booloader... OK
Wait sync signal... OK
Send SYNC signal... OK
Setup device environment... OK
Initiate hardware components... OK
Setup device parameters... OK
Read device connection agent... BROM
Initiate EXT RAM... OK
Send download agent... OK
Read device info... OK
EMMC INFORMATION:
BOOT1: 4.00 MB
BOOT2: 4.00 MB
RPMB: 16.00 MB
USER AREA: 58.24 GB
EMMC ID: 15010043555441343205E298E85068E7
RAM INFORMATION:
INTERNAL SRAM: 448.00 KB
EXTERNAL DRAM: 4.00 GB
Change to high speed port... OK
Reading device information... FAILED
SYSTEM PARTITION NOT FOUND
Reset Factory Reset Protection Lock... OK
Reboot... OK[/FONT]
[/B]
رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
Oppo F11 Pro (CPH1987) Flash Firmware Done By EFT Pro
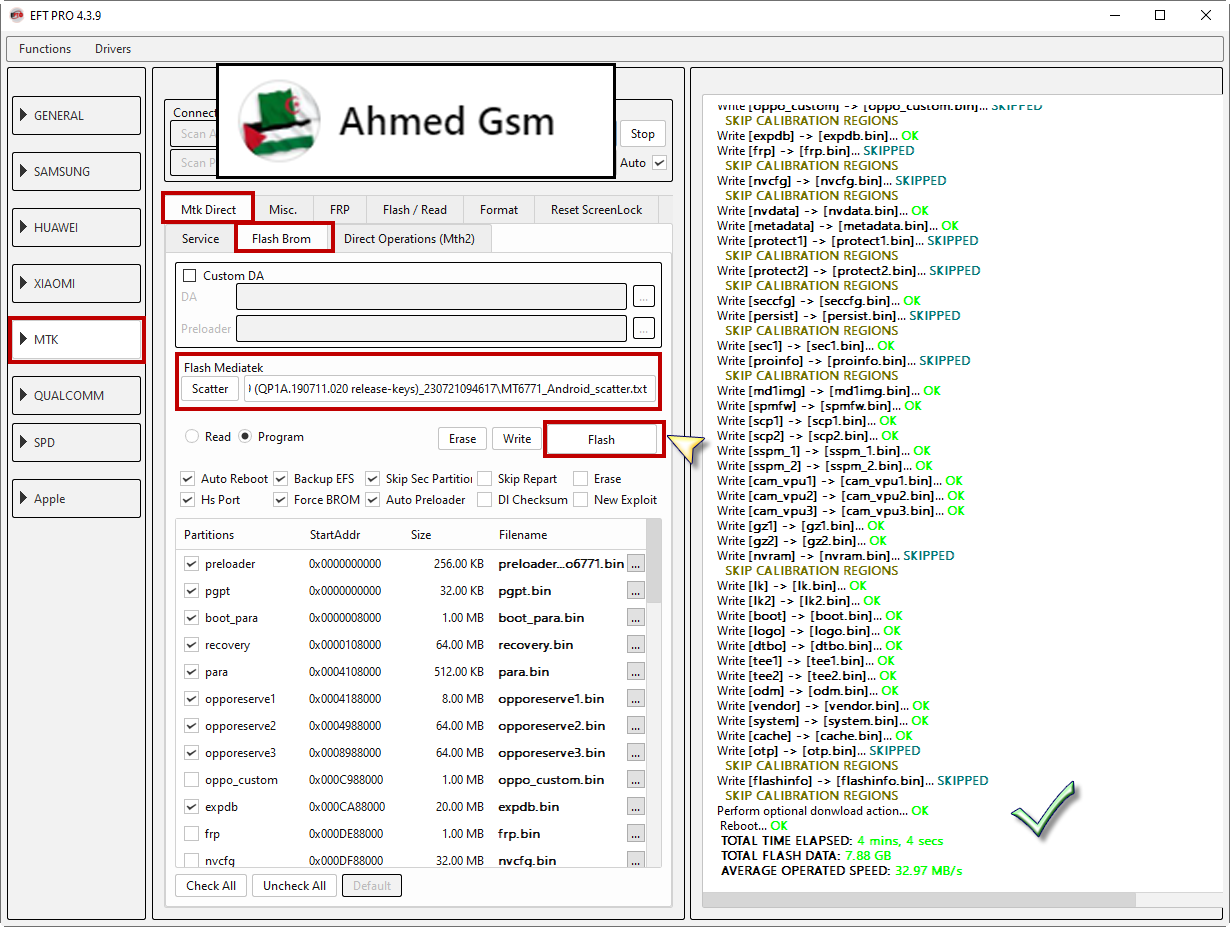
Oppo F11 Pro (CPH1987) Flash Firmware Done By EFT Pro

كود:
[B][FONT=Arial Black]Waiting for MTK port.....Detected {COM10}... OK
Connecting to Comport........ OK
Handshake... OK
Read chip id... OK
Search hardware profile... OK
Read chip ver... OK
Chip id: 0x0788_8A00_CA00
Chid name: MT6771
Chip type: XFLASH
Read target config... OK
Protection: SBOOT DAA SWJ MEMREAD MEMWRITE CMD88
Read bloader version... OK
Dump emi config...
Load Download Agent... OK
Jump to booloader... OK
Wait sync signal... OK
Send SYNC signal... OK
Setup device environment... OK
Initiate hardware components... OK
Setup device parameters... OK
Read device connection agent... BROM
Initiate EXT RAM... OK
Send download agent... OK
Read device info... OK
EMMC INFORMATION:
BOOT1: 4.00 MB
BOOT2: 4.00 MB
RPMB: 16.00 MB
USER AREA: 116.48 GB
EMMC ID: 150100335636434D4202F0A56A16563B
RAM INFORMATION:
INTERNAL SRAM: 224.00 KB
EXTERNAL DRAM: 6.00 GB
Change to high speed port... OK
Prepare to backup calibration data... OK
Backup preloader... OK
Backup opporeserve1... OK
Backup opporeserve2... OK
Backup opporeserve3... OK
Backup oppo_custom... OK
Backup nvcfg... OK
Backup nvdata... OK
Backup protect1... OK
Backup protect2... OK
Backup seccfg... OK
Backup persist... OK
Backup proinfo... OK
Backup nvram... OK
