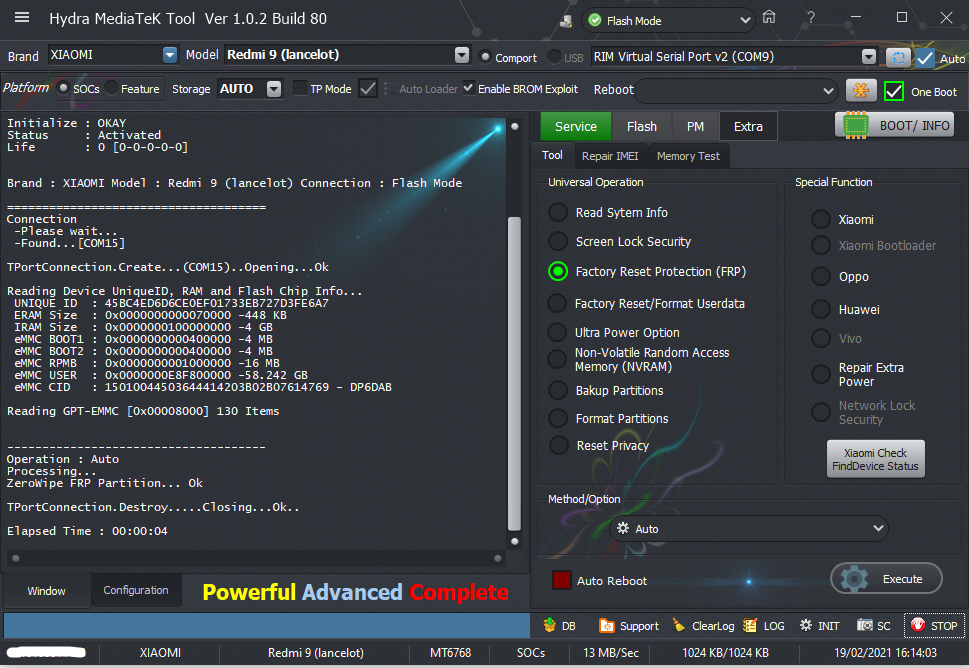
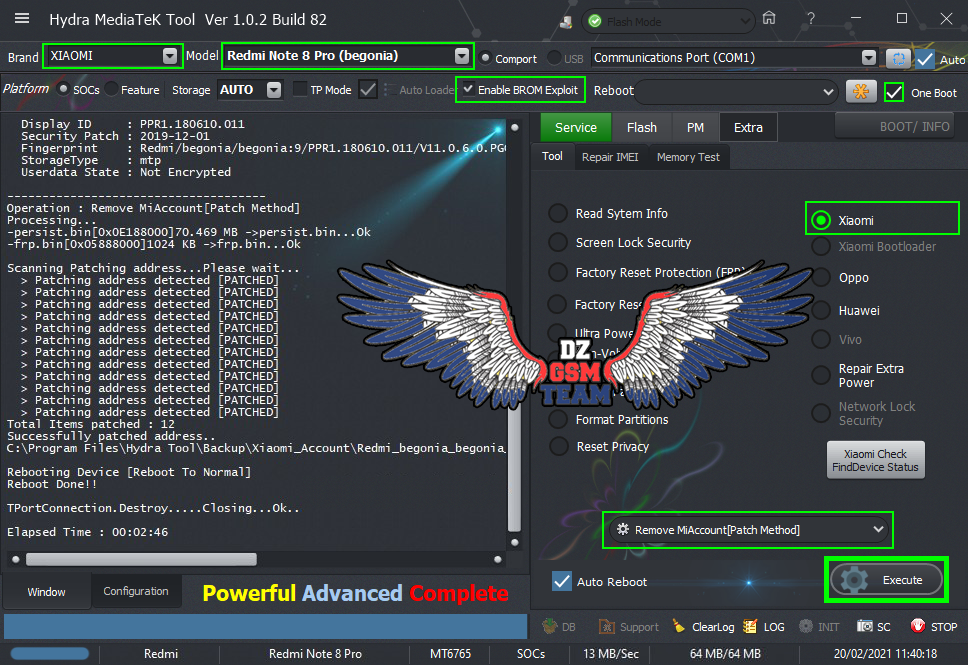
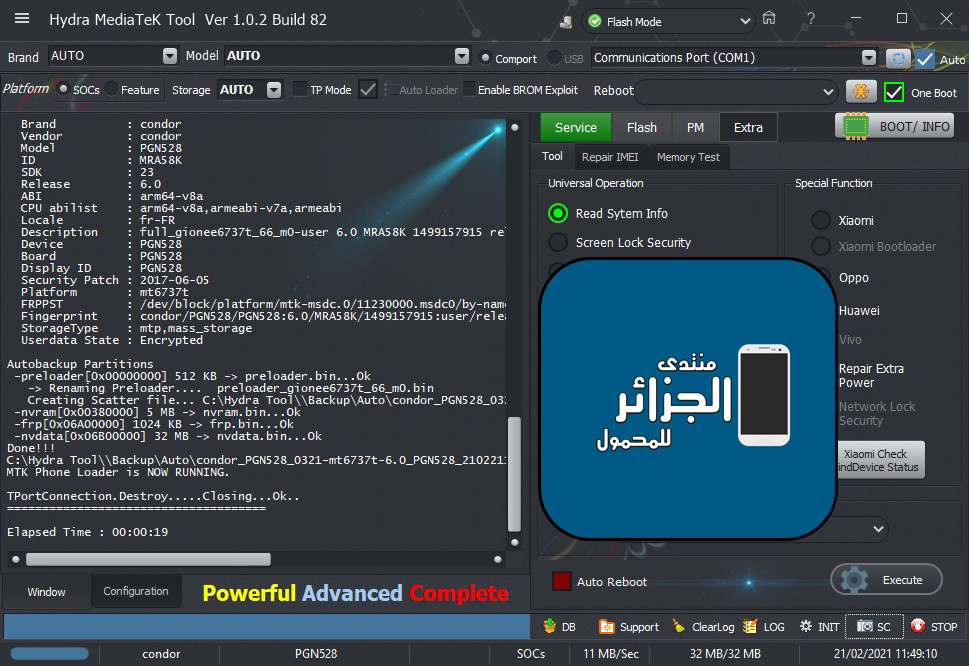
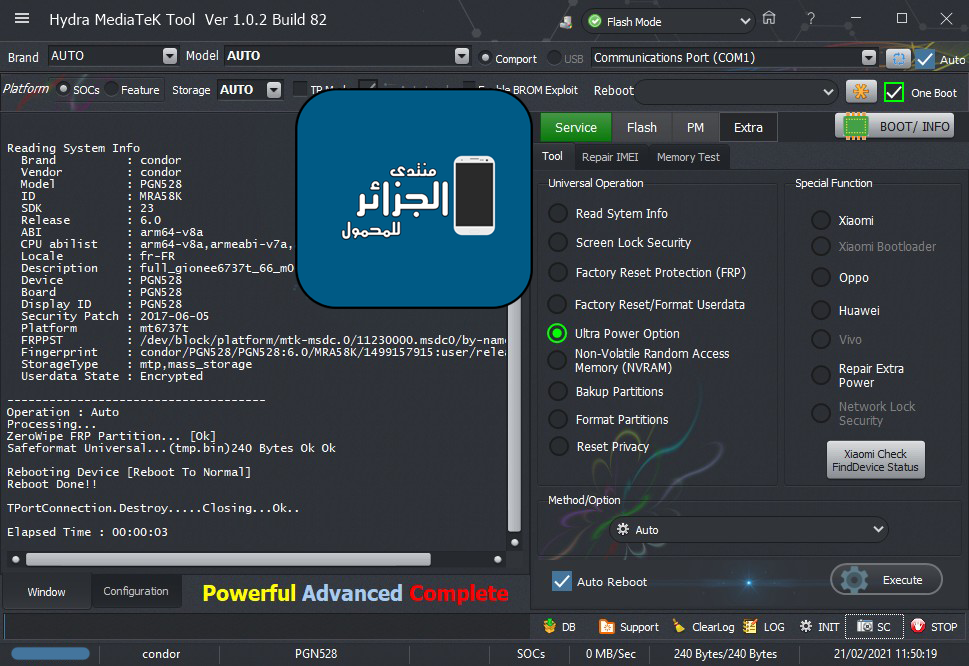
رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Lenovo C2 (K10a40) Ultra Power Option
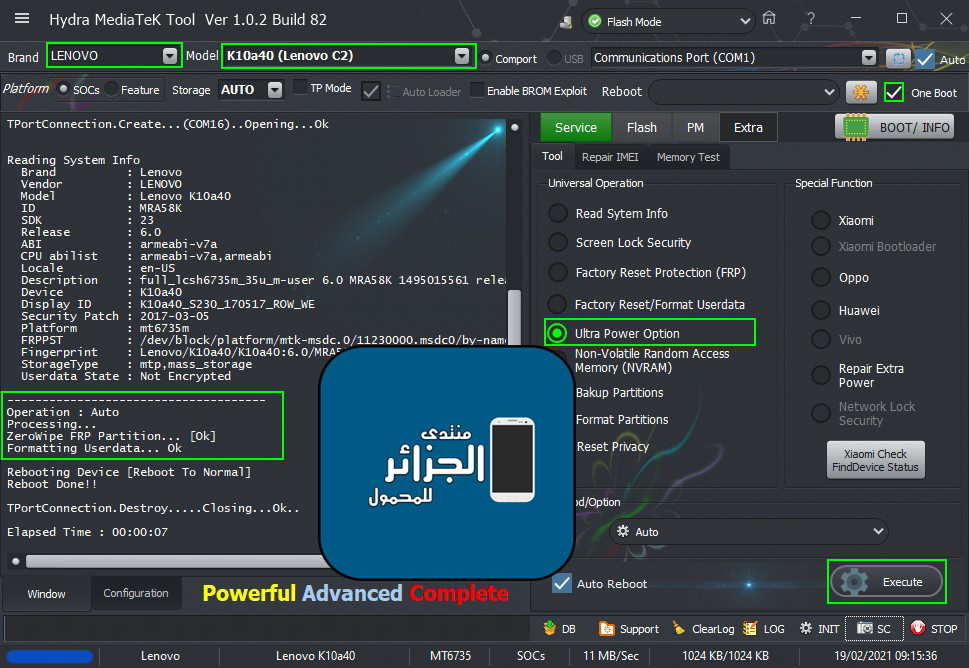
