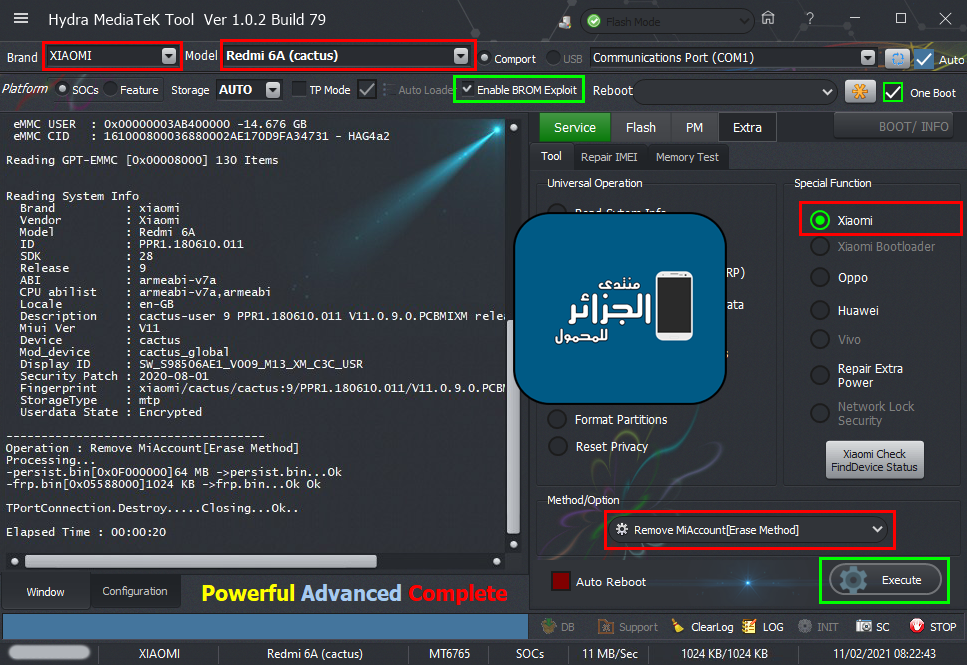
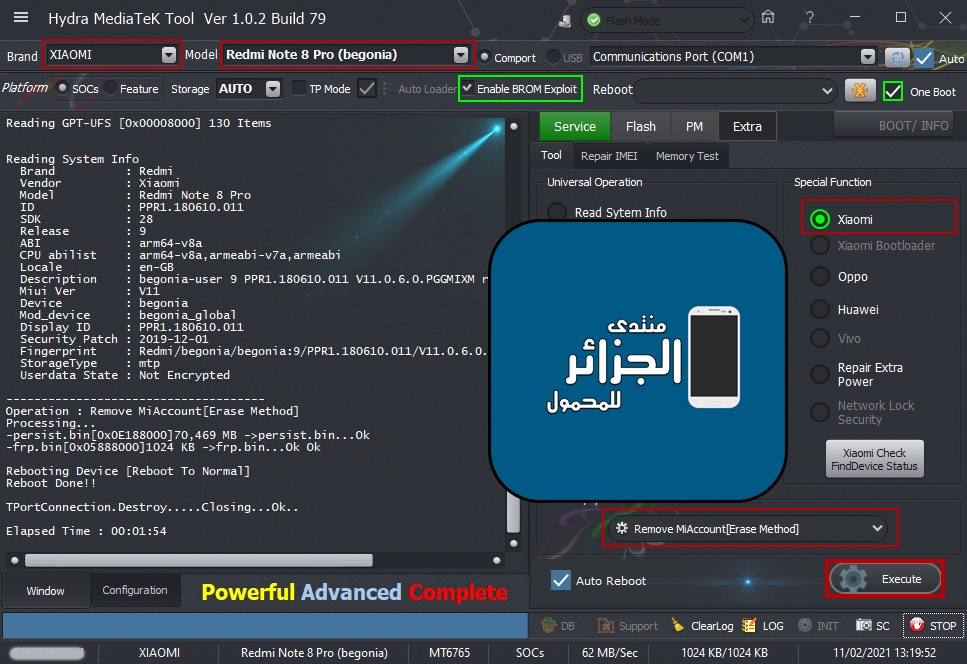
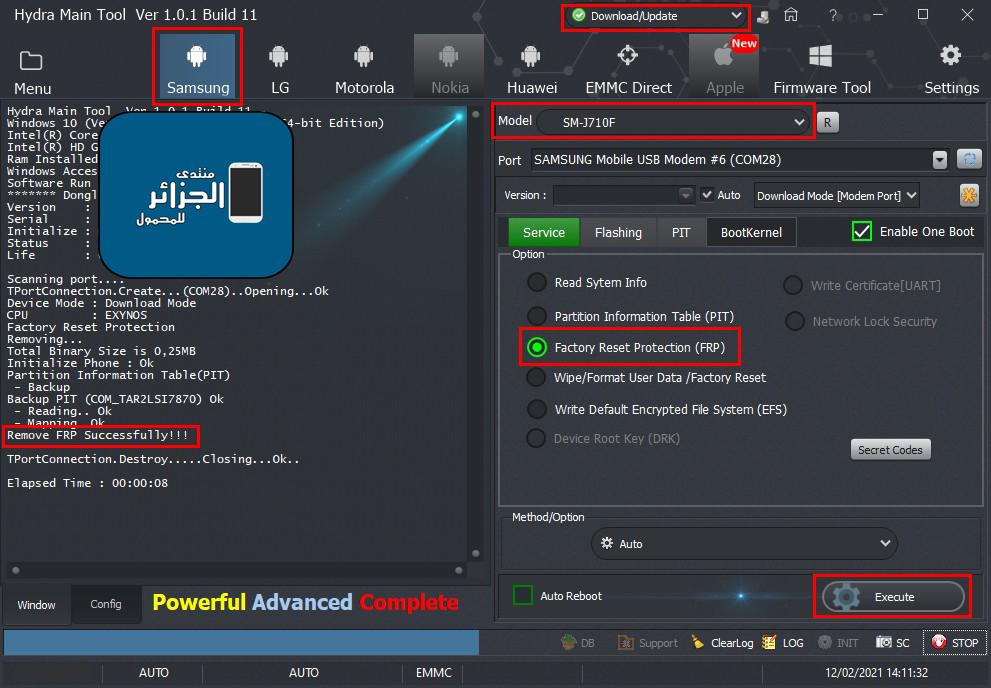
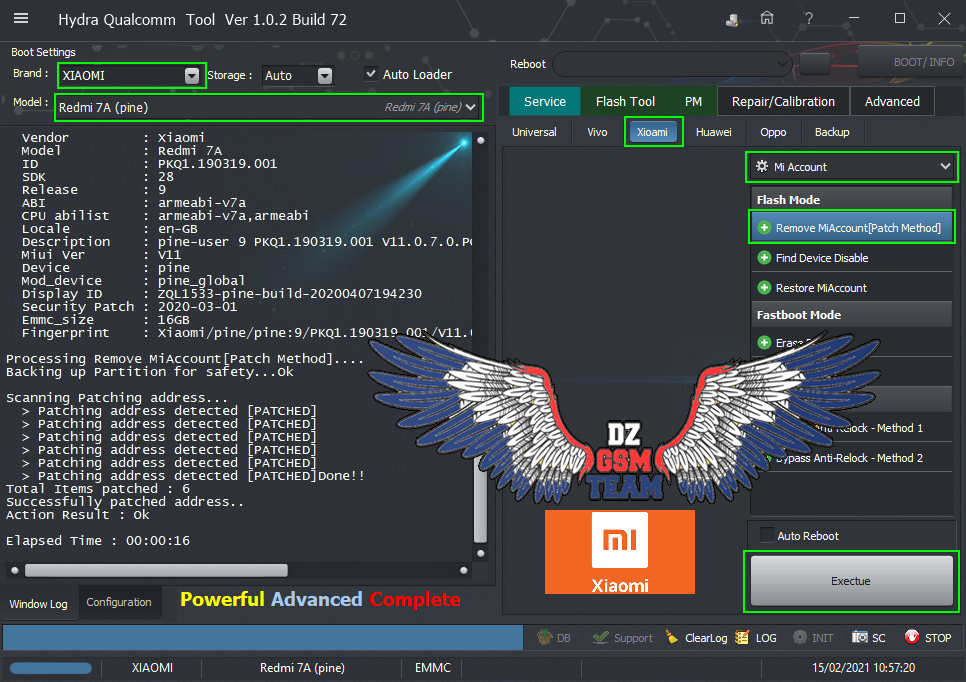
رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
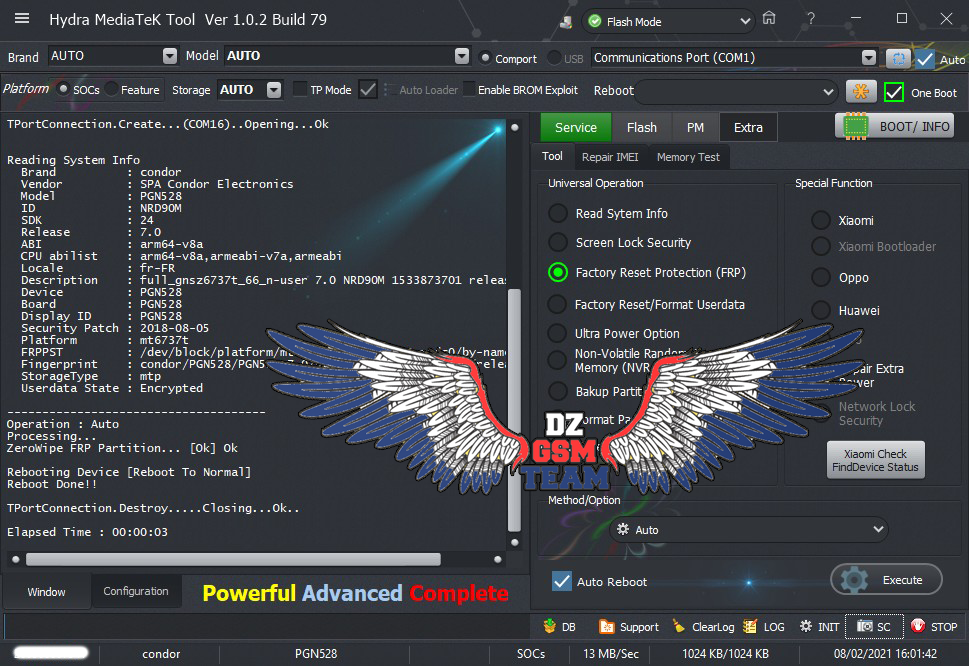
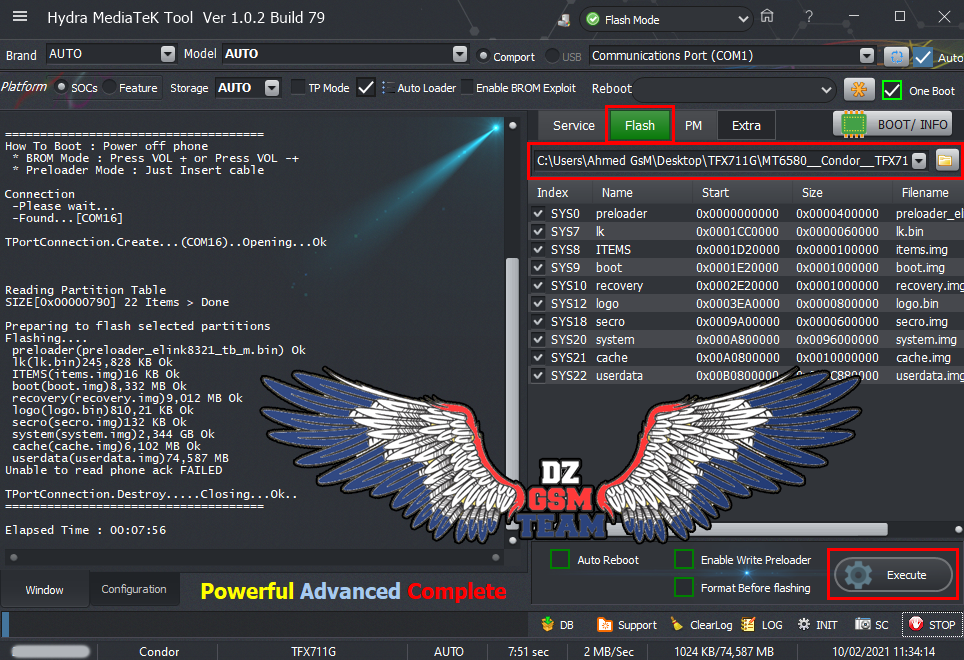
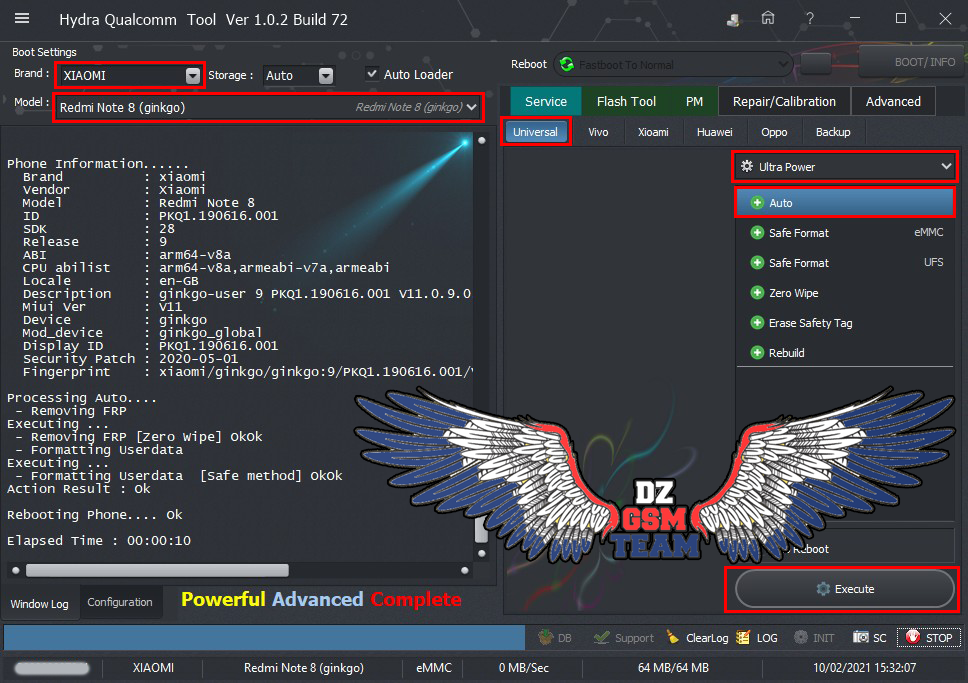
