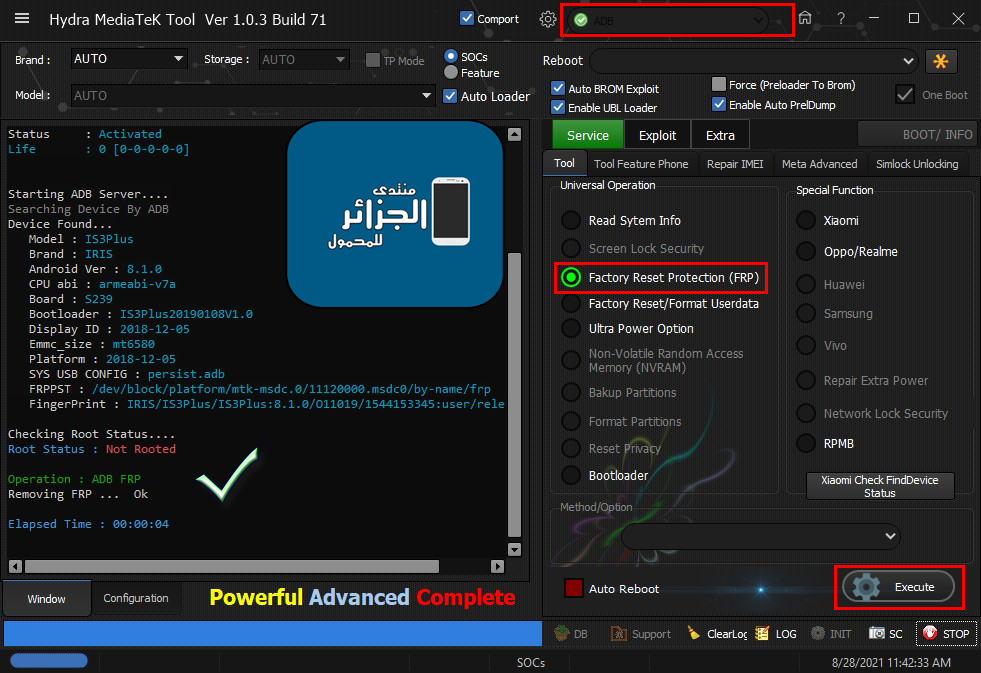
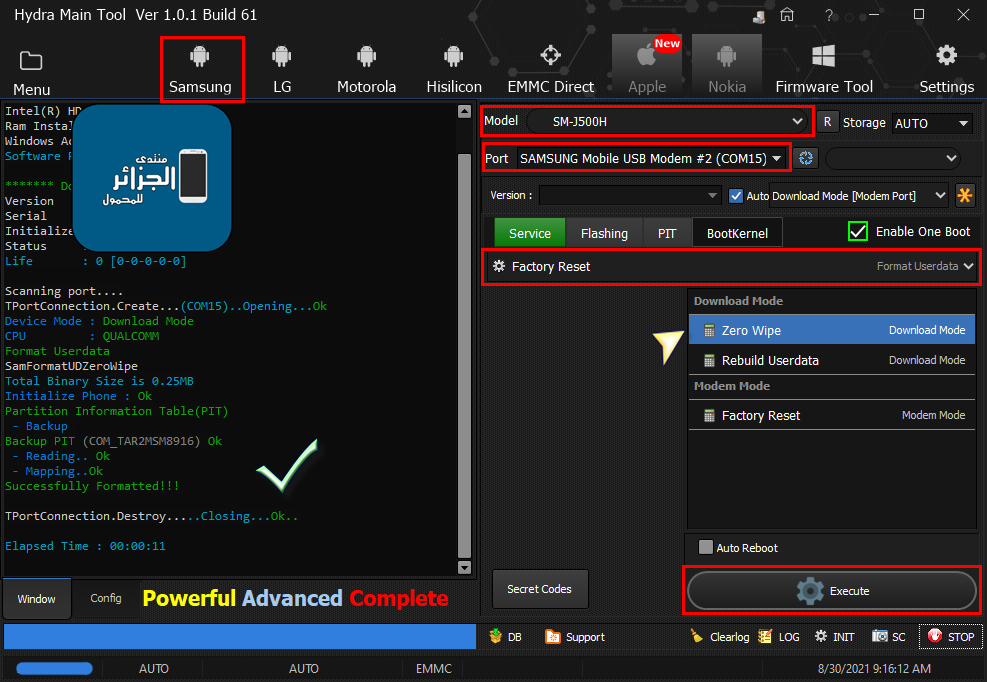
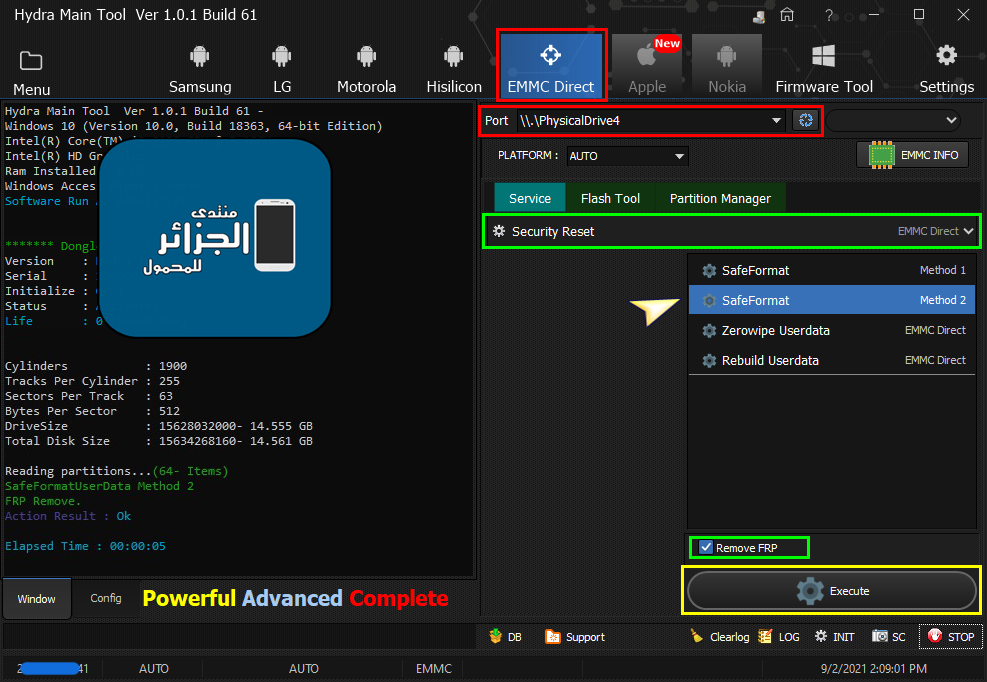
