رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Condor P8 lite (PGN610) Rebuild Userdata Done
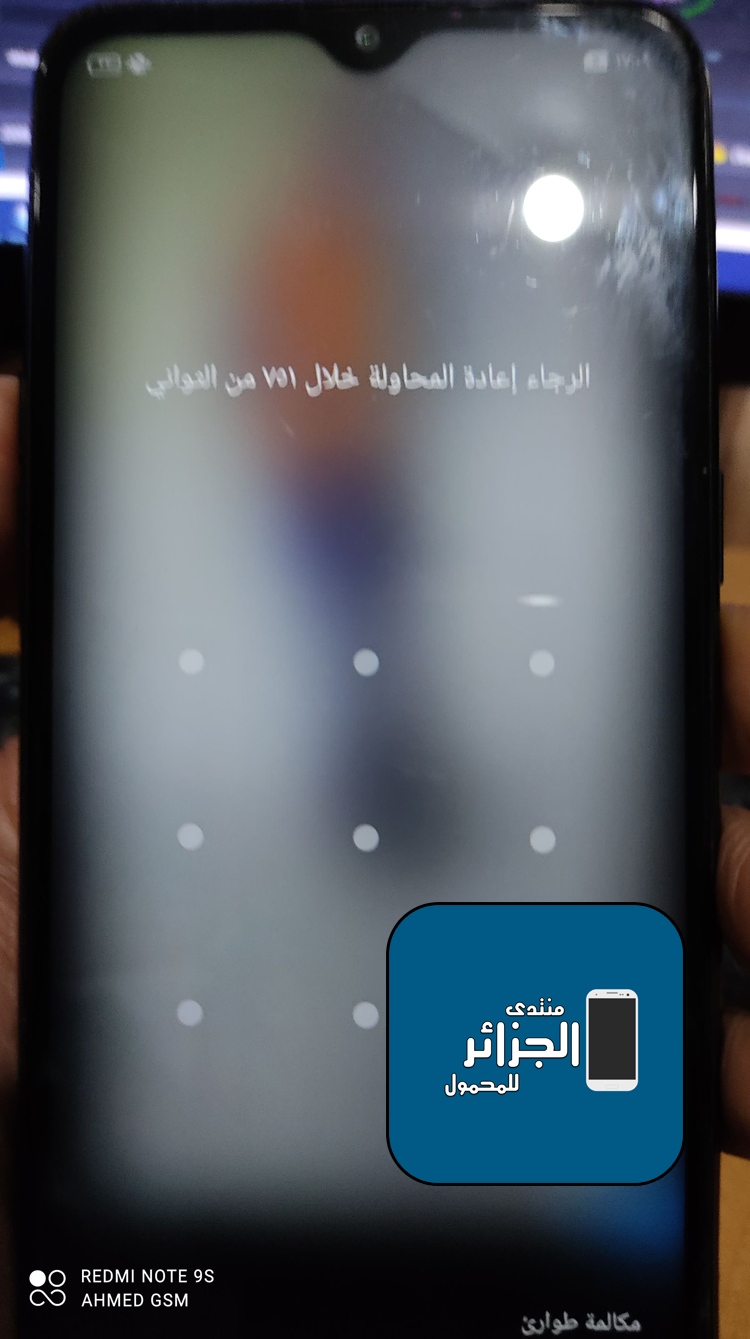
الهاتف يدخل لمود ريكوفري (Recovery Mode) ثم يعيد التشغيل
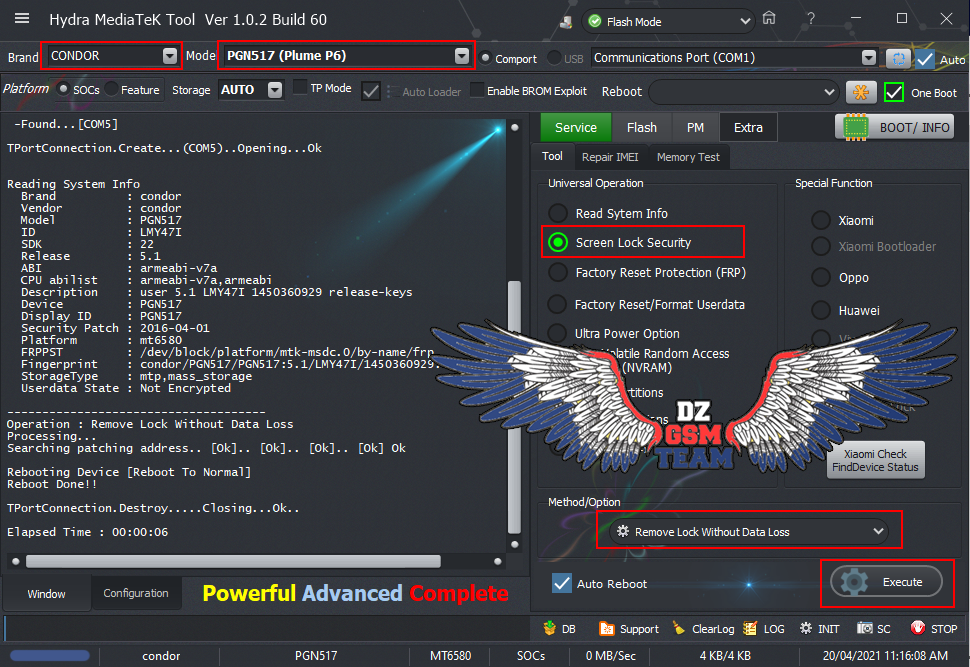