Lenovo C2 (K10a40) Ultra Power Option

كود:
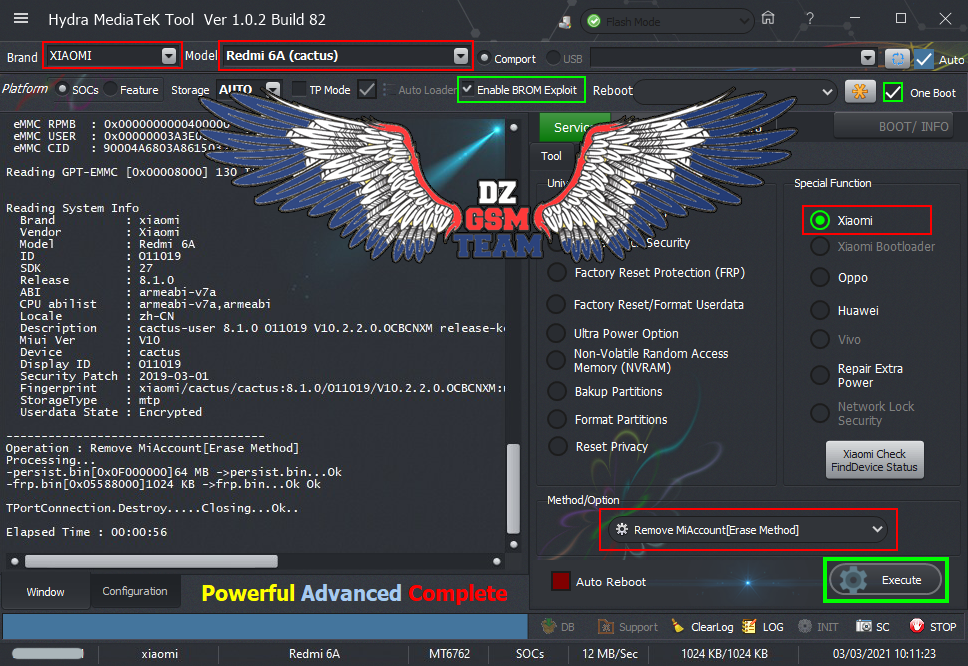
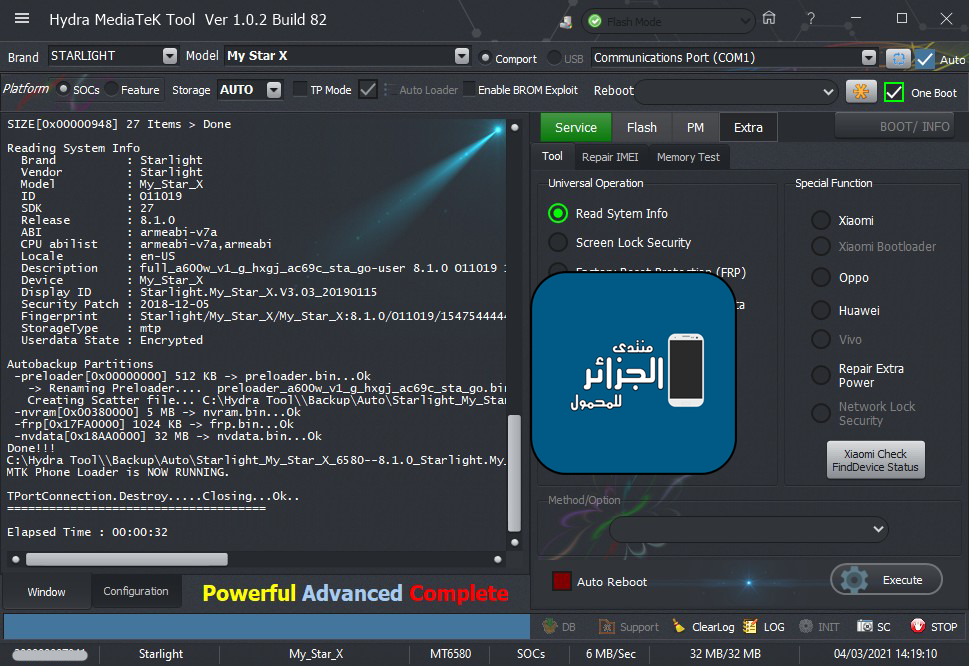
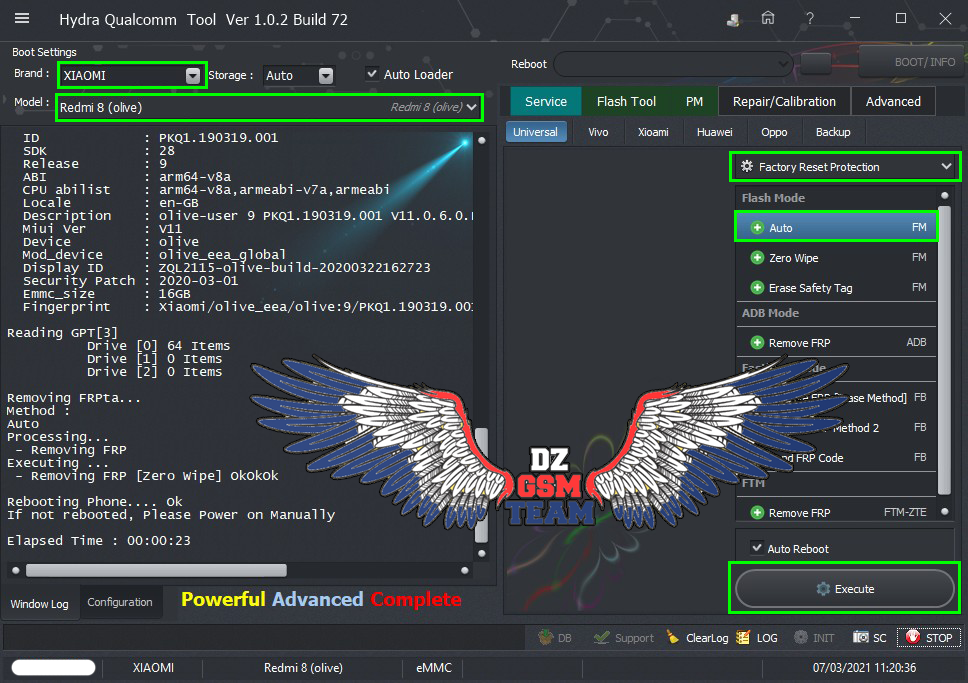
[B][FONT=Arial Black][SIZE=2]Brand : LENOVO Model : K10a40 (Lenovo C2) Connection : Flash Mode
=====================================
Connection
-Please wait...