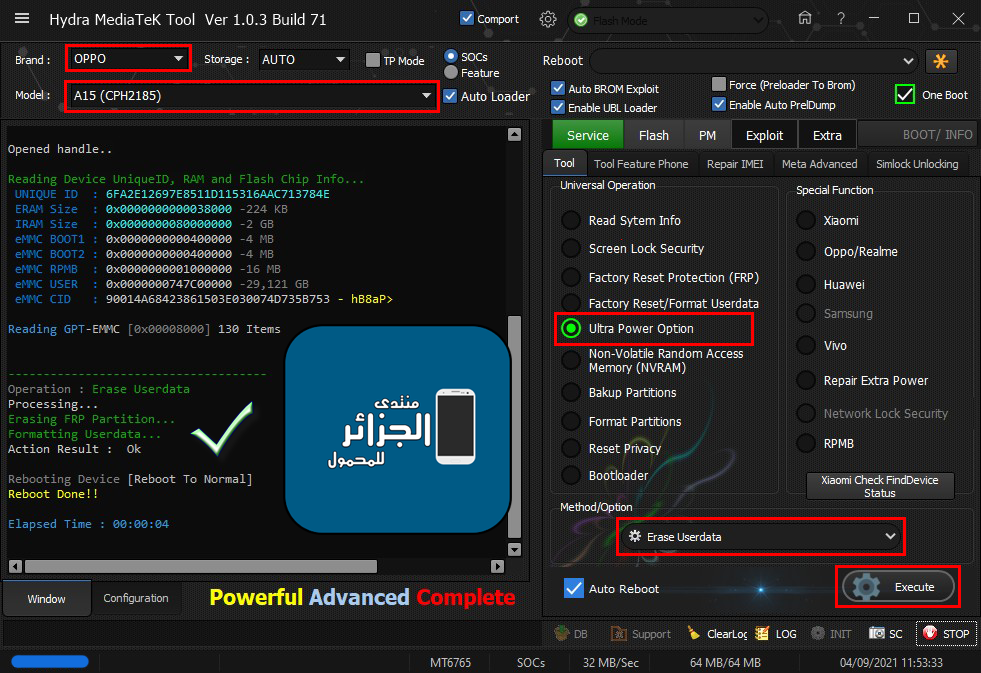
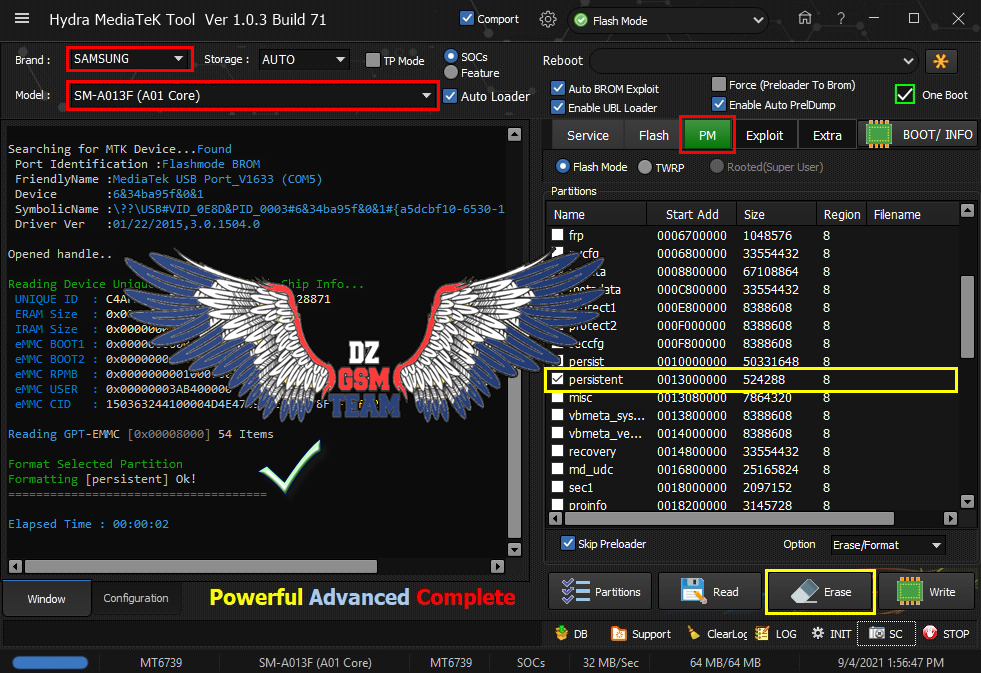
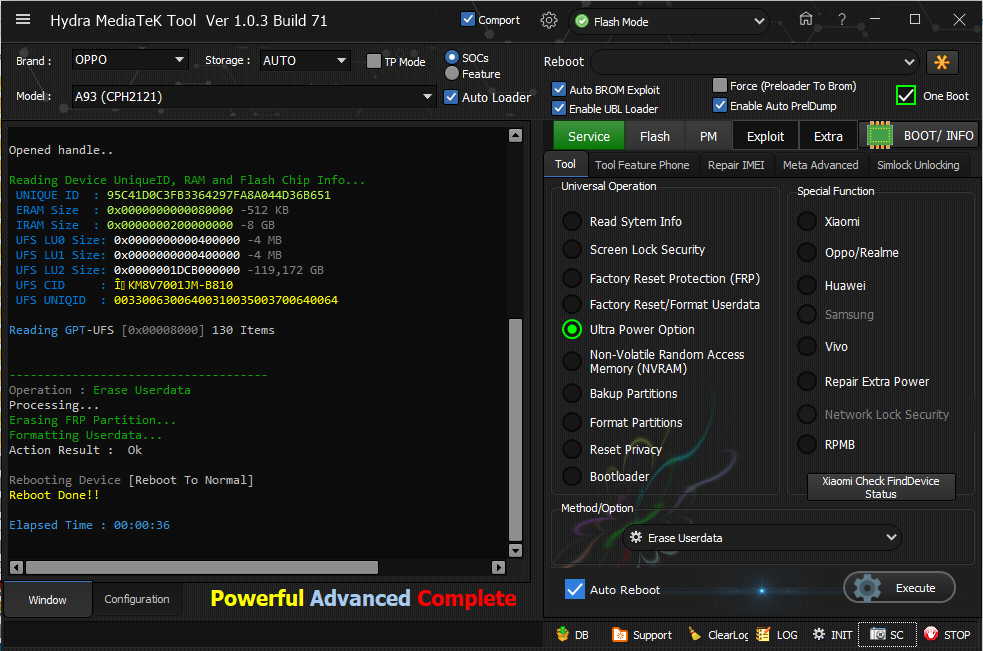
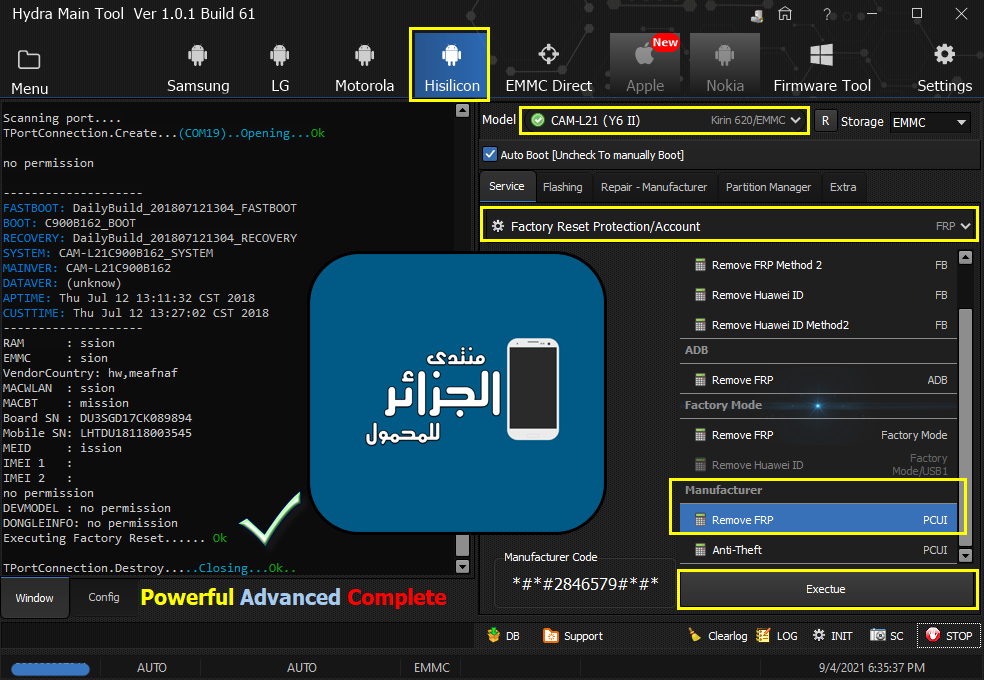