Calibration data is saved to C:\Program Files (x86)\EFT Dongle\update\CalibrationBackup\Unknown_Device_10_QP1A.190711.020_QP1A.190711.020_release-keys_2212170843.zip
Start download information... OK
Check SGPT... OK
Check PGPT... OK
Write [preloader] -> [preloader_oppo6771.bin]... OK
Write [pgpt] -> [pgpt.bin]... OK
Write [boot_para] -> [boot_para.bin]... OK
Write [recovery] -> [recovery.bin]... OK
Write [para] -> [para.bin]... OK
Write [opporeserve1] -> [opporeserve1.bin]... OK
Write [opporeserve2] -> [opporeserve2.bin]... OK
Write [opporeserve3] -> [opporeserve3.bin]... OK
Write [oppo_custom] -> [oppo_custom.bin]... SKIPPED
SKIP CALIBRATION REGIONS
Write [expdb] -> [expdb.bin]... OK
Write [frp] -> [frp.bin]... SKIPPED
SKIP CALIBRATION REGIONS
Write [nvcfg] -> [nvcfg.bin]... SKIPPED
SKIP CALIBRATION REGIONS
Write [nvdata] -> [nvdata.bin]... OK
Write [metadata] -> [metadata.bin]... OK
Write [protect1] -> [protect1.bin]... SKIPPED
SKIP CALIBRATION REGIONS
Write [protect2] -> [protect2.bin]... SKIPPED
SKIP CALIBRATION REGIONS
Write [seccfg] -> [seccfg.bin]... OK
Write [persist] -> [persist.bin]... SKIPPED
SKIP CALIBRATION REGIONS
Write [sec1] -> [sec1.bin]... OK
Write [proinfo] -> [proinfo.bin]... SKIPPED
SKIP CALIBRATION REGIONS
Write [md1img] -> [md1img.bin]... OK
Write [spmfw] -> [spmfw.bin]... OK
Write [scp1] -> [scp1.bin]... OK
Write [scp2] -> [scp2.bin]... OK
Write [sspm_1] -> [sspm_1.bin]... OK
Write [sspm_2] -> [sspm_2.bin]... OK
Write [cam_vpu1] -> [cam_vpu1.bin]... OK
Write [cam_vpu2] -> [cam_vpu2.bin]... OK
Write [cam_vpu3] -> [cam_vpu3.bin]... OK
Write [gz1] -> [gz1.bin]... OK
Write [gz2] -> [gz2.bin]... OK
Write [nvram] -> [nvram.bin]... SKIPPED
SKIP CALIBRATION REGIONS
Write [lk] -> [lk.bin]... OK
Write [lk2] -> [lk2.bin]... OK
Write [boot] -> [boot.bin]... OK
Write [logo] -> [logo.bin]... OK
Write [dtbo] -> [dtbo.bin]... OK
Write [tee1] -> [tee1.bin]... OK
Write [tee2] -> [tee2.bin]... OK
Write [odm] -> [odm.bin]... OK
Write [vendor] -> [vendor.bin]... OK
Write [system] -> [system.bin]... OK
Write [cache] -> [cache.bin]... OK
Write [otp] -> [otp.bin]... SKIPPED
SKIP CALIBRATION REGIONS
Write [flashinfo] -> [flashinfo.bin]... SKIPPED
SKIP CALIBRATION REGIONS