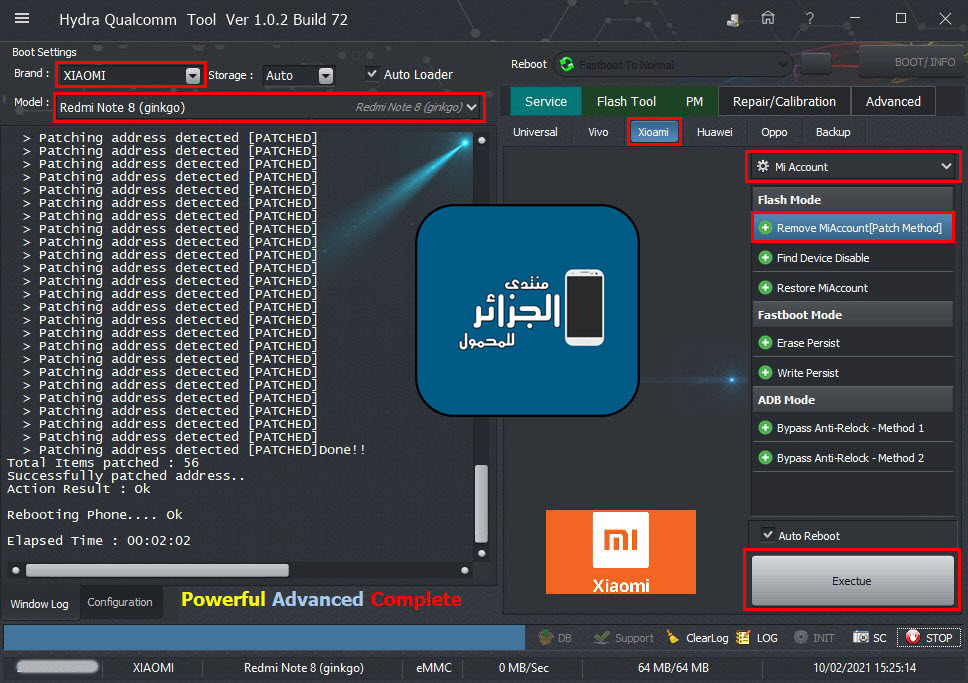
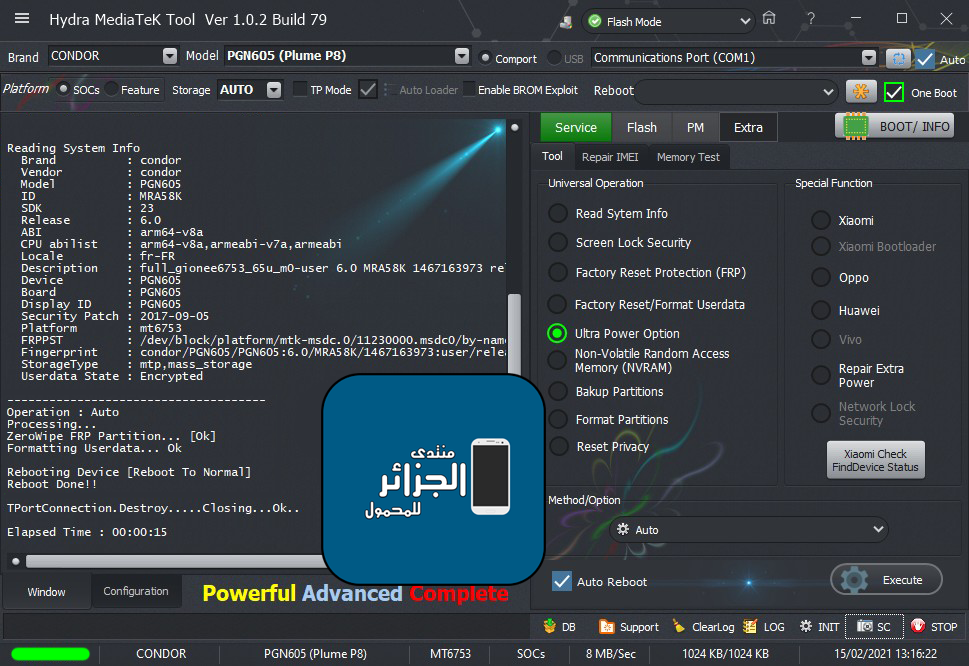
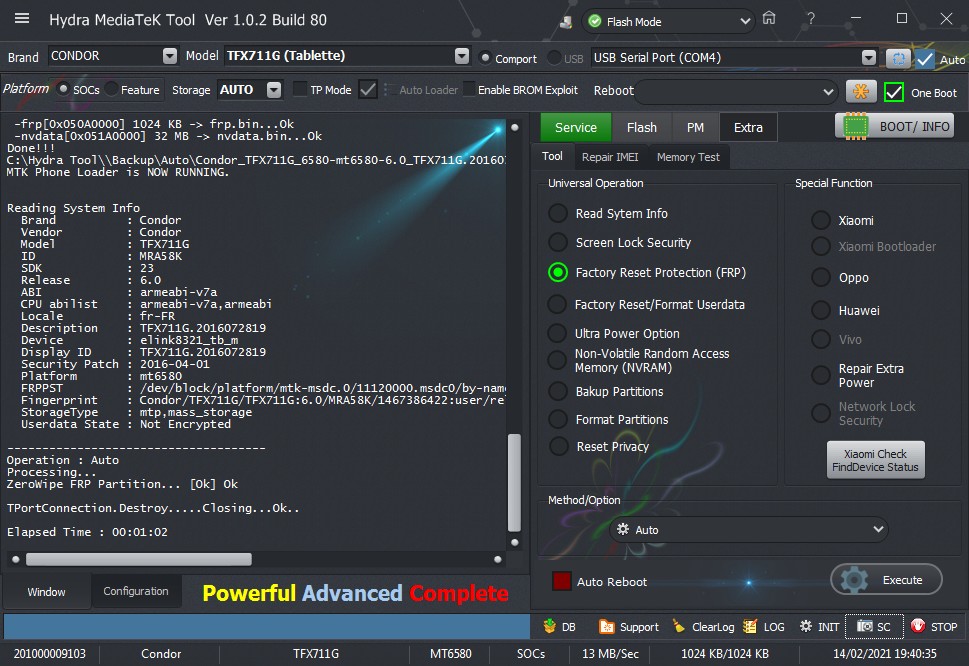
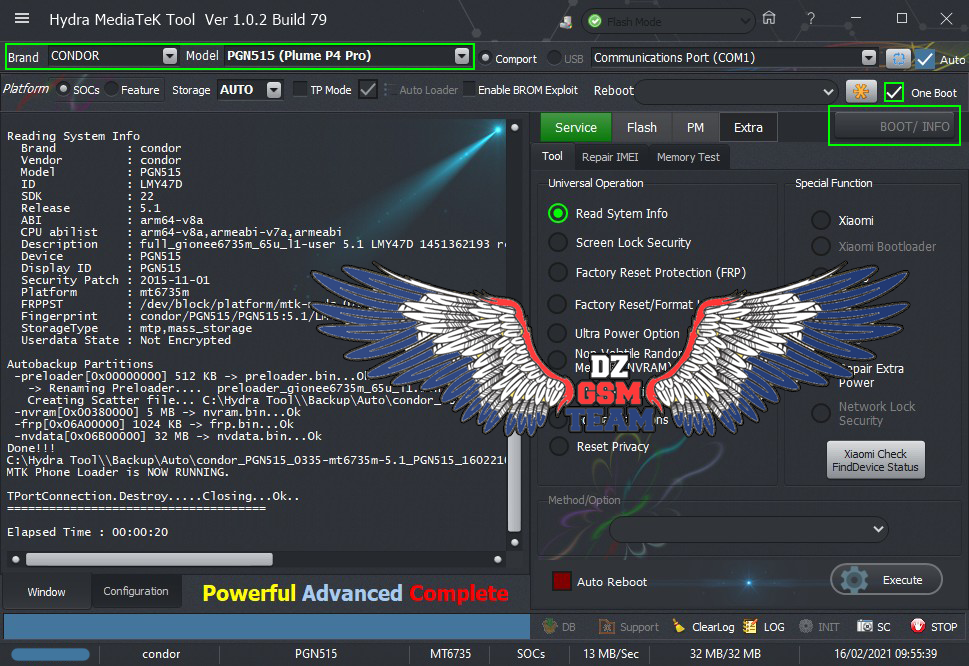