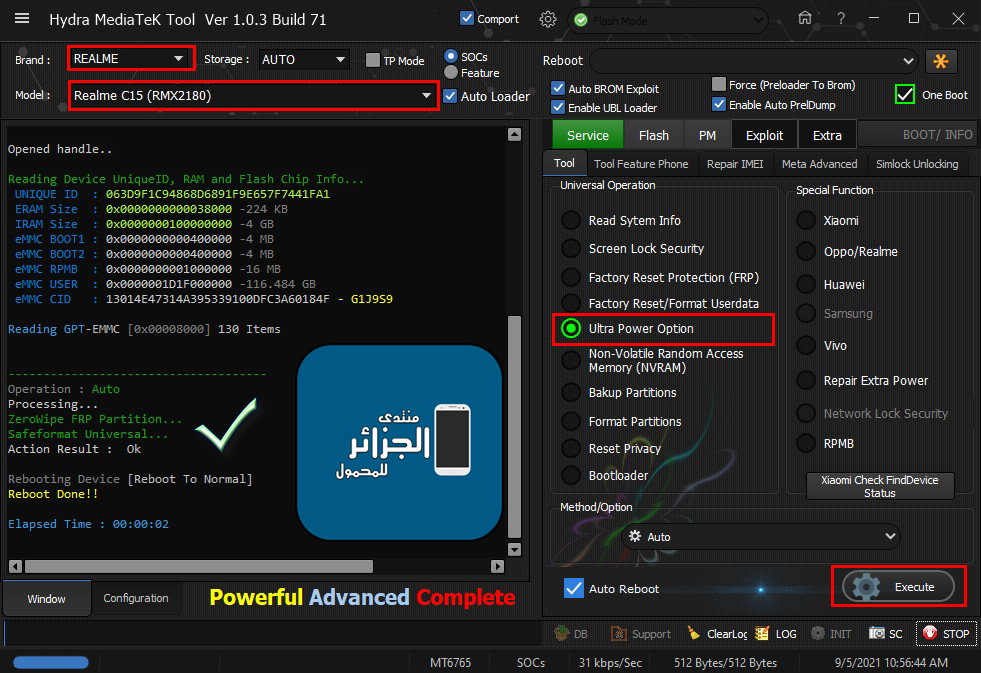
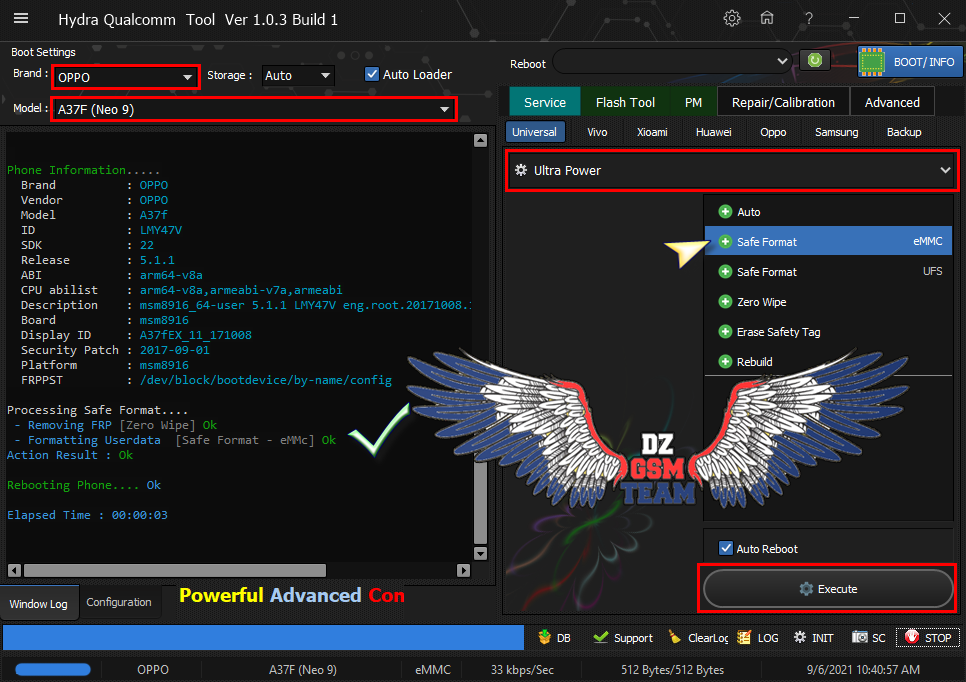
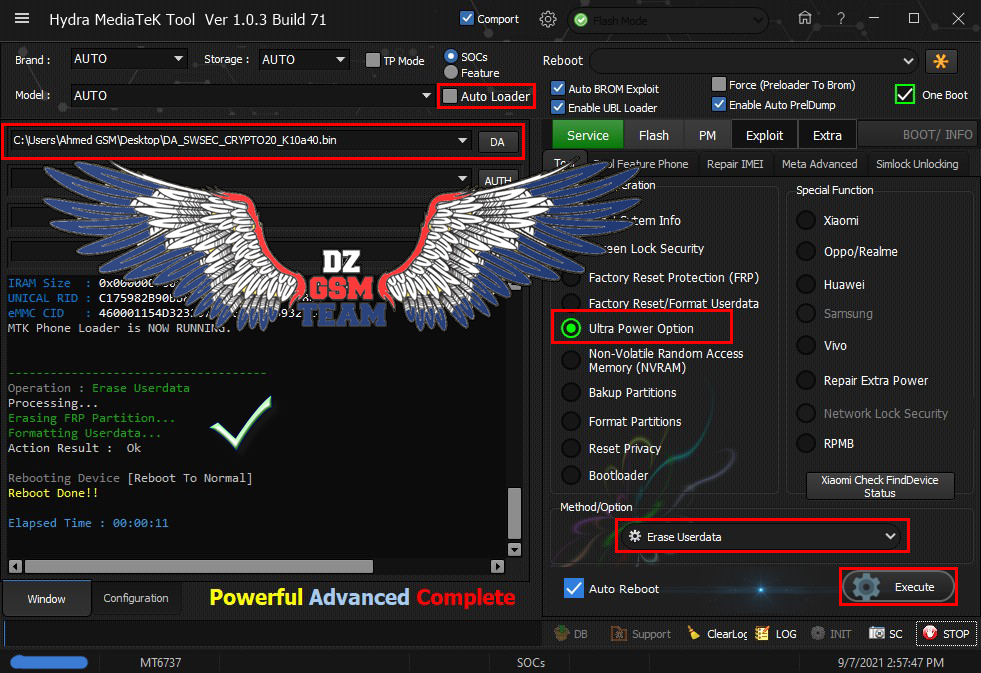