Perform optional donwload action... OK
Reboot... OK
TOTAL TIME ELAPSED: 4 mins, 4 secs
TOTAL FLASH DATA: 7.88 GB
AVERAGE OPERATED SPEED: 32.97 MB/s
[/FONT][/B]رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
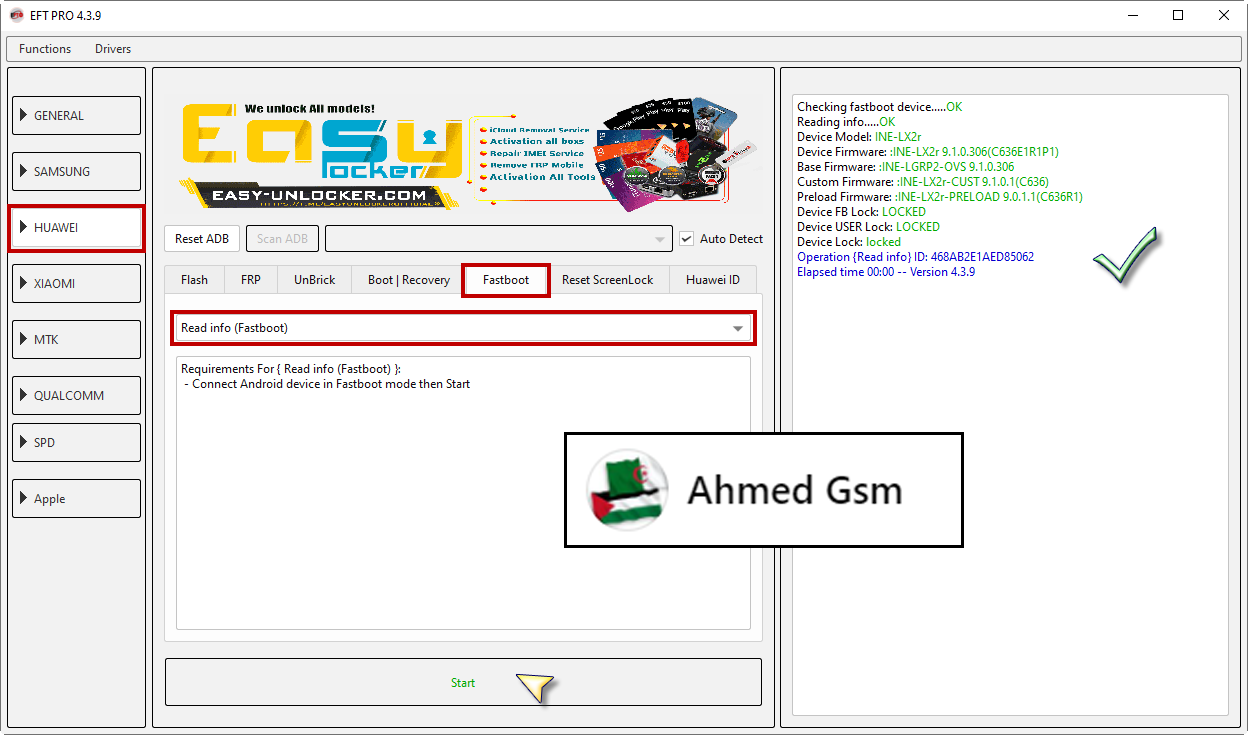
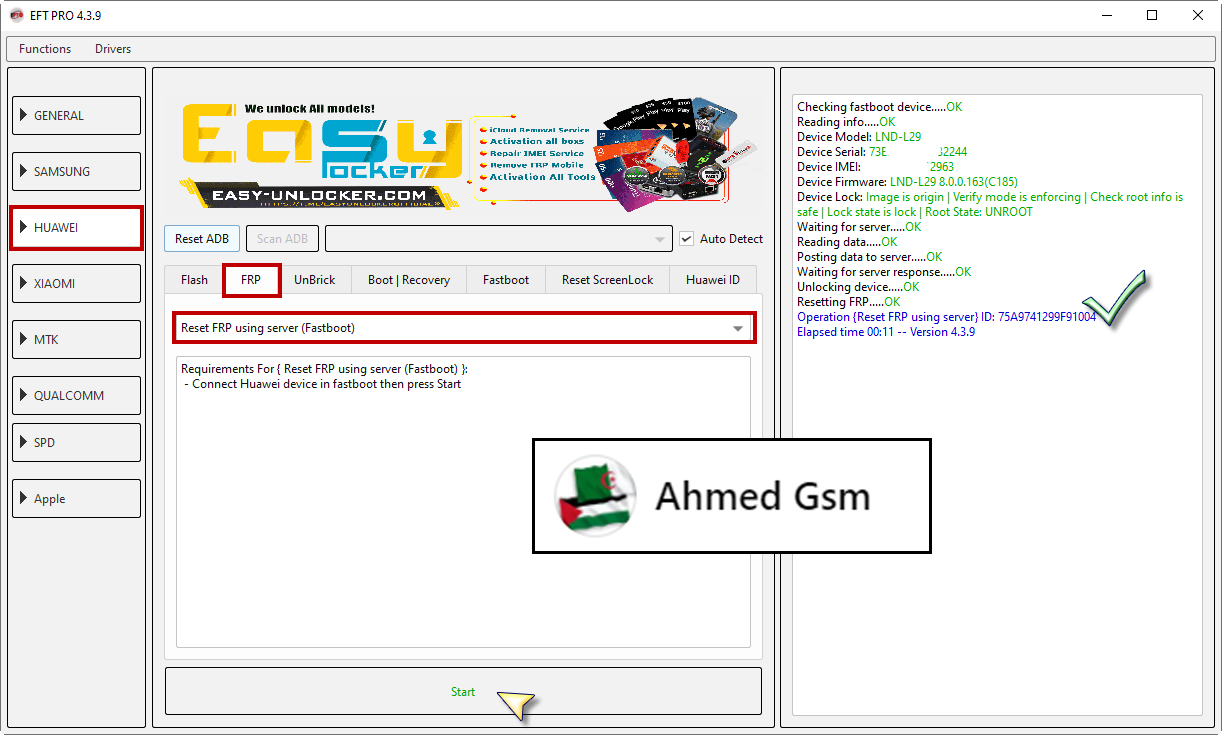
Huawei P8 Lite 2017 (PRA-LX1) Resetting FRP Done By EFT Pro
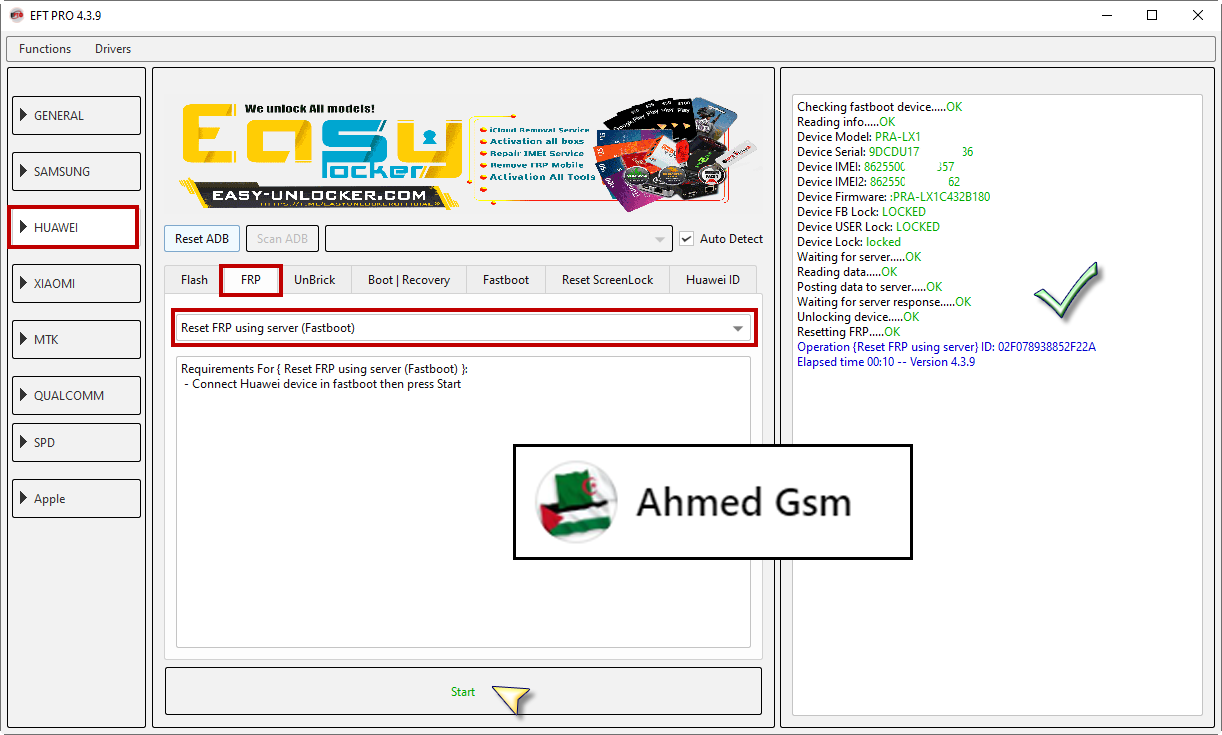
Huawei P8 Lite 2017 (PRA-LX1) Resetting FRP Done By EFT Pro

كود:
[B][FONT=Arial Black]Checking fastboot device.....OK
Reading info.....OK
Device Model: PRA-LX1
Device Serial: 9DCDUXXXXXXX886
Device IMEI: 862550XXXXXXX57
Device IMEI2: 862550XXXXXXX62
Device Firmware: :PRA-LX1C432B180
Device FB Lock: LOCKED
Device USER Lock: LOCKED
Device Lock: locked
Waiting for server.....OK
Reading data.....OK
Posting data to server.....OK
Waiting for server response.....OK
Unlocking device.....OK
Resetting FRP.....OK
Operation {Reset FRP using server} ID: 02F078938852F22A
Elapsed time 00:10 -- Version 4.3.9
[/FONT][/B]رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
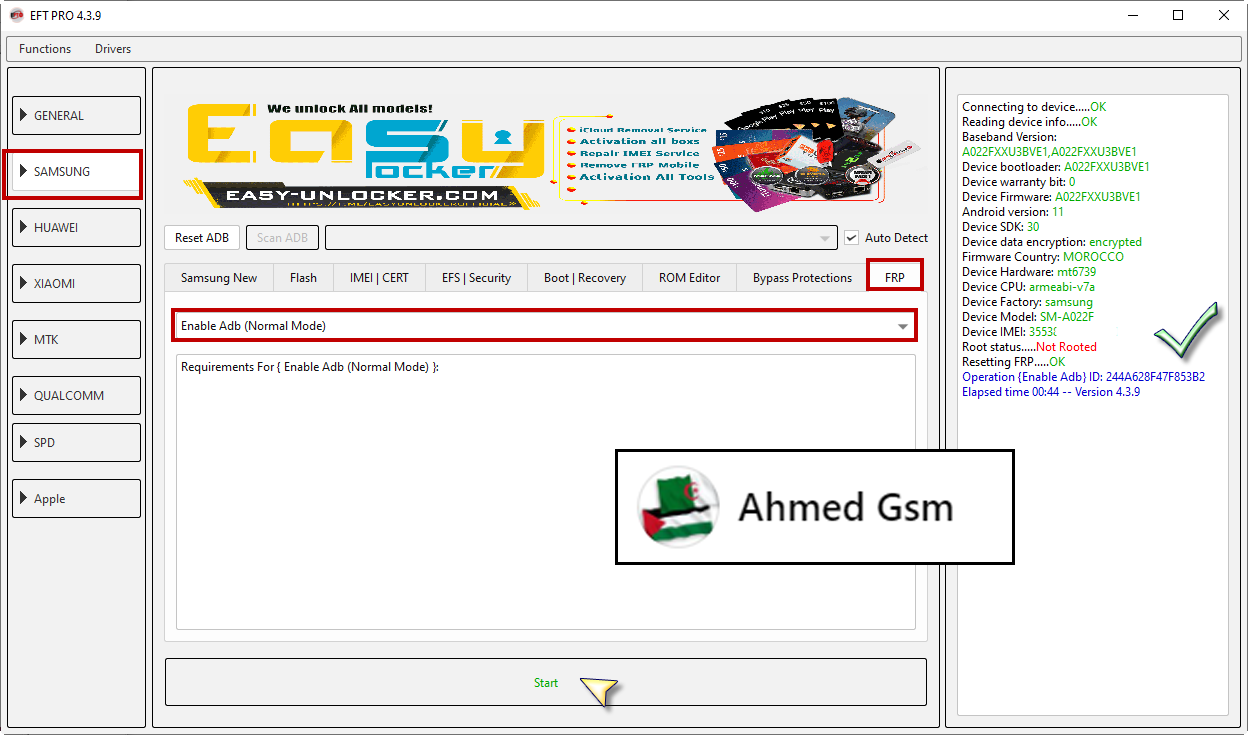
Samsung A8 2018 (SM-A530F) Resetting FRP Done By EFT Pro
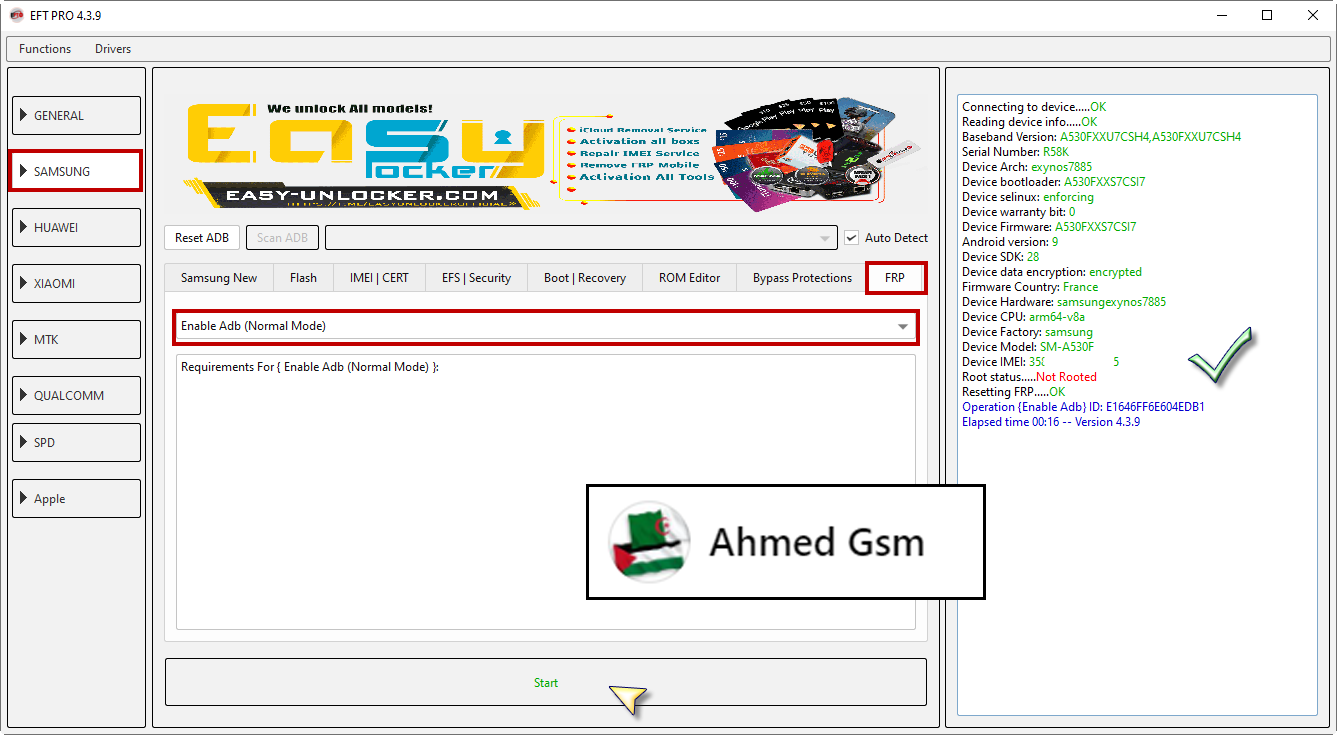
Samsung A8 2018 (SM-A530F) Resetting FRP Done By EFT Pro

كود:
[B][FONT=Arial Black]Connecting to device.....OK
Reading device info.....OK
Baseband Version: A530FXXU7CSH4,A530FXXU7CSH4
Serial Number: R5XXXXXXXGLZ
Device Arch: exynos7885
Device bootloader: A530FXXS7CSI7
Device selinux: enforcing
Device warranty bit: 0
Device Firmware: A530FXXS7CSI7
Android version: 9
Device SDK: 28
Device data encryption: encrypted
Firmware Country: France
Device Hardware: samsungexynos7885
Device CPU: arm64-v8a
Device Factory: samsung
Device Model: SM-A530F
Device IMEI: 358XXXXXXXX0715
Root status.....Not Rooted
Resetting FRP.....OK
Operation {Enable Adb} ID: E1646FF6E604EDB1
Elapsed time 00:16 -- Version 4.3.9
[/FONT][/B]رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
iPhone 6 iOS 12.5.6
Bypass Pascode (WITH SIGNAL)
DONE BY EFT PRO 4.3.9
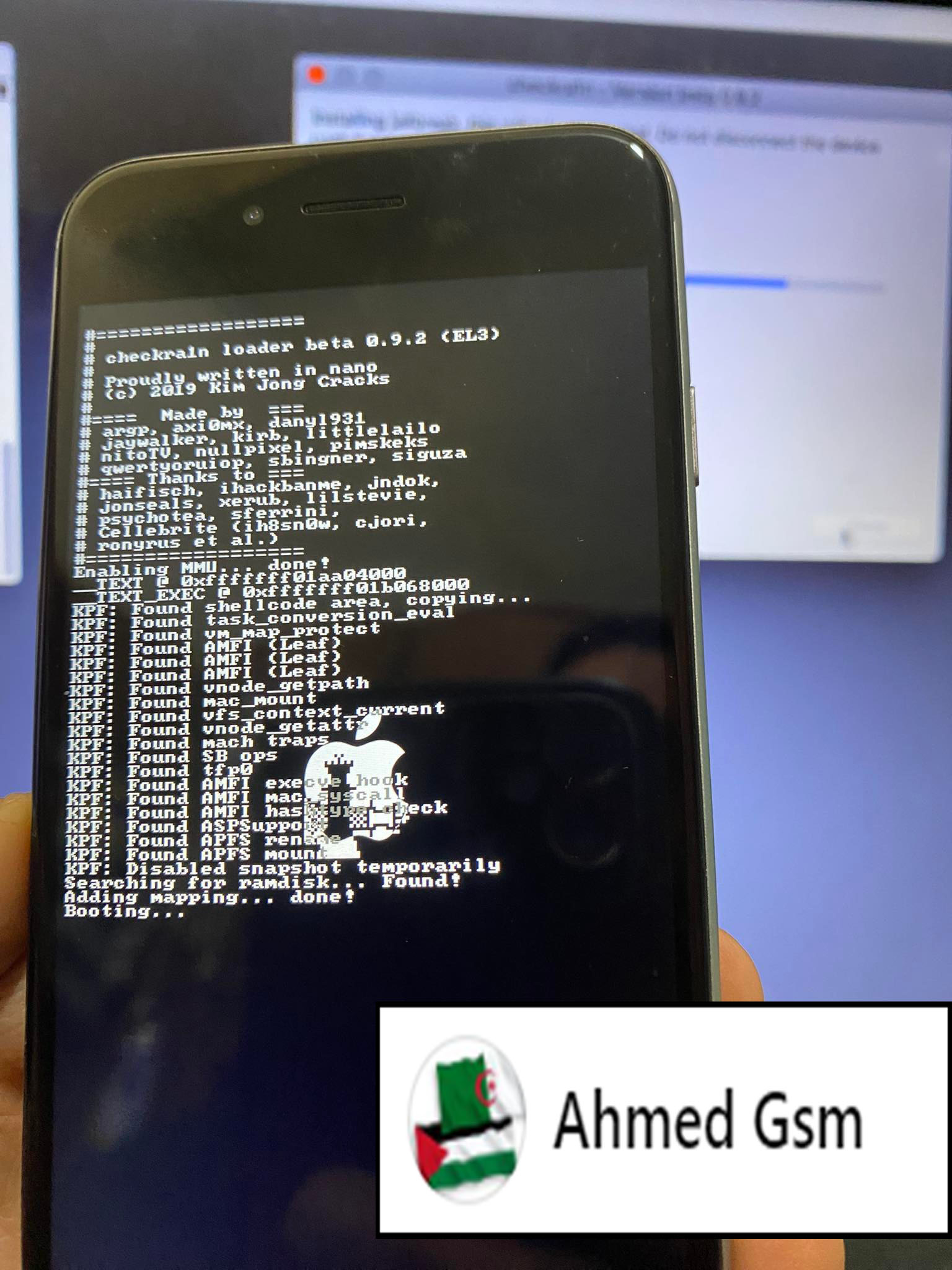
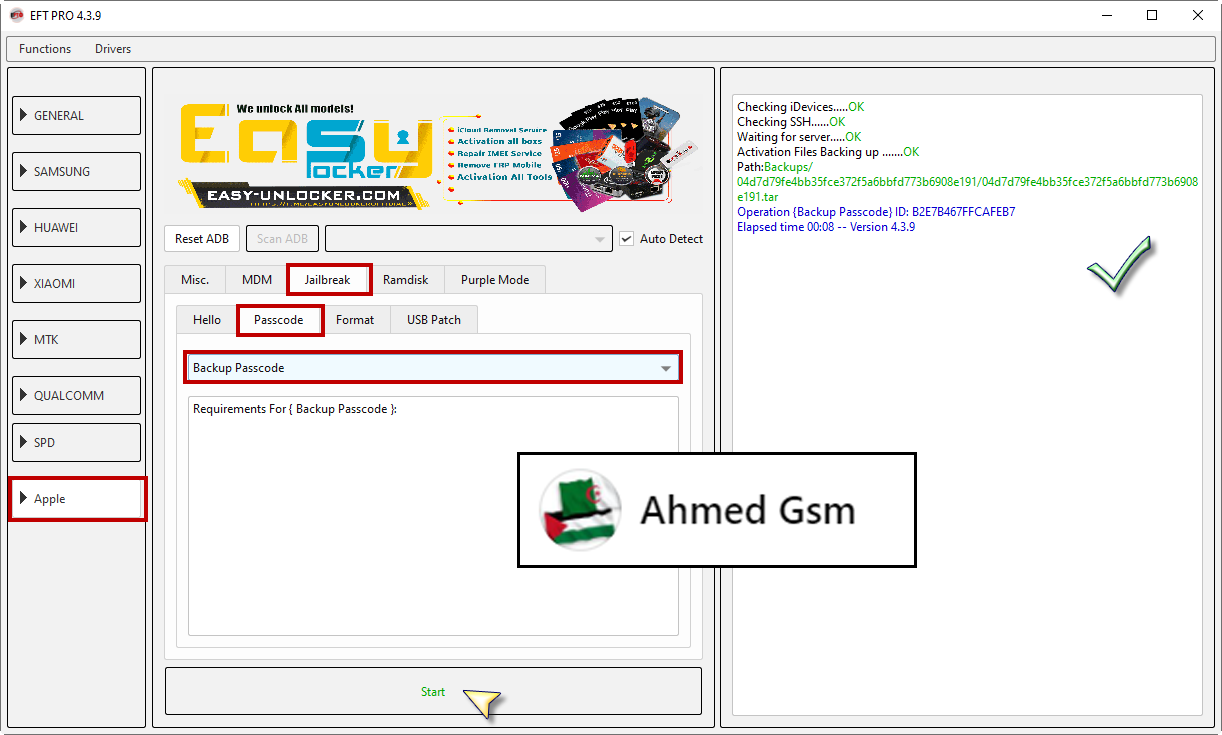