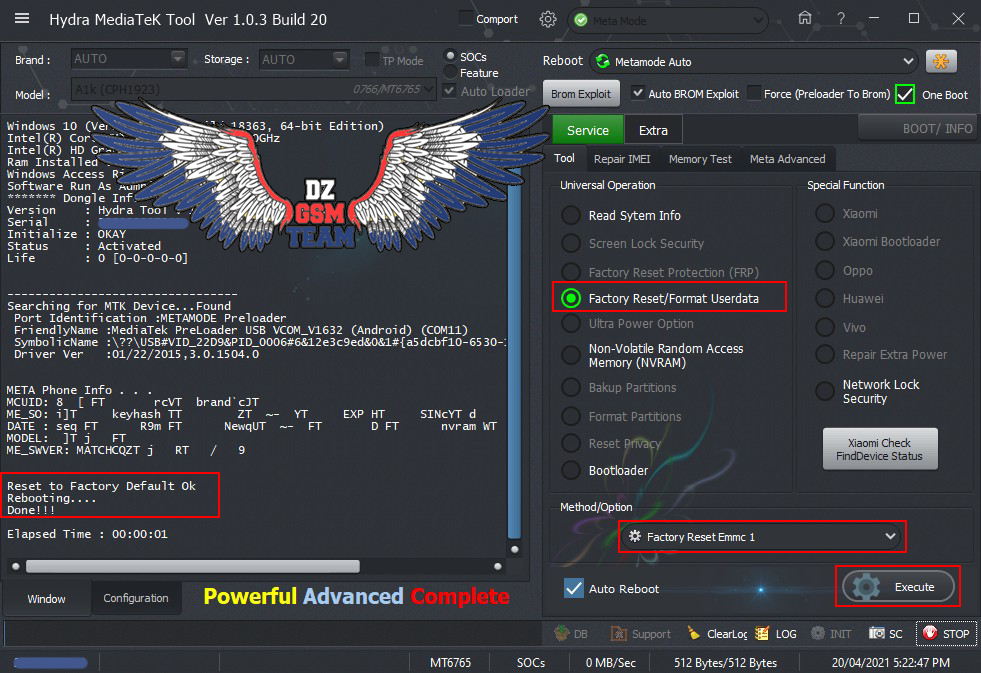
تم الحل باستعمال خاصية Rebuild Userdata
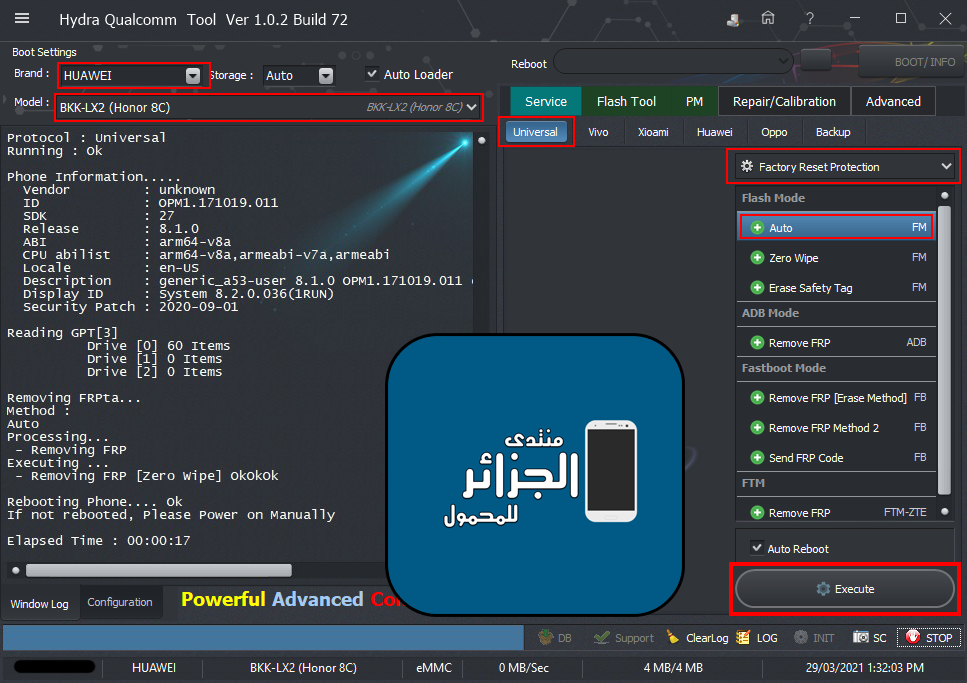