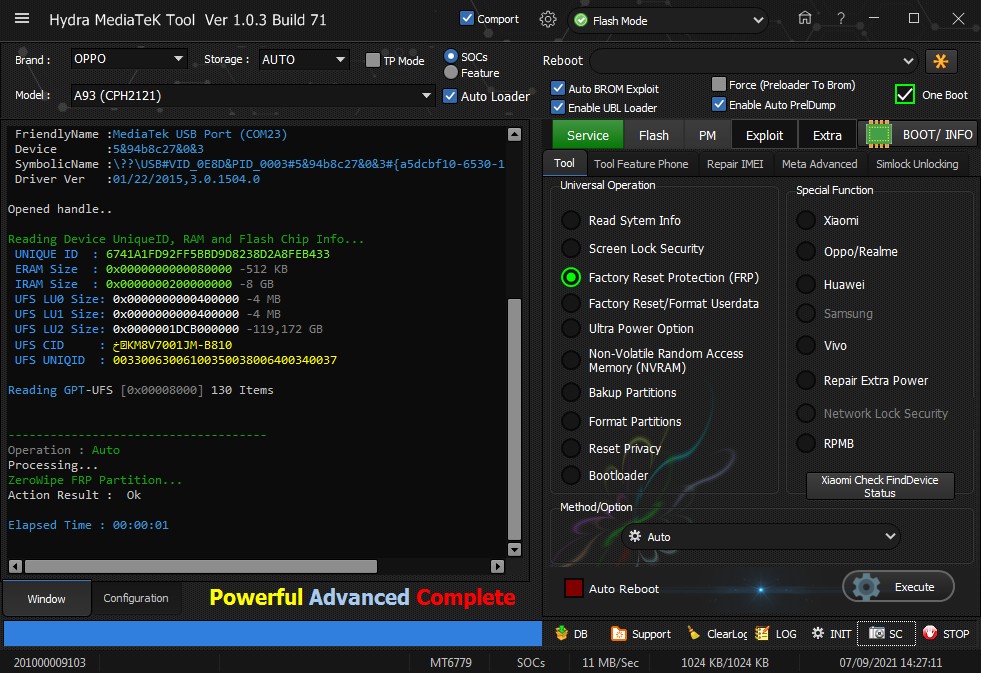
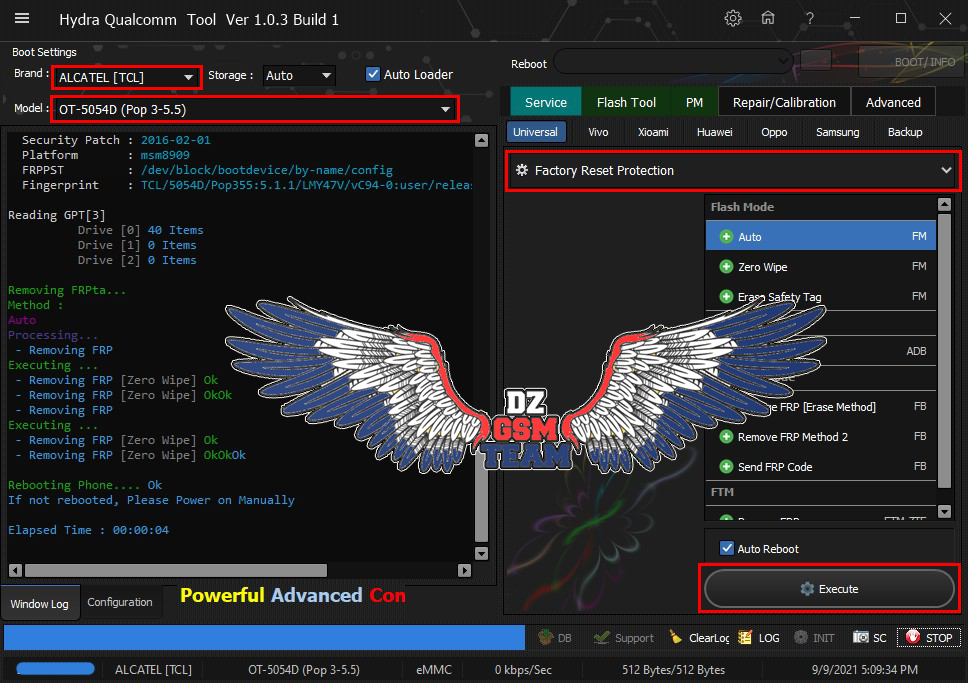
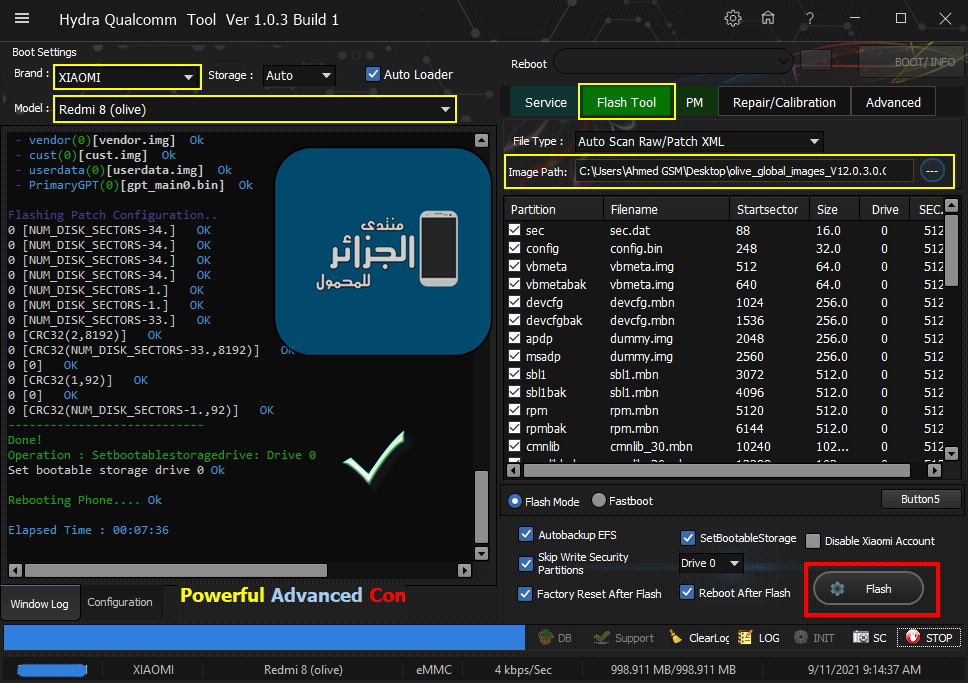
[B][FONT=Arial Black][SIZE=2] Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM5)
SymbolicName :\??\USB#VID_05C6&PID_9008#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :07/02/2015,2.00.05.00
Getting device info..Ok
Device MODE : Firehose
Connecting to Firehose...