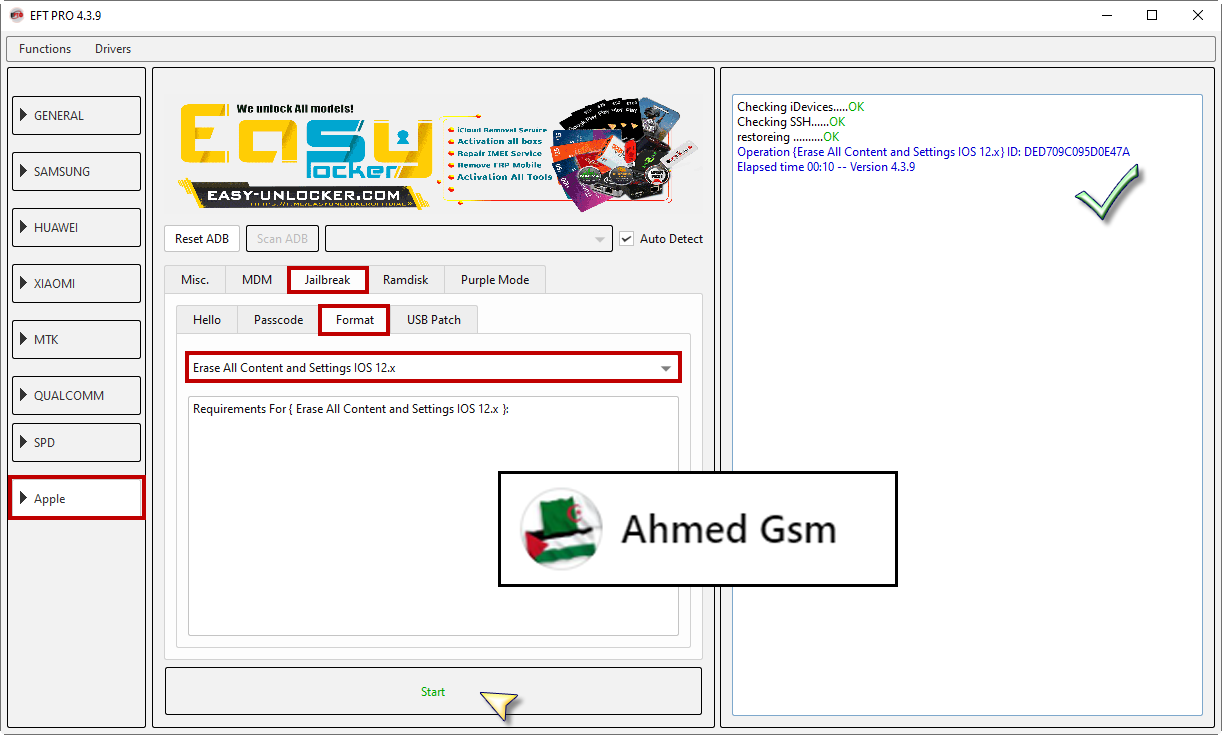
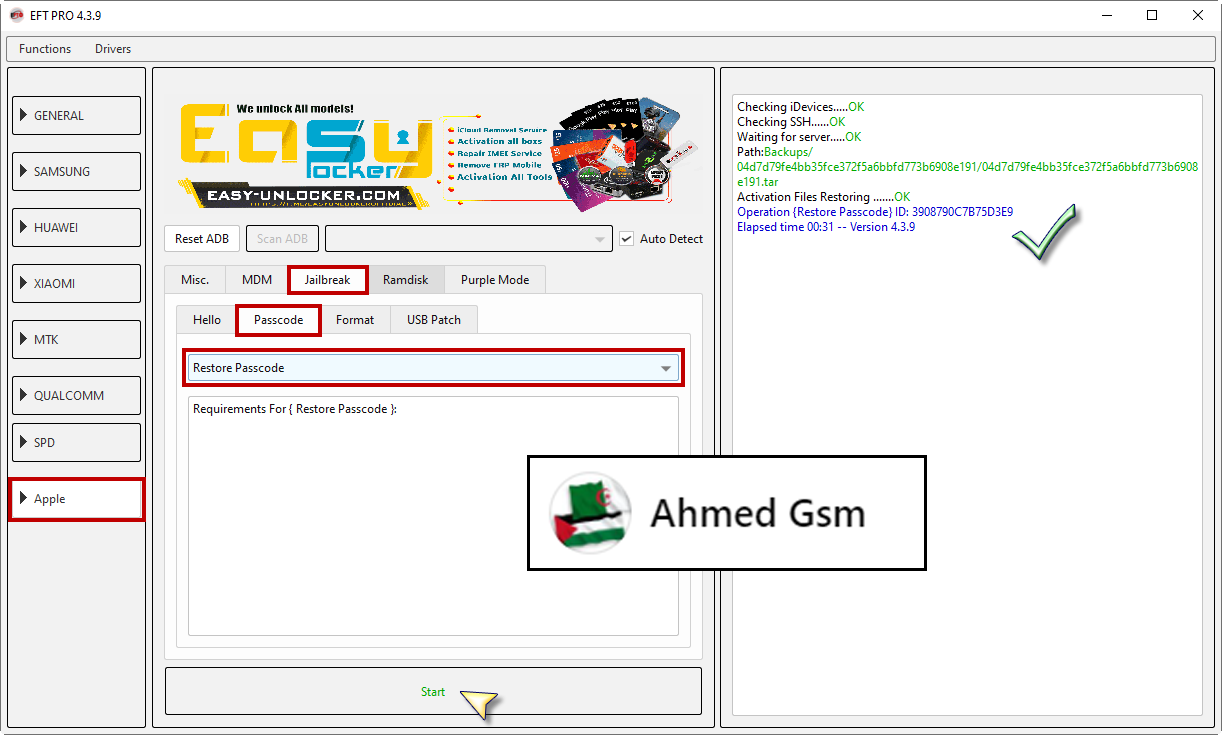
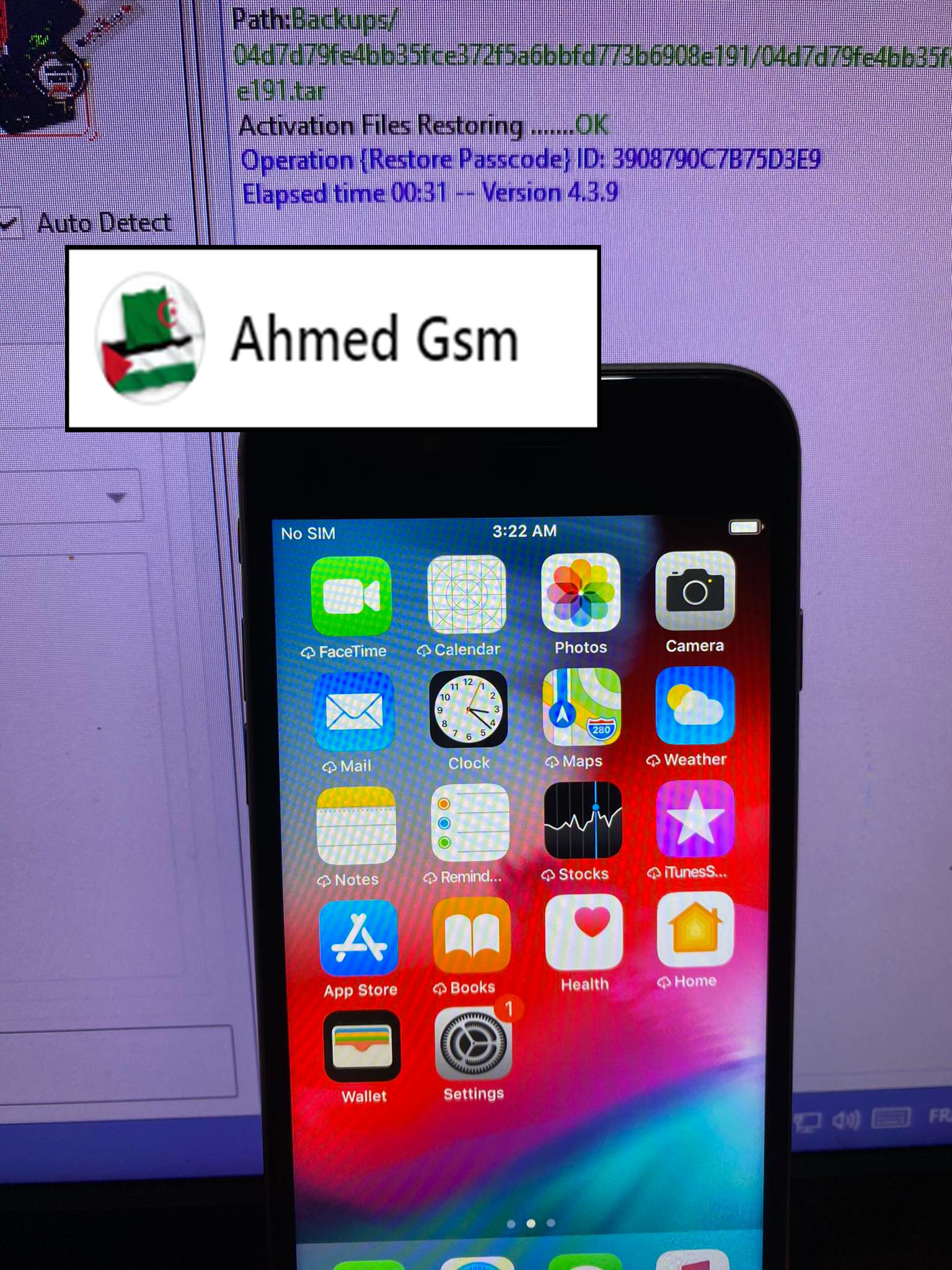
iPhone 6 iOS 12.5.6
Bypass Pascode (WITH SIGNAL)
DONE BY EFT PRO 4.3.9


كود:
[B][FONT=Arial Black]Checking iDevices.....OK
Checking SSH......OK
Waiting for server.....OK
Activation Files Backing up .......OK
Path:Backups/04d7d79fe4bb35fce372f5a6bbfd773b6908e191/04d7d79fe4bb35fce372f5a6bbfd773b6908e191.tar
Operation {Backup Passcode} ID: B2E7B467FFCAFEB7
Elapsed time 00:08 -- Version 4.3.9
[/FONT][/B]
كود:
[B][FONT=Arial Black]Checking iDevices.....OK
Checking SSH......OK
restoreing ..........OK
Operation {Erase All Content and Settings IOS 12.x} ID: DED709C095D0E47A
Elapsed time 00:10 -- Version 4.3.9
[/FONT][/B]
كود:
[B][FONT=Arial Black]Checking iDevices.....OK
Checking SSH......OK
Waiting for server.....OK
Path:Backups/04d7d79fe4bb35fce372f5a6bbfd773b6908e191/04d7d79fe4bb35fce372f5a6bbfd773b6908e191.tar
Activation Files Restoring .......OK
Operation {Restore Passcode} ID: 3908790C7B75D3E9
Elapsed time 00:31 -- Version 4.3.9
[/FONT][/B]
رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
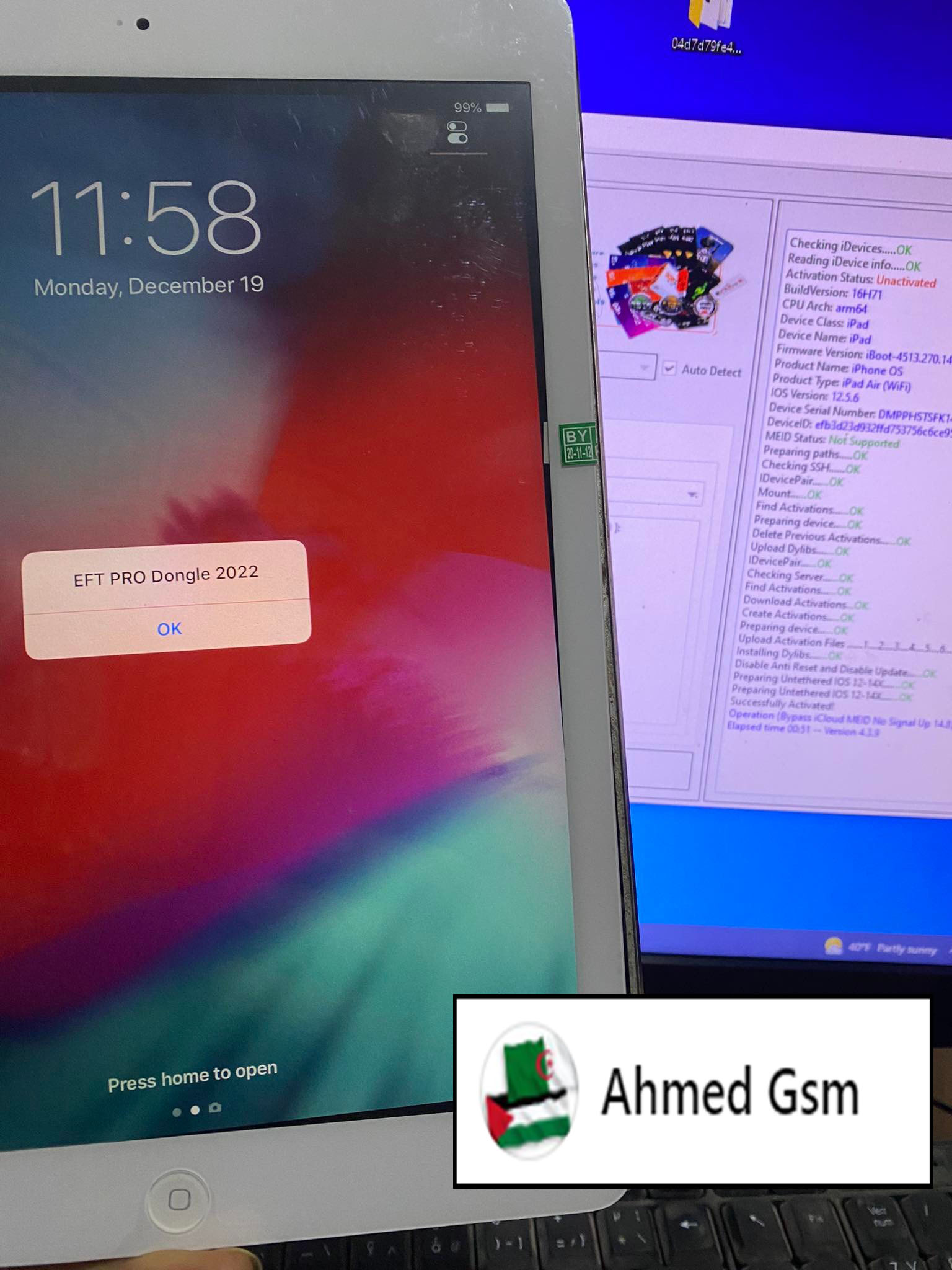
iPad Air (WiFi) Bypass iCloud iOS 12.5.6 Done
Jailbreak Windows Or MAC
Bypass iCloud MEID No Signal Up 14.8
EFT Pro 4.3.9
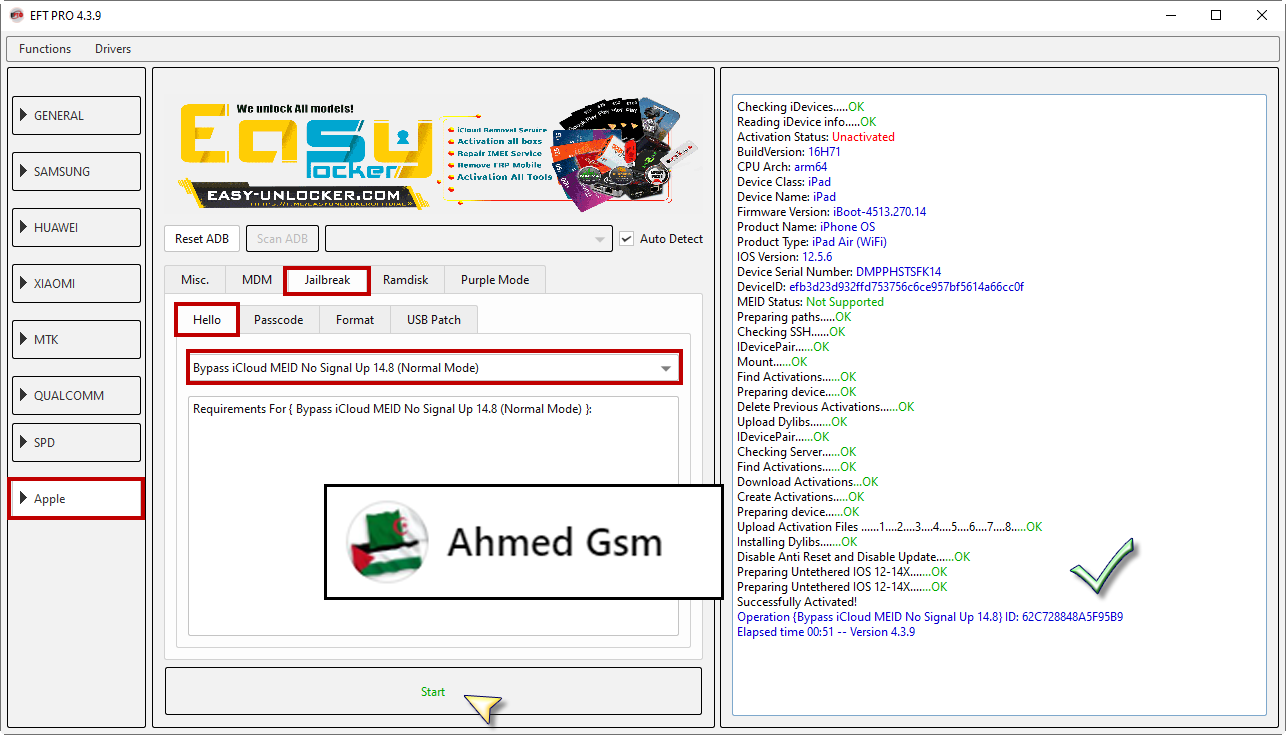
iPad Air (WiFi) Bypass iCloud iOS 12.5.6 Done
Jailbreak Windows Or MAC
Bypass iCloud MEID No Signal Up 14.8
EFT Pro 4.3.9


كود:
[B][FONT=Arial Black]Checking iDevices.....OK
Reading iDevice info.....OK
Activation Status: Unactivated
BuildVersion: 16H71
CPU Arch: arm64
Device Class: iPad
Device Name: iPad
Firmware Version: iBoot-4513.270.14
Product Name: iPhone OS
Product Type: iPad Air (WiFi)
IOS Version: 12.5.6
Device Serial Number: DMPPHSTSFK14
DeviceID: efb3d23d932ffd753756c6ce957bf5614a66cc0f
MEID Status: Not Supported
Preparing paths.....OK
Checking SSH......OK
IDevicePair......OK
Mount......OK
Find Activations......OK
Preparing device.....OK
Delete Previous Activations......OK
Upload Dylibs.......OK
IDevicePair......OK
Checking Server......OK
Find Activations......OK