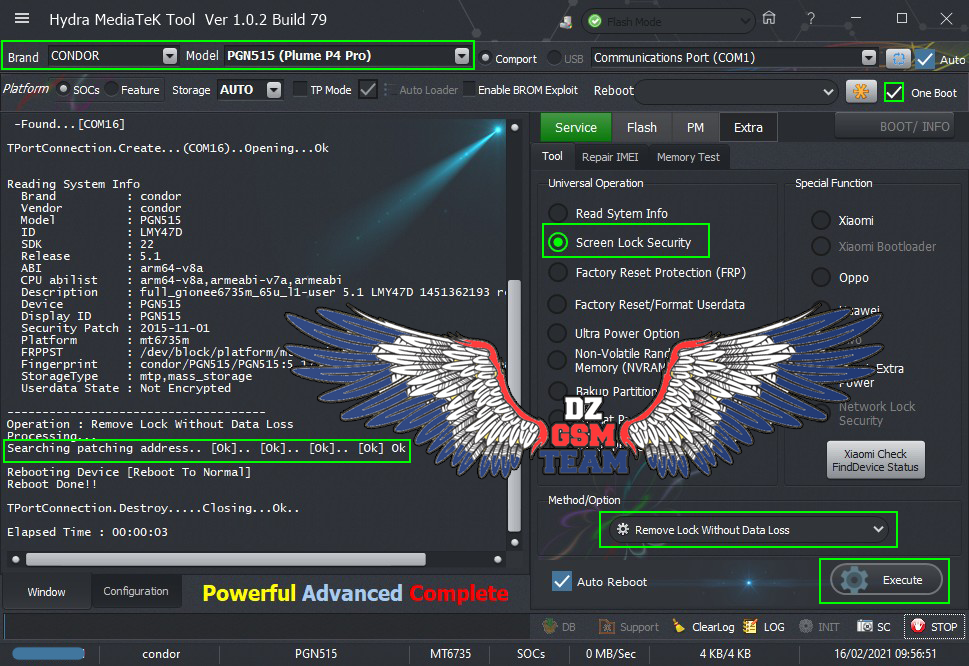
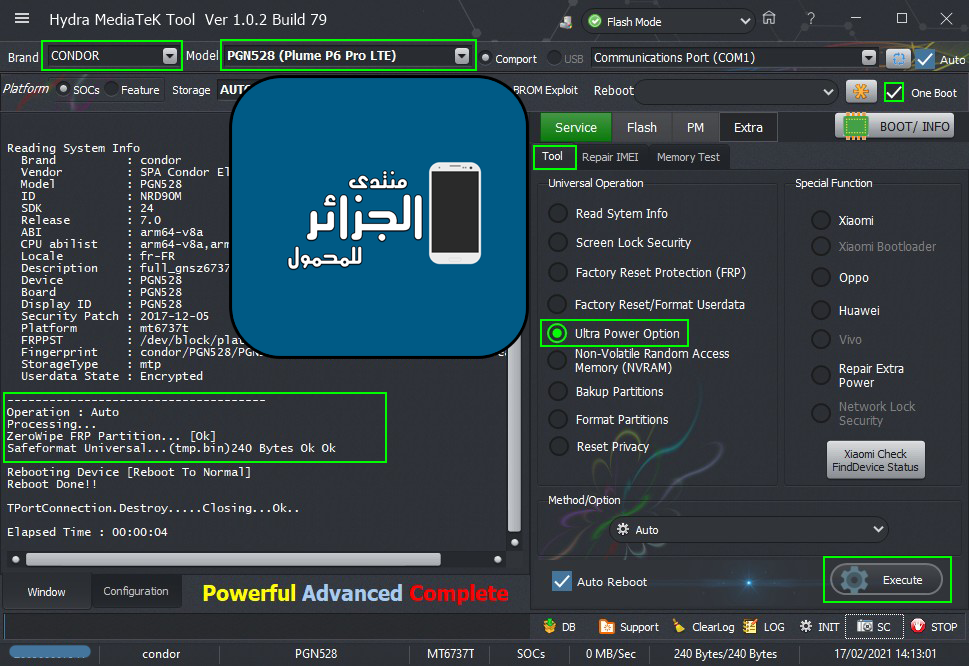
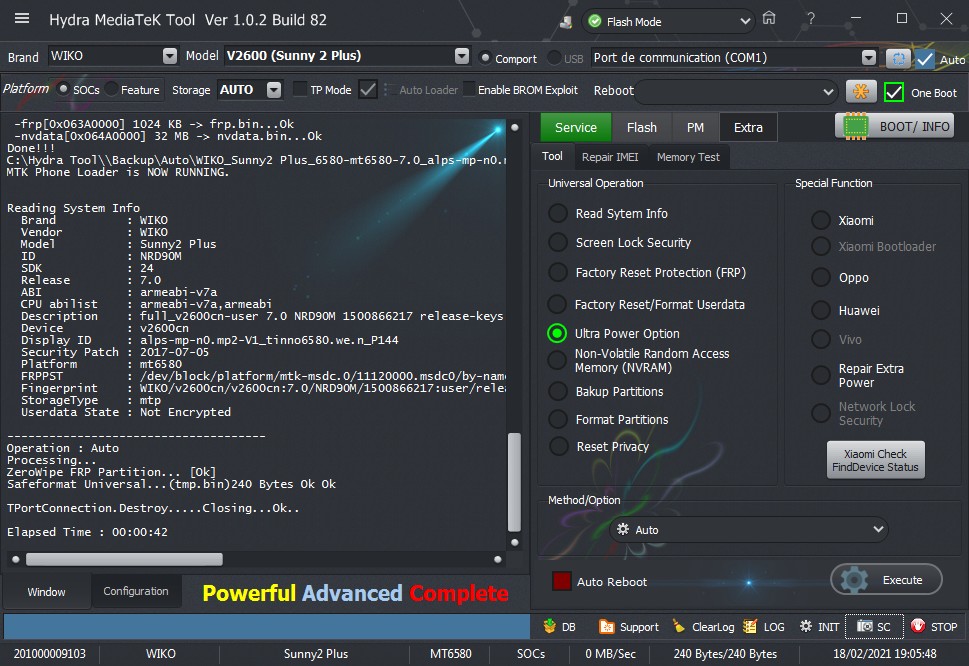
Condor T9 (SP648) Ultra Power Option
