السلام عليكم
يجب ان يكون برنامج تصفيه او تنقيح منافذ usb مثبتا lin32usb filter
والجهاز مغلق اظغط زري رقع وخفض الصوت وصله بالحاسوب
يجب ان يكون برنامج تصفيه او تنقيح منافذ usb مثبتا lin32usb filter
والجهاز مغلق اظغط زري رقع وخفض الصوت وصله بالحاسوب
كود:
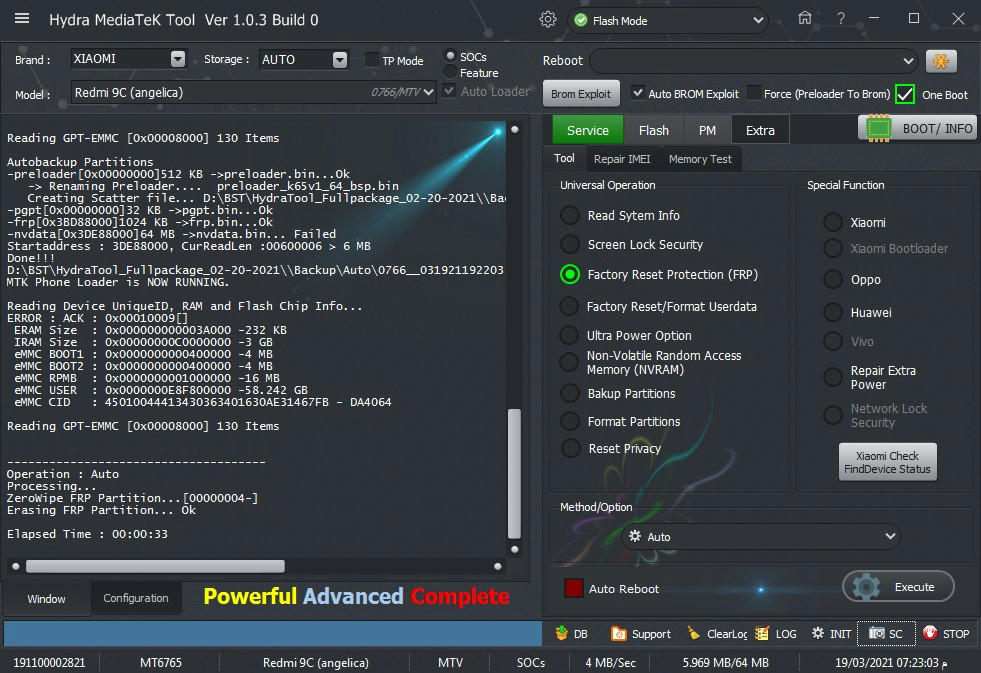
Hydra MediaTeK Tool Ver 1.0.3 Build 0[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Intel(R) Core(TM) i3 CPU 540 @ 3.07GHz[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Intel(R) HD Graphics[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Ram Installed : 3 GB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Windows Access Right Admin[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Software Run As Admnistrator[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]******* Dongle Info *******[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Version : Hydra Tool v 1.1[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Serial : 191100002821[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Initialize : OKAY[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Status : Activated[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Life : 1 [3-0-0-0-0][/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]=====================================[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Searching for MTK Device...Found[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Port Identification :Flashmode BROM [/SIZE][/FONT]
[FONT=Verdana][SIZE=5] FriendlyName :MediaTek USB Port_V1632 (COM480)[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] SymbolicName :\??\USB#VID_0E8D&PID_0003#7&9095c04&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Driver Ver :01/22/2015,3.0.1504.0[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Handshaking...Ok[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Identifying Hardware ID.....[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] BROM CPUID : 0766MT6765[6765][/SIZE][/FONT]
[FONT=Verdana][SIZE=5] BROM HW_SW_VER : 8A00 CA00 0000 0000 [/SIZE][/FONT]
[FONT=Verdana][SIZE=5] getMTKPayloadExploit : 0766[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] #Executing Exploit..[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] #SUCCESS..[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Handshaking...Ok[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Identifying Hardware ID.....[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] BROM CPUID : 0766MT6765[6765][/SIZE][/FONT]
[FONT=Verdana][SIZE=5] BROM HW_SW_VER : 8A00 CA00 0000 0000 [/SIZE][/FONT]
[FONT=Verdana][SIZE=5] FUSEID : 00000000[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] SECURE VERSION : 00 [/SIZE][/FONT]
[FONT=Verdana][SIZE=5] BL VERSION : FE [/SIZE][/FONT]
[FONT=Verdana][SIZE=5] BR Secured : E0[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Preparing Download Agent..[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] DA : 6765.bin[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Agent: MTK_DOWNLOAD_AGENT -HYDRA[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Ver : MTK_AllInOne_DA_v3.3001.2020-11-03.22:07_536568[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Init : Loader [1][/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Sending : Accepted[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Identifying Protocol...[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]C0[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Protocol : New[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Synchronization...[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]SYNCSYNC[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Mode : brom[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Preloader Initialization...