Download Activations...OK
Create Activations.....OK
Preparing device......OK
Upload Activation Files ......1....2....3....4....5....6....7....8.....OK
Installing Dylibs.......OK
Disable Anti Reset and Disable Update......OK
Preparing Untethered IOS 12-14X.......OK
Preparing Untethered IOS 12-14X.......OK
Successfully Activated!
Operation {Bypass iCloud MEID No Signal Up 14.8} ID: 62C728848A5F95B9
Elapsed time 00:51 -- Version 4.3.9
[/FONT][/B]
رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
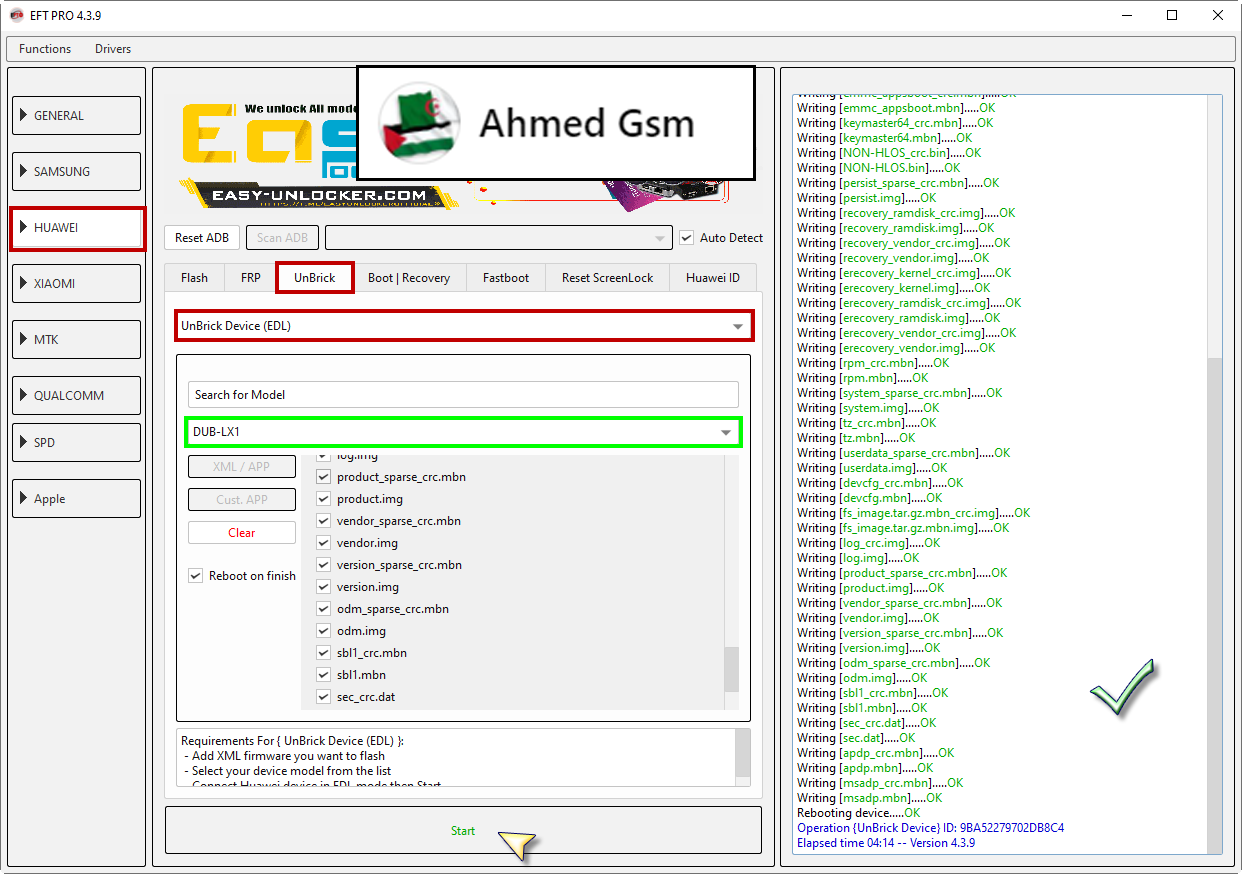
Huawei Y7 Prime 2019
(DUB-LX1)
Unbrick Repair Done
By EFT Pro
Huawei Y7 Prime 2019
(DUB-LX1)
Unbrick Repair Done
By EFT Pro

كود:
[B][FONT=Arial Black]Checking EDL port.....Detected {COM14 }
Decrypting package.....OK
Inflating package.....OK
Preparing.....OK
Loading loader.....OK
Sending files.....OK
Resetting device.....OK
Waiting for fastboot device.....OK
Reading info.....OK
Device Lock: Image is origin | Verify mode is enforcing | Check root info is safe | Lock state is lock | Root State: UNROOT
Checking lock.....OK
Writing [gpt_both0_crc.bin].....OK
Writing [gpt_both0.bin].....OK
Writing [adspso_crc.bin].....OK
Writing [adspso.bin].....OK
Writing [boot_ramdisk_crc.img].....OK
Writing [boot_ramdisk.img].....OK
Writing [kernel_crc.img].....OK
Writing [kernel.img].....OK
Writing [cache_sparse_crc.mbn].....OK
Writing [cache.img].....OK
Writing [cmnlib_30_crc.mbn].....OK
Writing [cmnlib_30.mbn].....OK
Writing [cmnlib64_30_crc.mbn].....OK
Writing [cmnlib64_30.mbn].....OK
Writing [emmc_appsboot_crc.mbn].....OK
Writing [emmc_appsboot.mbn].....OK
Writing [keymaster64_crc.mbn].....OK
Writing [keymaster64.mbn].....OK
Writing [NON-HLOS_crc.bin].....OK
Writing [NON-HLOS.bin].....OK
Writing [persist_sparse_crc.mbn].....OK
Writing [persist.img].....OK
Writing [recovery_ramdisk_crc.img].....OK
Writing [recovery_ramdisk.img].....OK
Writing [recovery_vendor_crc.img].....OK
Writing [recovery_vendor.img].....OK
Writing [erecovery_kernel_crc.img].....OK
Writing [erecovery_kernel.img].....OK
Writing [erecovery_ramdisk_crc.img].....OK
Writing [erecovery_ramdisk.img].....OK