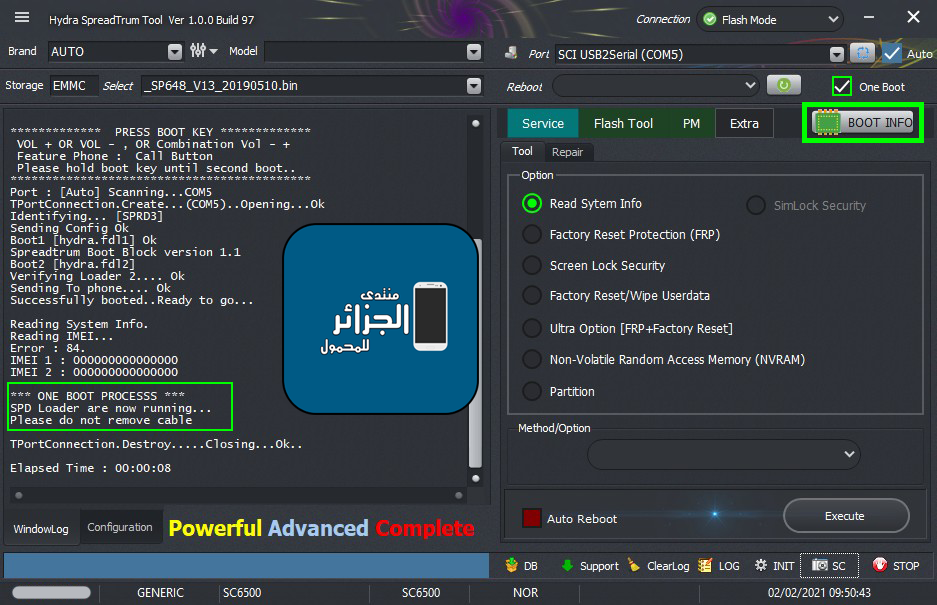
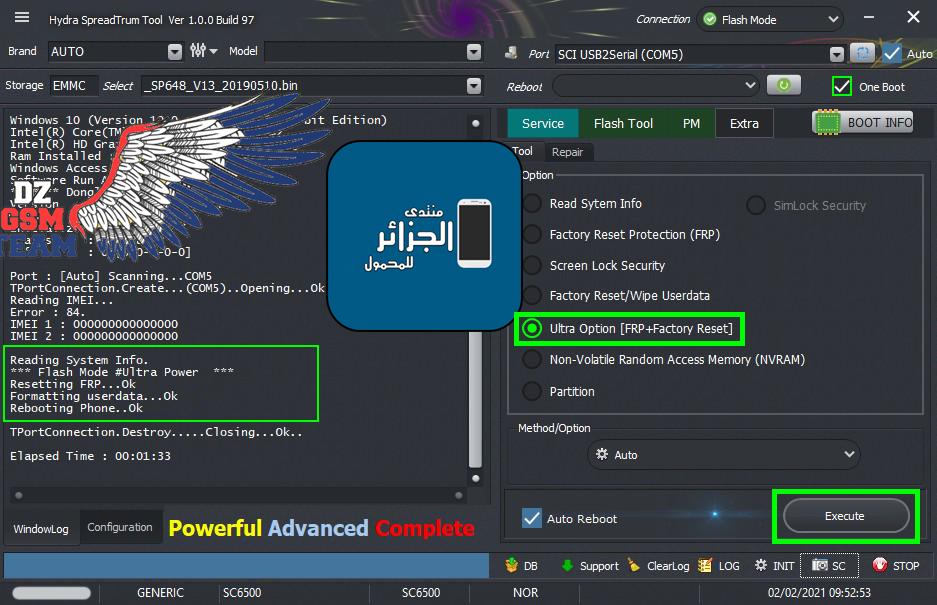
Condor T9 (SP648) Ultra Power Option

كود:
[B][FONT=Arial Black][SIZE=2]************* PRESS BOOT KEY *************
VOL + OR VOL - , OR Combination Vol - +
Feature Phone : Call Button
Please hold boot key until second boot..