[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Parsing preloader_k65v1_64_bsp.bin[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Init : Accepted[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Execute Secondary Loader[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Init : Loader [2][/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Executing : SYNC[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Reading Device UniqueID, RAM and Flash Chip Info...[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] UNIQUE ID : 23FEE4348281AB2133BEDCFEFDB517A8[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] ERAM Size : 0x000000000003A000 -232 KB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] IRAM Size : 0x00000000C0000000 -3 GB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] eMMC BOOT1 : 0x0000000000400000 -4 MB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] eMMC BOOT2 : 0x0000000000400000 -4 MB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] eMMC RPMB : 0x0000000001000000 -16 MB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] eMMC USER : 0x0000000E8F800000 -58.242 GB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] eMMC CID : 45010044413430363401630AE31467FB - DA4064[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]DA Speed : high-speed[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Reading GPT-EMMC [0x00008000] 130 Items[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Autobackup Partitions[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]-preloader[0x00000000]512 KB ->preloader.bin...Ok[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] -> Renaming Preloader.... preloader_k65v1_64_bsp.bin[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] Creating Scatter file... D:\BST\HydraTool_Fullpackage_02-20-2021\\Backup\Auto\0766__031921192203\MT6765_Android_scatter.txt[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]-pgpt[0x00000000]32 KB ->pgpt.bin...Ok[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]-frp[0x3BD88000]1024 KB ->frp.bin...Ok[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]-nvdata[0x3DE88000]64 MB ->nvdata.bin... Failed[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Startaddress : 3DE88000, CurReadLen :00600006 > 6 MB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Done!!![/SIZE][/FONT]
[FONT=Verdana][SIZE=5]D:\BST\HydraTool_Fullpackage_02-20-2021\\Backup\Auto\0766__031921192203[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]MTK Phone Loader is NOW RUNNING.[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Reading Device UniqueID, RAM and Flash Chip Info...[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]ERROR : ACK : 0x00010009[][/SIZE][/FONT]
[FONT=Verdana][SIZE=5] ERAM Size : 0x000000000003A000 -232 KB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] IRAM Size : 0x00000000C0000000 -3 GB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] eMMC BOOT1 : 0x0000000000400000 -4 MB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] eMMC BOOT2 : 0x0000000000400000 -4 MB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] eMMC RPMB : 0x0000000001000000 -16 MB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] eMMC USER : 0x0000000E8F800000 -58.242 GB[/SIZE][/FONT]
[FONT=Verdana][SIZE=5] eMMC CID : 45010044413430363401630AE31467FB - DA4064[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Reading GPT-EMMC [0x00008000] 130 Items[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]
[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]-------------------------------------[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Operation : Auto[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Processing...[/SIZE][/FONT]
[FONT=Verdana][SIZE=5]ZeroWipe FRP Partition...[00000004-][/SIZE][/FONT]
[FONT=Verdana][SIZE=5]Erasing FRP Partition... Ok[/SIZE][/FONT]
[FONT=Verdana][/FONT]
[FONT=Verdana][SIZE=5]Elapsed Time : 00:00:33