Writing [erecovery_vendor_crc.img].....OK
Writing [erecovery_vendor.img].....OK
Writing [rpm_crc.mbn].....OK
Writing [rpm.mbn].....OK
Writing [system_sparse_crc.mbn].....OK
Writing [system.img].....OK
Writing [tz_crc.mbn].....OK
Writing [tz.mbn].....OK
Writing [userdata_sparse_crc.mbn].....OK
Writing [userdata.img].....OK
Writing [devcfg_crc.mbn].....OK
Writing [devcfg.mbn].....OK
Writing [fs_image.tar.gz.mbn_crc.img].....OK
Writing [fs_image.tar.gz.mbn.img].....OK
Writing [log_crc.img].....OK
Writing [log.img].....OK
Writing [product_sparse_crc.mbn].....OK
Writing [product.img].....OK
Writing [vendor_sparse_crc.mbn].....OK
Writing [vendor.img].....OK
Writing [version_sparse_crc.mbn].....OK
Writing [version.img].....OK
Writing [odm_sparse_crc.mbn].....OK
Writing [odm.img].....OK
Writing [sbl1_crc.mbn].....OK
Writing [sbl1.mbn].....OK
Writing [sec_crc.dat].....OK
Writing [sec.dat].....OK
Writing [apdp_crc.mbn].....OK
Writing [apdp.mbn].....OK
Writing [msadp_crc.mbn].....OK
Writing [msadp.mbn].....OK
Rebooting device.....OK
Operation {UnBrick Device} ID: 9BA52279702DB8C4
Elapsed time 04:14 -- Version 4.3.9
[/FONT][/B]رد: تجارب الاعضاء الناجحة فى تصليح و تفليش و فك شفرات الاجهزة على EFT Dongle
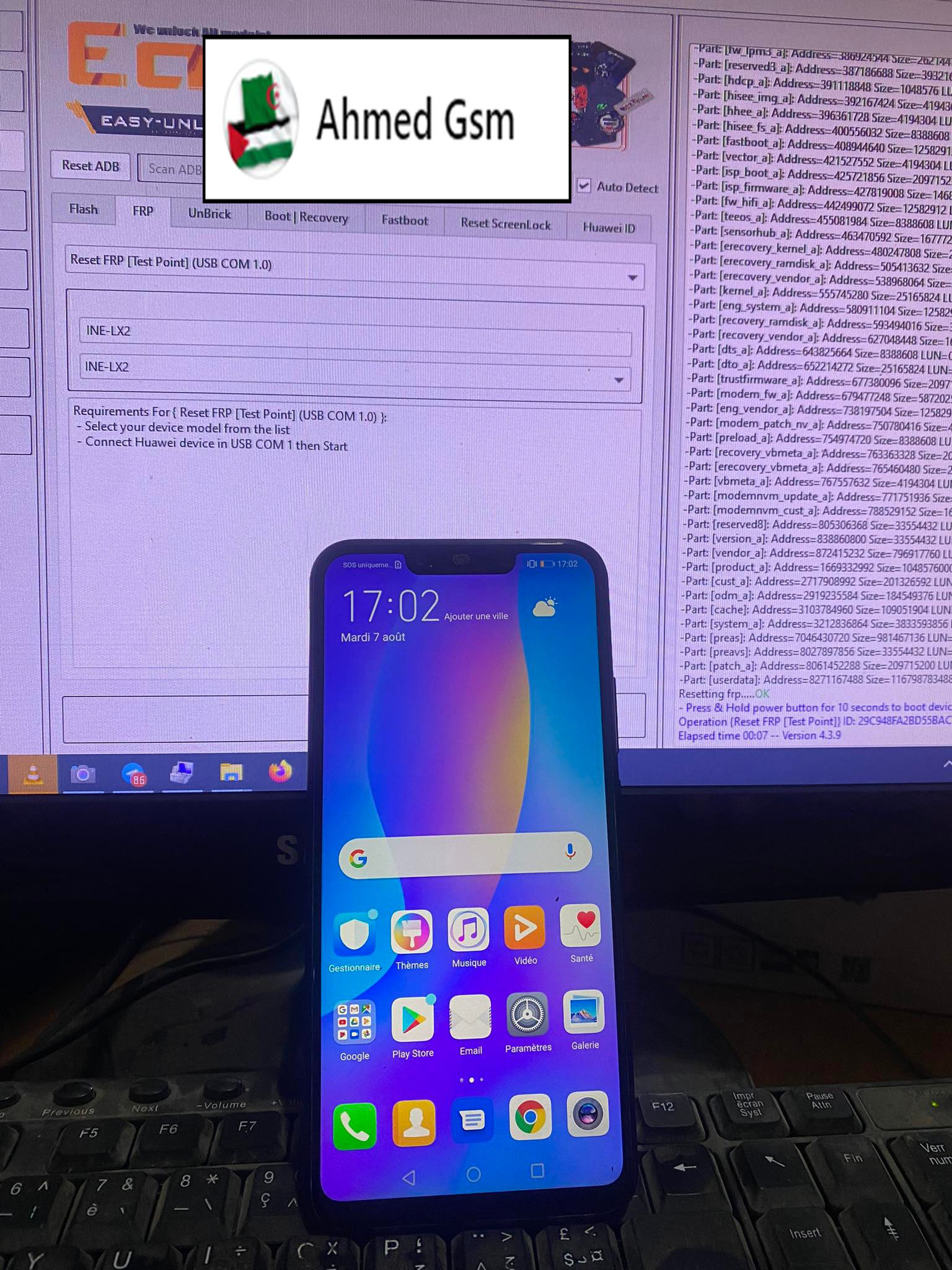
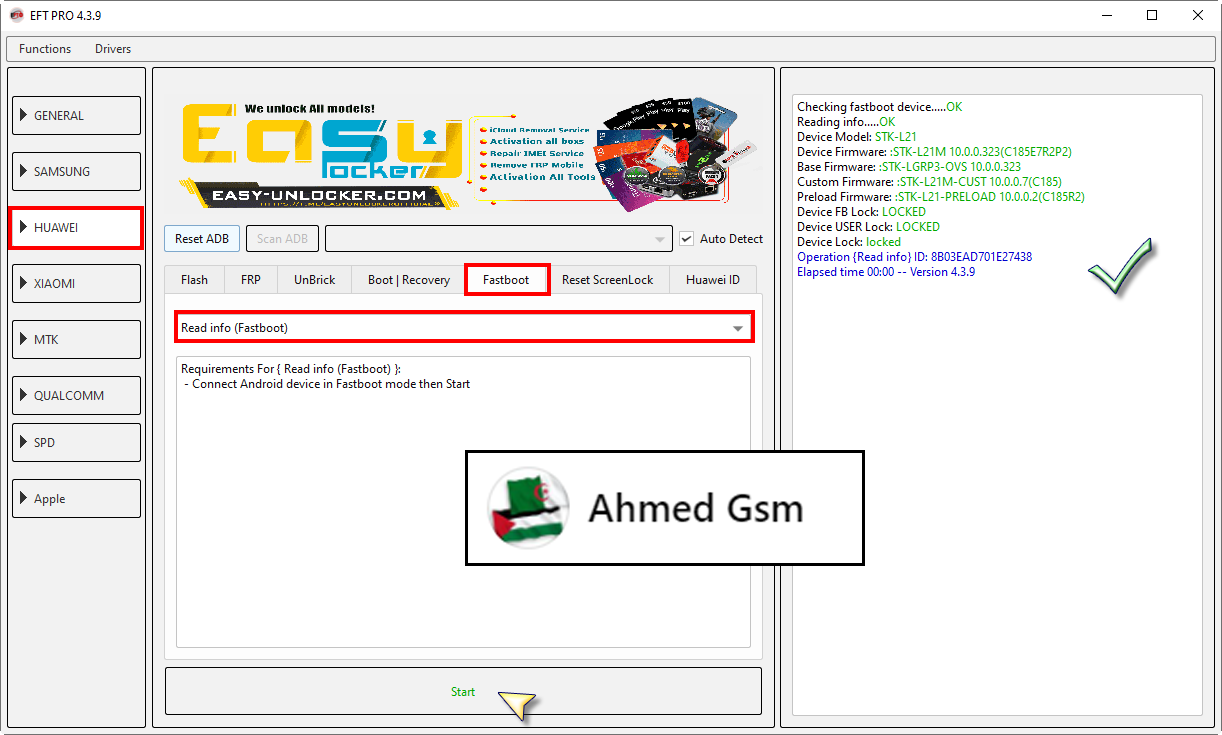
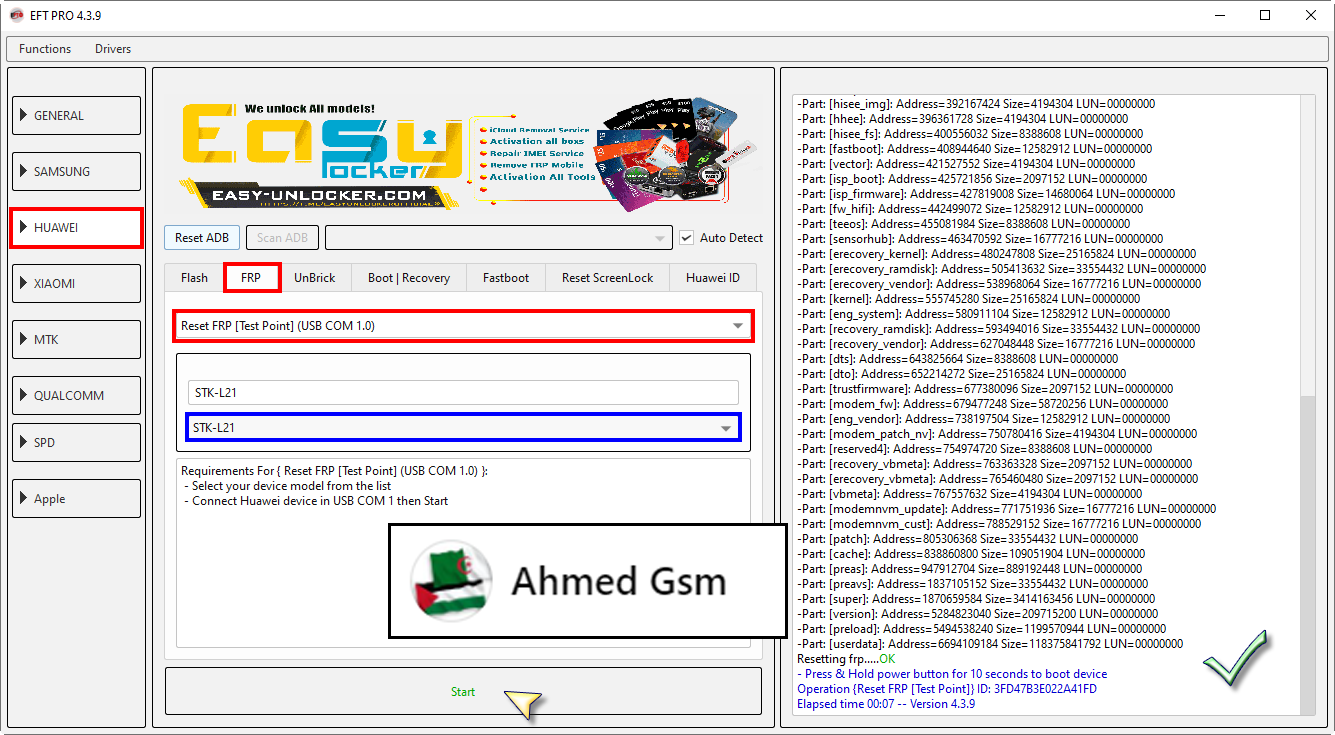
Huawei Y9 Prime 2019
(STK-L21)
Reset FRP [Test Point]
By EFT Pro
Huawei Y9 Prime 2019
(STK-L21)
Reset FRP [Test Point]
By EFT Pro


كود:
[B][FONT=Arial Black]Waiting for USB COM 1 port.....Detected {COM37}
Reading data from server.....OK
Opening Port.....OK
Writing loaders.....OK
Reading GPT.....OK
-Part: [frp]: Address=524288 Size=524288 LUN=00000000
-Part: [persist]: Address=1048576 Size=2097152 LUN=00000000
-Part: [reserved1]: Address=3145728 Size=5242880 LUN=00000000
-Part: [reserved6]: Address=8388608 Size=524288 LUN=00000000
-Part: [vrl]: Address=8912896 Size=524288 LUN=00000000
-Part: [vrl_backup]: Address=9437184 Size=524288 LUN=00000000
-Part: [modem_secure]: Address=9961472 Size=8912896 LUN=00000000
-Part: [nvme]: Address=18874368 Size=5242880 LUN=00000000
-Part: [certification]: Address=24117248 Size=1048576 LUN=00000000