*******************************************
Port : [Auto] Scanning...COM5
TPortConnection.Create...(COM5)..Opening...Ok
Identifying... [SPRD3]
Sending Config Ok
Boot1 [hydra.fdl1] Ok
Spreadtrum Boot Block version 1.1
Boot2 [hydra.fdl2]
Verifying Loader 2.... Ok
Sending To phone.... Ok
Successfully booted..Ready to go...
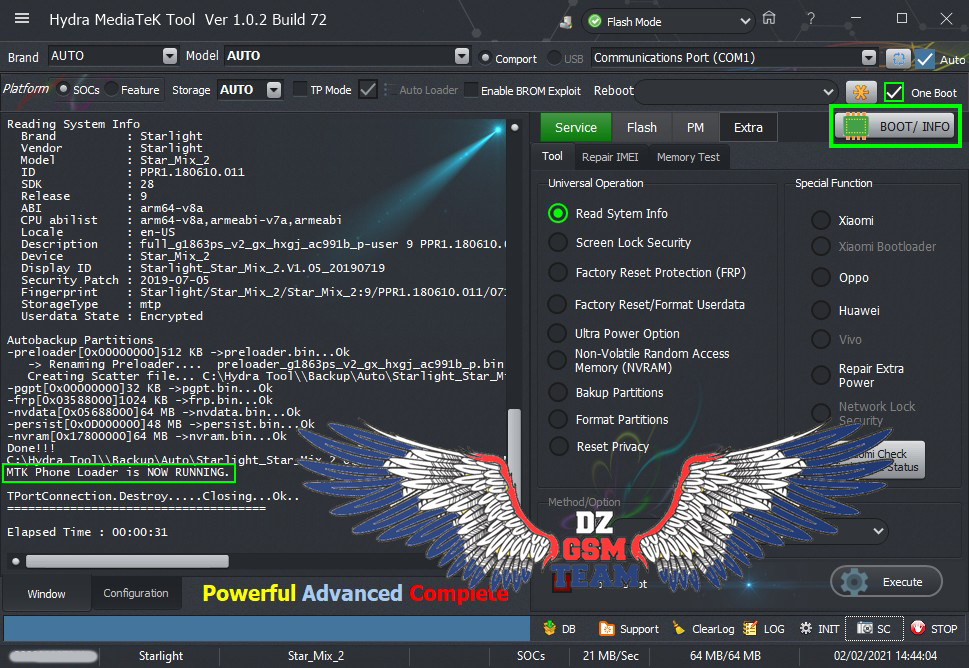
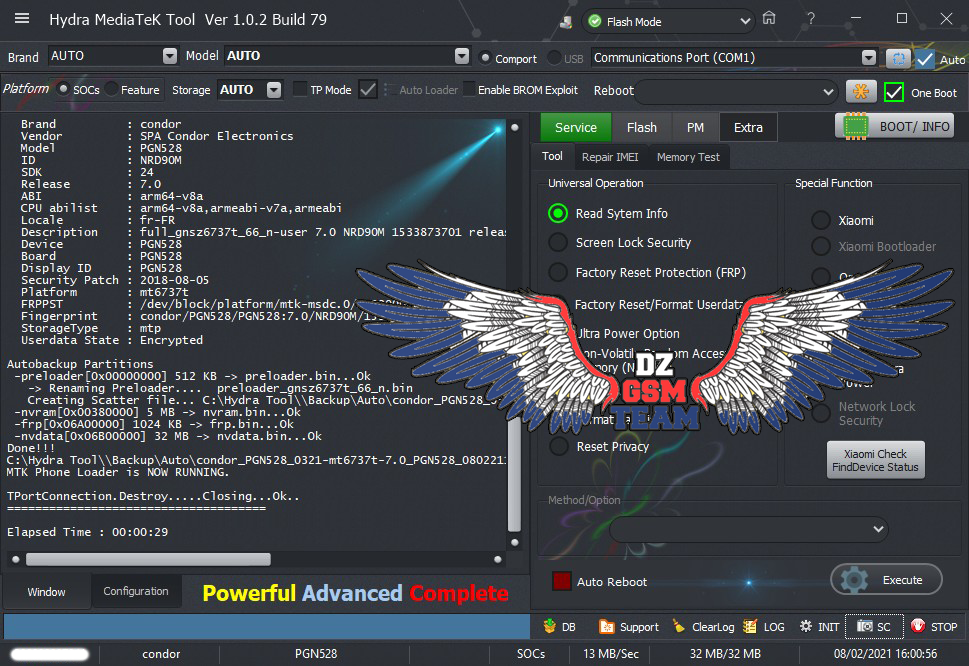
Reading System Info.