-Found...[COM16]
TPortConnection.Create...(COM16)..Opening...Ok
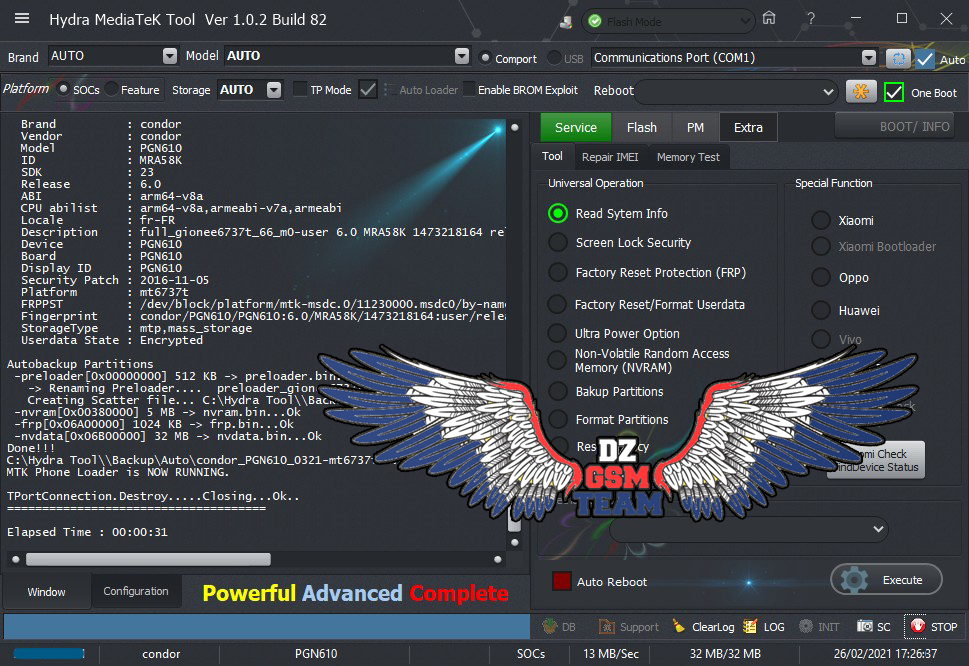
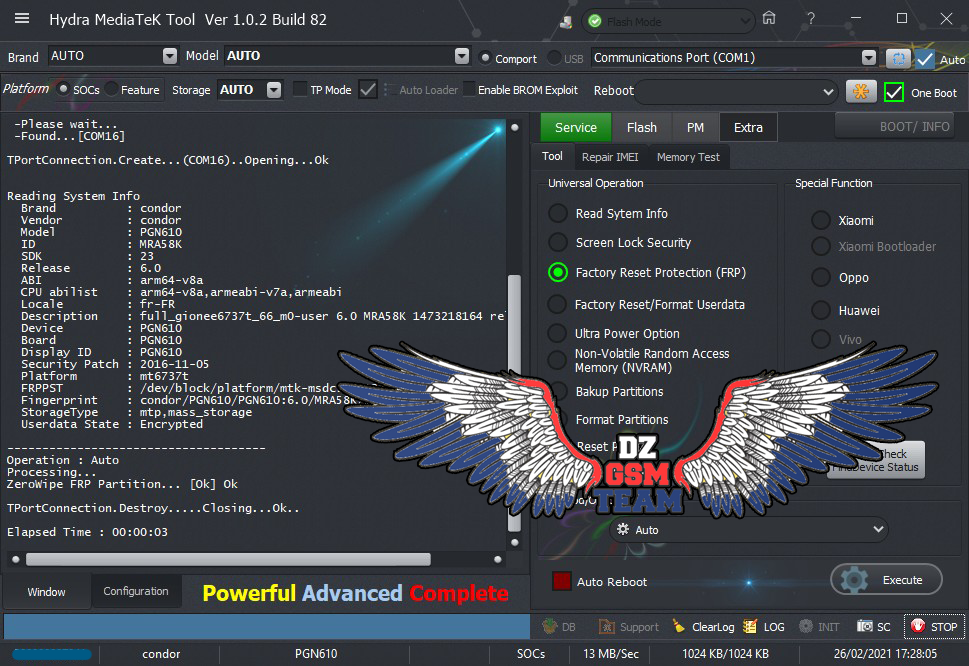
Reading System Info
Brand : Lenovo
Vendor : LENOVO
Model : Lenovo K10a40
ID : MRA58K
SDK : 23
Release : 6.0
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-US
Description : full_lcsh6735m_35u_m-user 6.0 MRA58K 1495015561 release-keys