-Part: [oeminfo]: Address=25165824 Size=67108864 LUN=00000000
-Part: [secure_storage]: Address=92274688 Size=33554432 LUN=00000000
-Part: [modem_om]: Address=125829120 Size=33554432 LUN=00000000
-Part: [modemnvm_factory]: Address=159383552 Size=16777216 LUN=00000000
-Part: [modemnvm_backup]: Address=176160768 Size=16777216 LUN=00000000
-Part: [modemnvm_img]: Address=192937984 Size=35651584 LUN=00000000
-Part: [reserved7]: Address=228589568 Size=2097152 LUN=00000000
-Part: [hisee_encos]: Address=230686720 Size=4194304 LUN=00000000
-Part: [veritykey]: Address=234881024 Size=1048576 LUN=00000000
-Part: [ddr_para]: Address=235929600 Size=1048576 LUN=00000000
-Part: [modem_driver]: Address=236978176 Size=20971520 LUN=00000000
-Part: [ramdisk]: Address=257949696 Size=2097152 LUN=00000000
-Part: [vbmeta_system]: Address=260046848 Size=1048576 LUN=00000000
-Part: [vbmeta_vendor]: Address=261095424 Size=1048576 LUN=00000000
-Part: [vbmeta_odm]: Address=262144000 Size=1048576 LUN=00000000
-Part: [vbmeta_cust]: Address=263192576 Size=1048576 LUN=00000000
-Part: [vbmeta_hw_product]: Address=264241152 Size=1048576 LUN=00000000
-Part: [splash2]: Address=265289728 Size=83886080 LUN=00000000
-Part: [bootfail_info]: Address=349175808 Size=2097152 LUN=00000000
-Part: [misc]: Address=351272960 Size=2097152 LUN=00000000
-Part: [dfx]: Address=353370112 Size=16777216 LUN=00000000
-Part: [rrecord]: Address=370147328 Size=16777216 LUN=00000000
-Part: [fw_lpm3]: Address=386924544 Size=262144 LUN=00000000
-Part: [kpatch]: Address=387186688 Size=3932160 LUN=00000000
-Part: [hdcp]: Address=391118848 Size=1048576 LUN=00000000
-Part: [hisee_img]: Address=392167424 Size=4194304 LUN=00000000
-Part: [hhee]: Address=396361728 Size=4194304 LUN=00000000
-Part: [hisee_fs]: Address=400556032 Size=8388608 LUN=00000000
-Part: [fastboot]: Address=408944640 Size=12582912 LUN=00000000
-Part: [vector]: Address=421527552 Size=4194304 LUN=00000000
-Part: [isp_boot]: Address=425721856 Size=2097152 LUN=00000000
-Part: [isp_firmware]: Address=427819008 Size=14680064 LUN=00000000