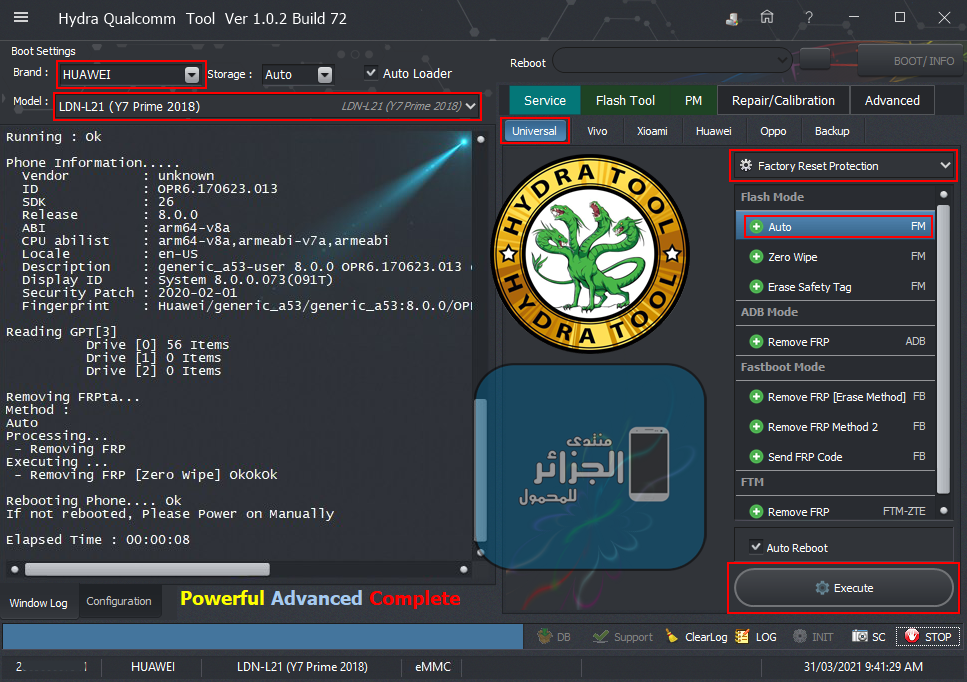
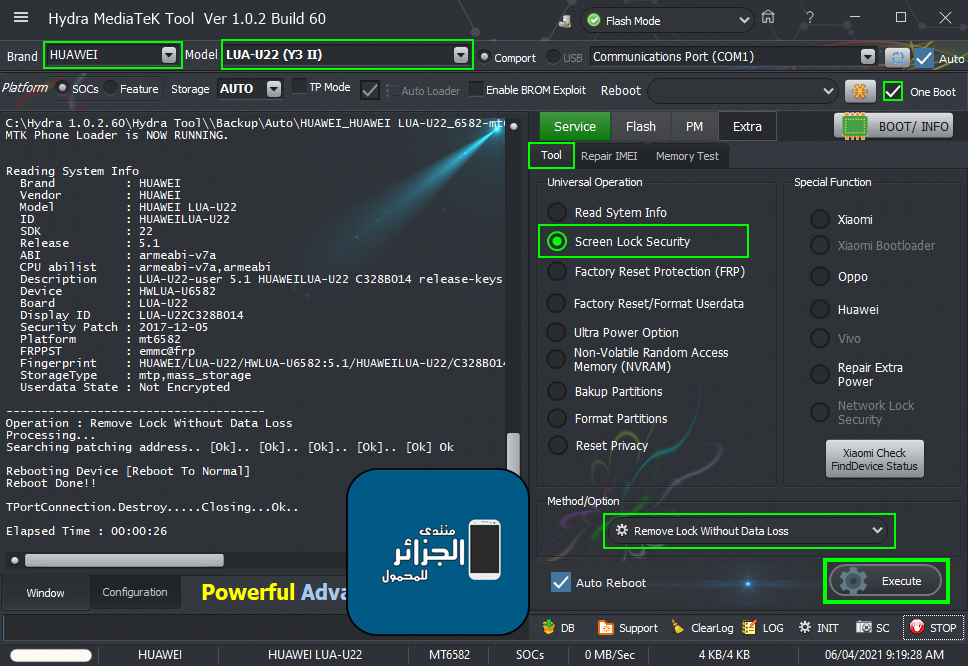