Ping.. Ok
Configuration......
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8937
Version : 1
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 144
Serial Number : 2800291281
Firmware Version : 162
Product Name : HCG8a4
Physical Partitions : 3
Total Logical Blocks:
Drive [0] 122142720[58.242 GB]
Drive [1] 8192[4 MB]
Drive [2] 8192[4 MB]
Protocol : Universal
Running : Ok
Phone Information......
Brand : Xiaomi
Vendor : Xiaomi
Model : Redmi 8
ID : PKQ1.190319.001
SDK : 28
Release : 9
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-GB
Description : olive-user 9 PKQ1.190319.001 V11.0.11.0.PCNMIXM release-keys
Miui Ver : V11
Device : olive
Mod_device : olive_global
Display ID : ZQL2115-olive-build-20200519032343
Security Patch : 2020-05-01
Emmc_size : 16GB
Fingerprint : Xiaomi/olive/olive:9/PKQ1.190319.001/V11.0.11.0.PCNMIXM:user/release-keys
Reading GPT[3]
Drive [0] 64 Items
Drive [1] 0 Items
Drive [2] 0 Items
Backup Security partitions...
Reading Security Items....
> modemst1
> modemst2
> fsg
> fsc
C:\Hydra Tool\Backup\Security_Backup\Redmi 8__9_Security_091121090706.sec
Backup Security Success....
----------------------------
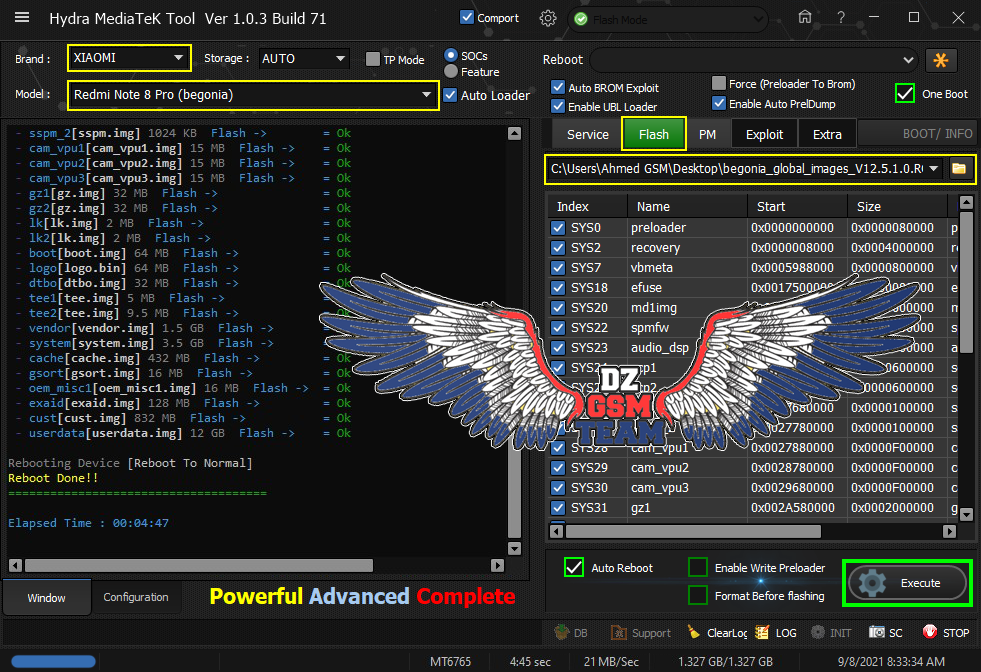
Flashing Selected Partitions....