-Part: [fw_hifi]: Address=442499072 Size=12582912 LUN=00000000
-Part: [teeos]: Address=455081984 Size=8388608 LUN=00000000
-Part: [sensorhub]: Address=463470592 Size=16777216 LUN=00000000
-Part: [erecovery_kernel]: Address=480247808 Size=25165824 LUN=00000000
-Part: [erecovery_ramdisk]: Address=505413632 Size=33554432 LUN=00000000
-Part: [erecovery_vendor]: Address=538968064 Size=16777216 LUN=00000000
-Part: [kernel]: Address=555745280 Size=25165824 LUN=00000000
-Part: [eng_system]: Address=580911104 Size=12582912 LUN=00000000
-Part: [recovery_ramdisk]: Address=593494016 Size=33554432 LUN=00000000
-Part: [recovery_vendor]: Address=627048448 Size=16777216 LUN=00000000
-Part: [dts]: Address=643825664 Size=8388608 LUN=00000000
-Part: [dto]: Address=652214272 Size=25165824 LUN=00000000
-Part: [trustfirmware]: Address=677380096 Size=2097152 LUN=00000000
-Part: [modem_fw]: Address=679477248 Size=58720256 LUN=00000000
-Part: [eng_vendor]: Address=738197504 Size=12582912 LUN=00000000
-Part: [modem_patch_nv]: Address=750780416 Size=4194304 LUN=00000000
-Part: [reserved4]: Address=754974720 Size=8388608 LUN=00000000
-Part: [recovery_vbmeta]: Address=763363328 Size=2097152 LUN=00000000
-Part: [erecovery_vbmeta]: Address=765460480 Size=2097152 LUN=00000000
-Part: [vbmeta]: Address=767557632 Size=4194304 LUN=00000000
-Part: [modemnvm_update]: Address=771751936 Size=16777216 LUN=00000000
-Part: [modemnvm_cust]: Address=788529152 Size=16777216 LUN=00000000
-Part: [patch]: Address=805306368 Size=33554432 LUN=00000000
-Part: [cache]: Address=838860800 Size=109051904 LUN=00000000
-Part: [preas]: Address=947912704 Size=889192448 LUN=00000000
-Part: [preavs]: Address=1837105152 Size=33554432 LUN=00000000
-Part: [super]: Address=1870659584 Size=3414163456 LUN=00000000
-Part: [version]: Address=5284823040 Size=209715200 LUN=00000000
-Part: [preload]: Address=5494538240 Size=1199570944 LUN=00000000
-Part: [userdata]: Address=6694109184 Size=118375841792 LUN=00000000
Resetting frp.....OK
- Press & Hold power button for 10 seconds to boot device
Operation {Reset FRP [Test Point]} ID: 3FD47B3E022A41FD
Elapsed time 00:07 -- Version 4.3.9
[/FONT][/B]