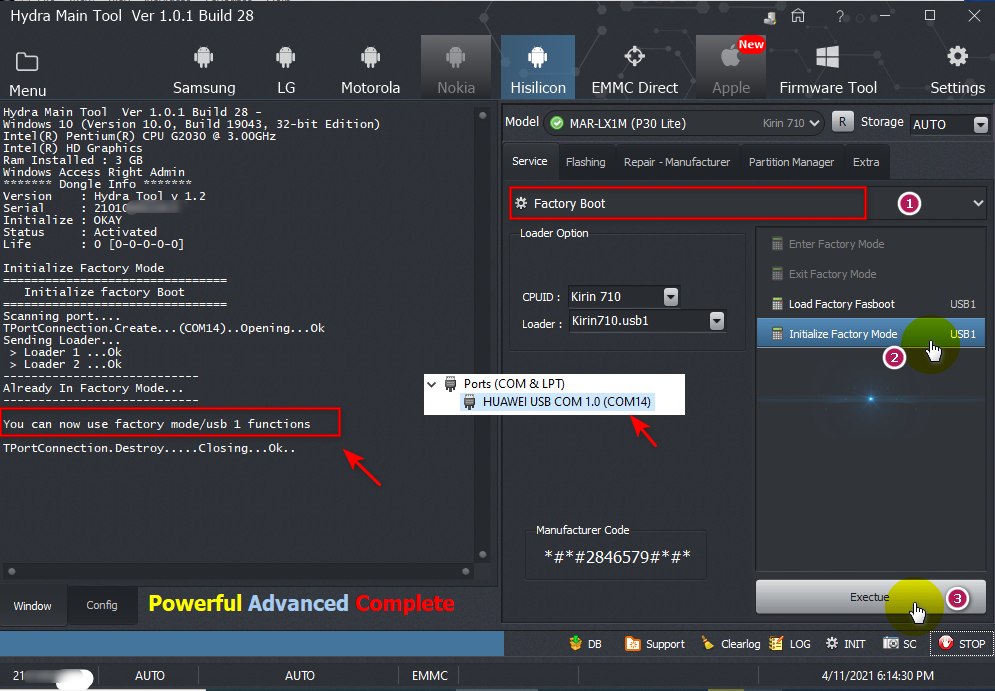
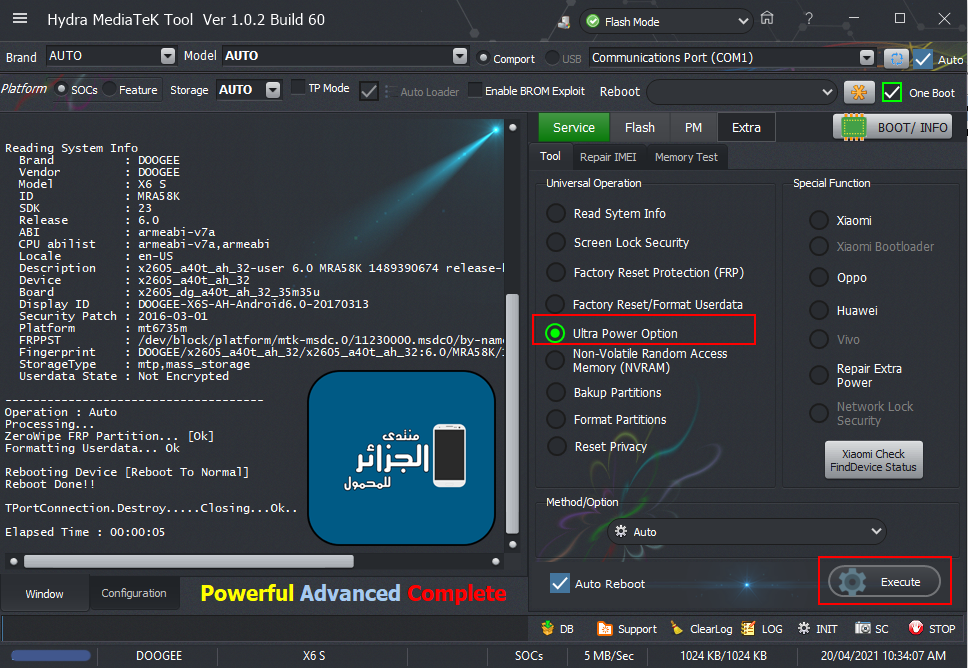
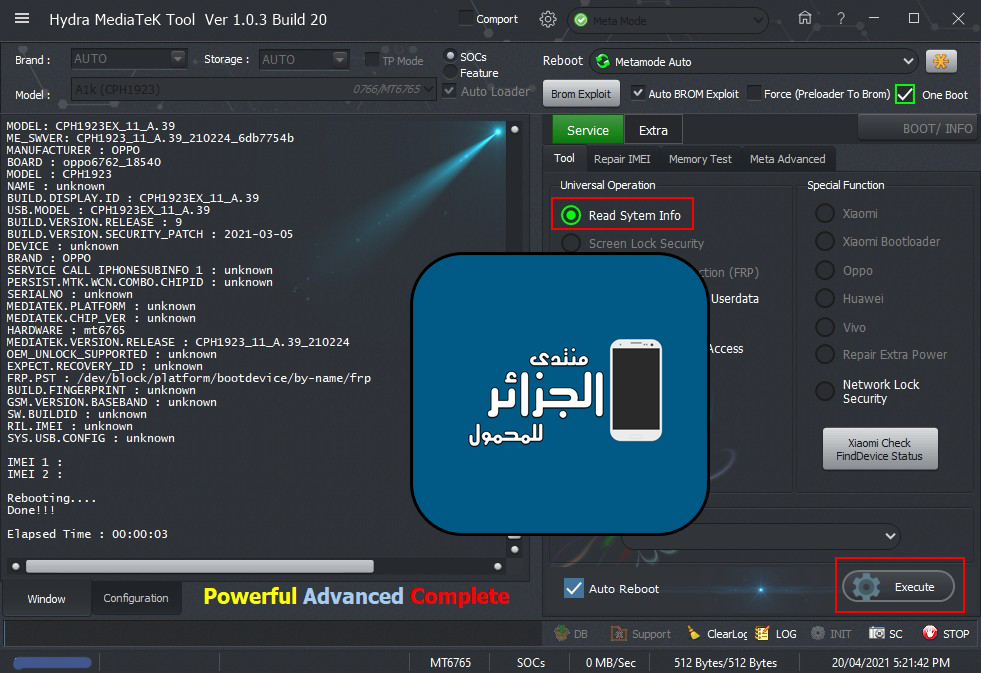