- sec(0)[sec.dat] Skipped
- config(0)[config.bin] Ok
- vbmeta(0)[vbmeta.img] Ok
- vbmetabak(0)[vbmeta.img] Ok
- devcfg(0)[devcfg.mbn] Ok
- devcfgbak(0)[devcfg.mbn] Ok
- apdp(0)[dummy.img] Ok
- msadp(0)[dummy.img] Ok
- sbl1(0)[sbl1.mbn] Ok
- sbl1bak(0)[sbl1.mbn] Ok
- rpm(0)[rpm.mbn] Ok
- rpmbak(0)[rpm.mbn] Ok
- cmnlib(0)[cmnlib_30.mbn] Ok
- cmnlibbak(0)[cmnlib_30.mbn] Ok
- cmnlib64(0)[cmnlib64_30.mbn] Ok
- cmnlib64bak(0)[cmnlib64_30.mbn] Ok
- keymaster(0)[km4.mbn] Ok
- keymasterbak(0)[km4.mbn] Ok
- misc(0)[misc.img] Ok
- aboot(0)[emmc_appsboot.mbn] Ok
- abootbak(0)[emmc_appsboot.mbn] Ok
- tz(0)[tz.mbn] Ok
- tzbak(0)[tz.mbn] Ok
- dtbo(0)[dtbo.img] Ok
- dtbobak(0)[dtbo.img] Ok
- splash(0)[splash.img] Ok
- dsp(0)[adspso.bin] Ok
- dspbak(0)[adspso.bin] Ok
- persist(0)[persist.img] Ok
- mdtp(0)[mdtp.img] Ok
- mdtpbak(0)[mdtp.img] Ok
- boot(0)[boot.img] Ok
- recovery(0)[recovery.img] Ok
- cache(0)[cache.img] Ok
- modem(0)[NON-HLOS.bin] Ok
- system(0)[system.img] Ok
- vendor(0)[vendor.img] Ok
- cust(0)[cust.img] Ok
- userdata(0)[userdata.img] Ok
- PrimaryGPT(0)[gpt_main0.bin] Ok
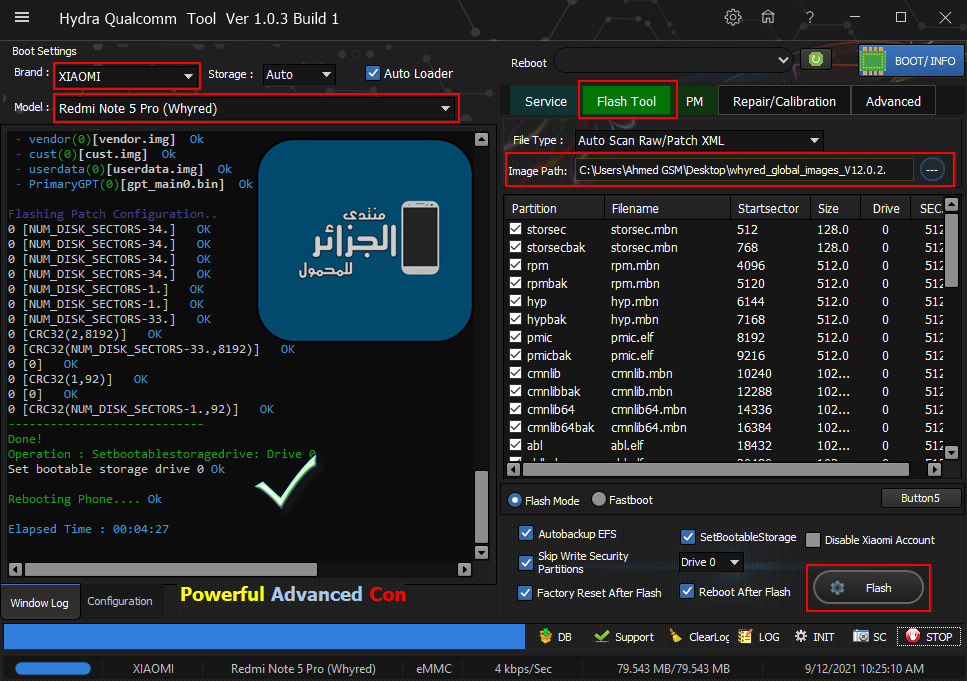
Flashing Patch Configuration..
0 [NUM_DISK_SECTORS-34.] OK
0 [NUM_DISK_SECTORS-34.] OK
0 [NUM_DISK_SECTORS-34.] OK
0 [NUM_DISK_SECTORS-34.] OK
0 [NUM_DISK_SECTORS-1.] OK
0 [NUM_DISK_SECTORS-1.] OK
0 [NUM_DISK_SECTORS-33.] OK
0 [CRC32(2,8192)] OK
0 [CRC32(NUM_DISK_SECTORS-33.,8192)] OK
0 [0] OK
0 [CRC32(1,92)] OK
0 [0] OK
0 [CRC32(NUM_DISK_SECTORS-1.,92)] OK
----------------------------
Done!
Operation : Setbootablestoragedrive: Drive 0
Set bootable storage drive 0 Ok
Rebooting Phone.... Ok
Elapsed Time : 00:07:36
[/SIZE][/FONT][/B]