Device : K10a40
Display ID : K10a40_S230_170517_ROW_WE
Security Patch : 2017-03-05
Platform : mt6735m
FRPPST : /dev/block/platform/mtk-msdc.0/11230000.msdc0/by-name/frp
Fingerprint : Lenovo/K10a40/K10a40:6.0/MRA58K/K10a40_S230_170517_ROW_WE:user/release-keys
StorageType : mtp,mass_storage
Userdata State : Not Encrypted
-------------------------------------
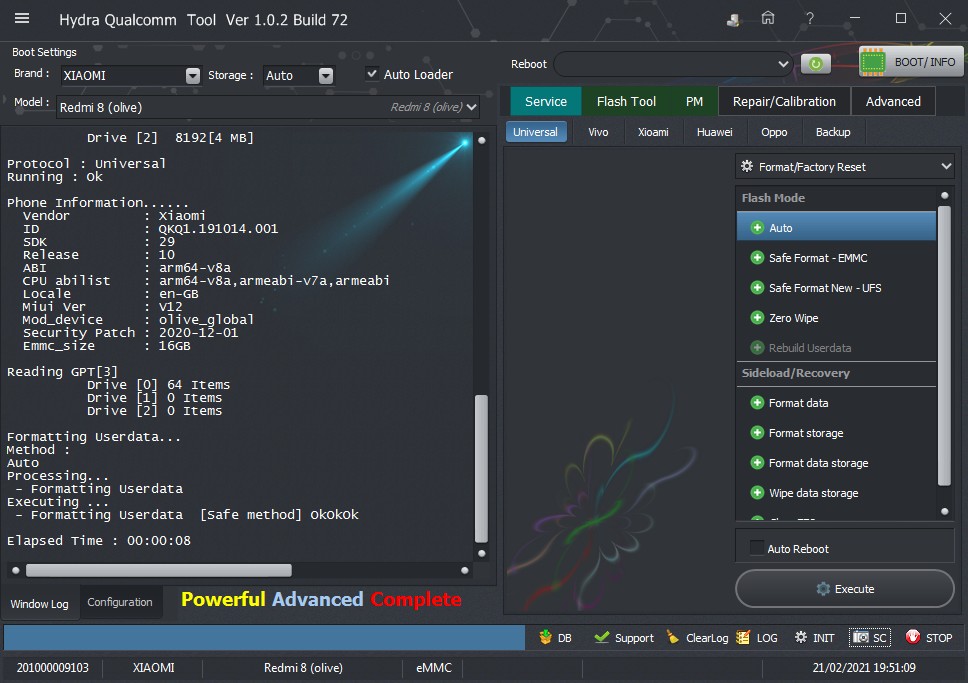
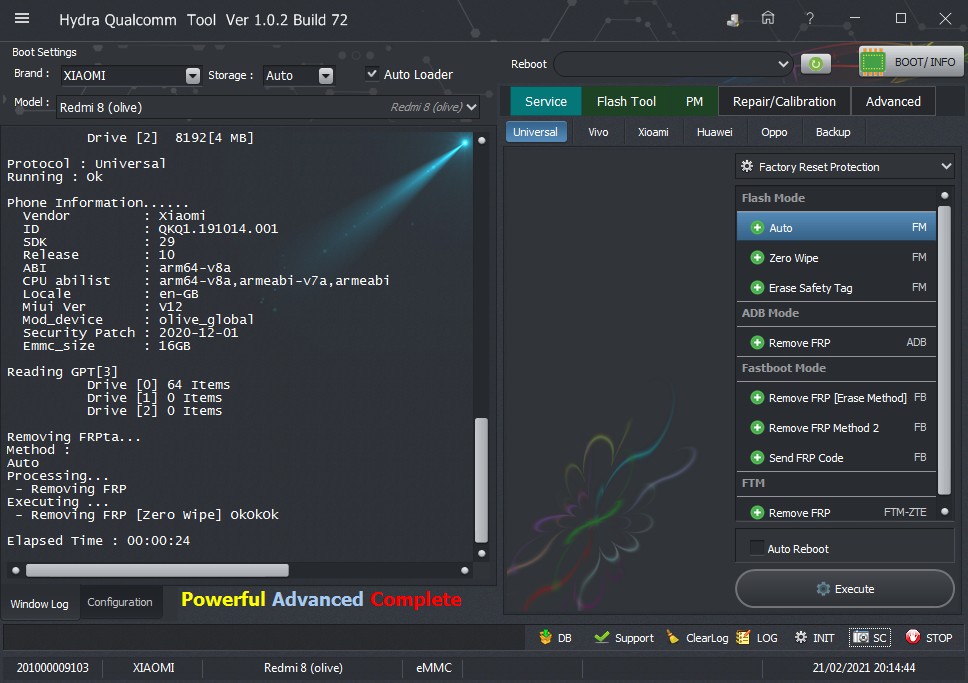
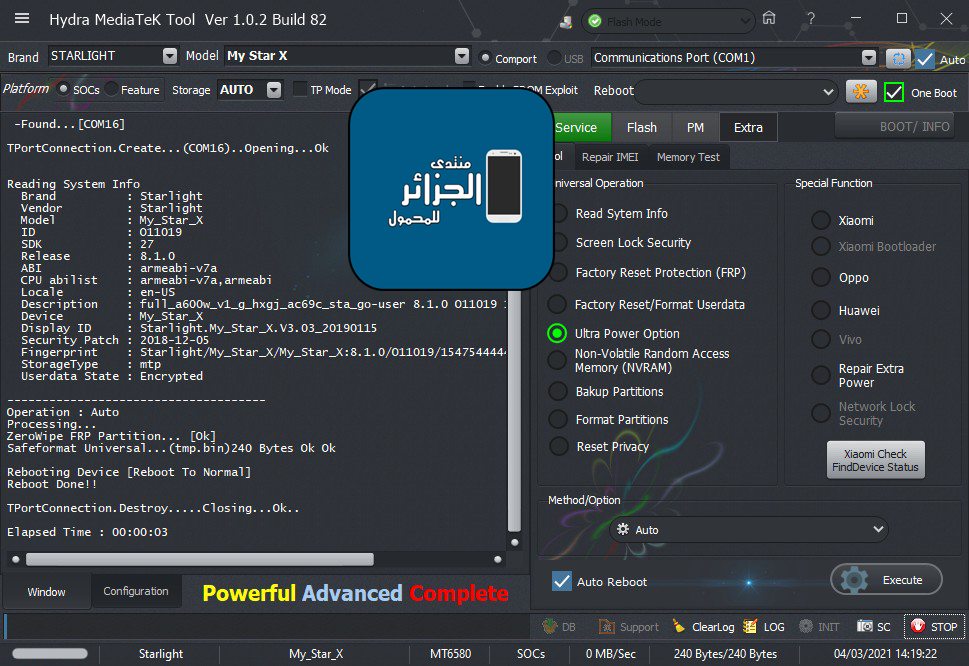
Operation : Auto
Processing...
ZeroWipe FRP Partition... [Ok]
Formatting Userdata... Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
TPortConnection.Destroy.....Closing...Ok..
Elapsed Time : 00:00:07
[/SIZE][/FONT][/B]