Reading IMEI...
Error : 84.
IMEI 1 : 000000000000000
IMEI 2 : 000000000000000
[COLOR="#008000"]*** ONE BOOT PROCESSS ***
SPD Loader are now running...
Please do not remove cable
[/COLOR]
TPortConnection.Destroy.....Closing...Ok..
Elapsed Time : 00:00:14
[/SIZE][/FONT][/B]
كود:
[B][FONT=Arial Black][SIZE=2]Port : [Auto] Scanning...COM5
TPortConnection.Create...(COM5)..Opening...Ok
Reading IMEI...
Error : 84.
IMEI 1 : 000000000000000
IMEI 2 : 000000000000000
Reading System Info.
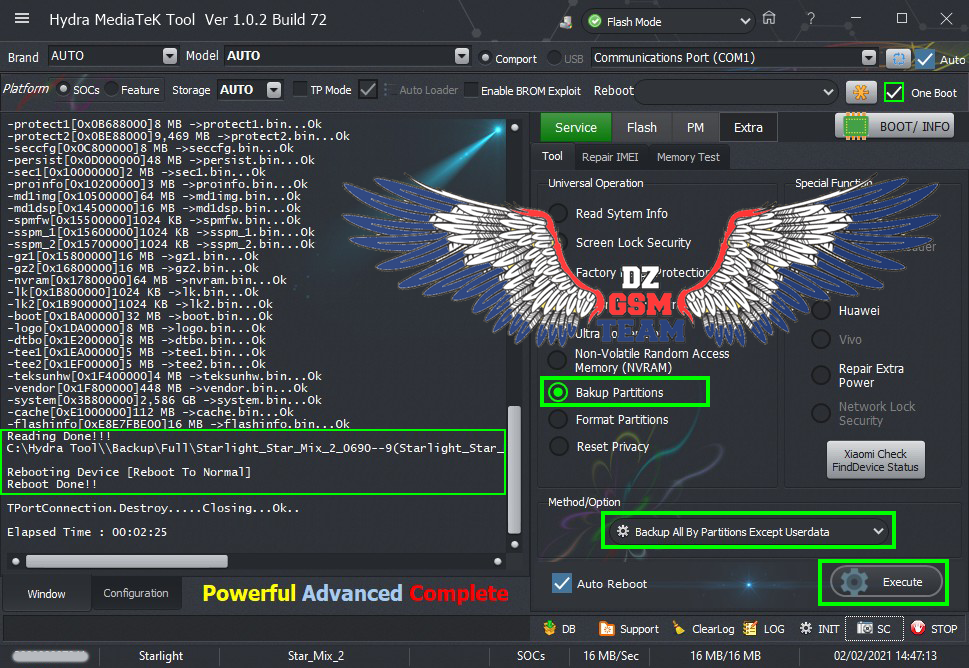
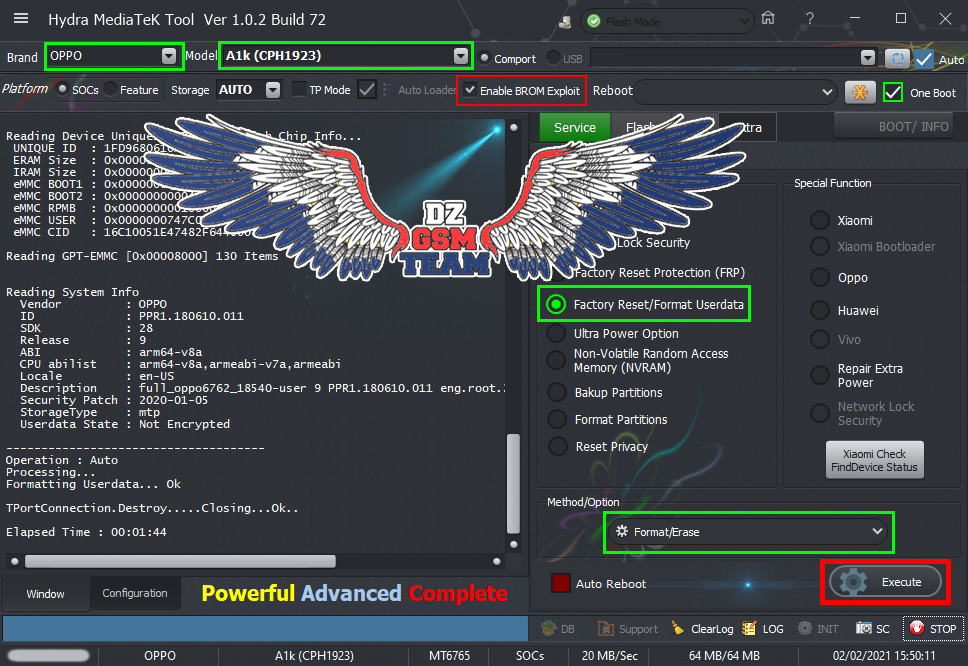
[COLOR="#008000"]*** Flash Mode #Ultra Power ***
Resetting FRP...Ok
Formatting userdata...Ok
Rebooting Phone..Ok
[/COLOR]
TPortConnection.Destroy.....Closing...Ok..
Elapsed Time : 00:01:33
[/SIZE][/FONT][/B]