اولا بوت انفو BOOT INFO على الهايدرا
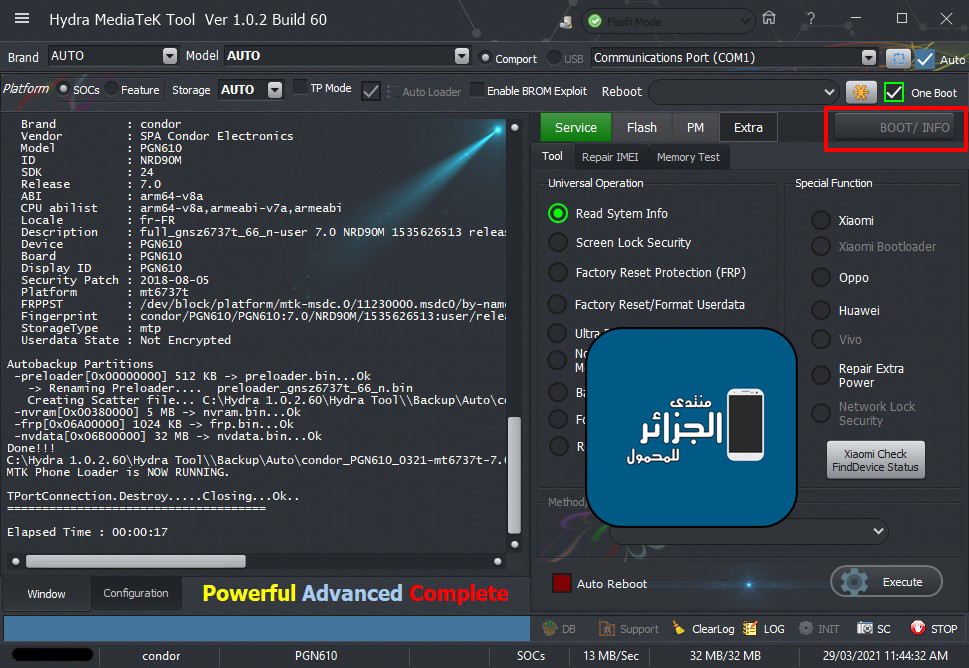
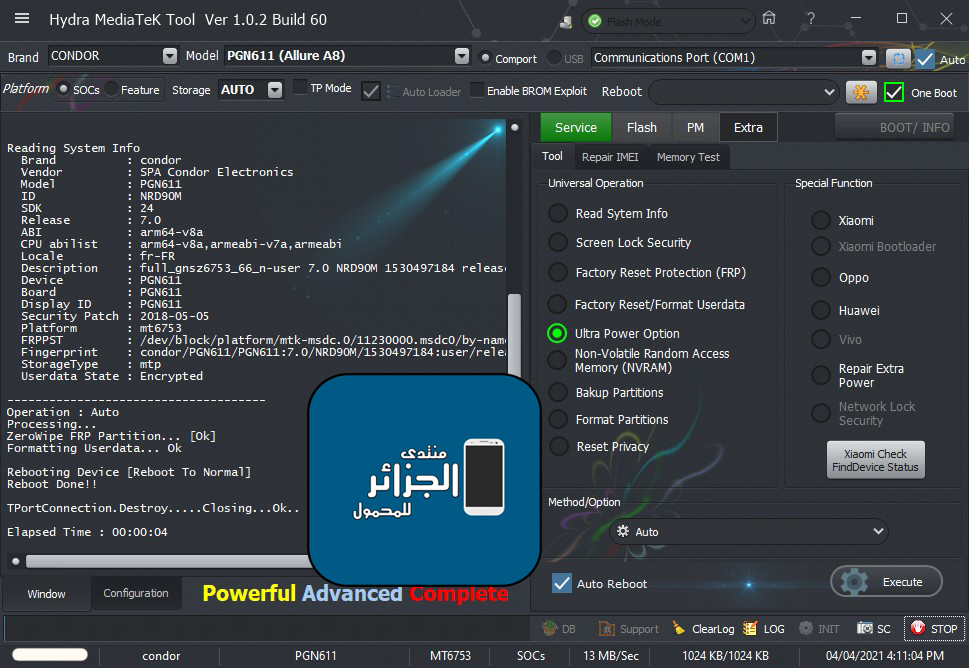
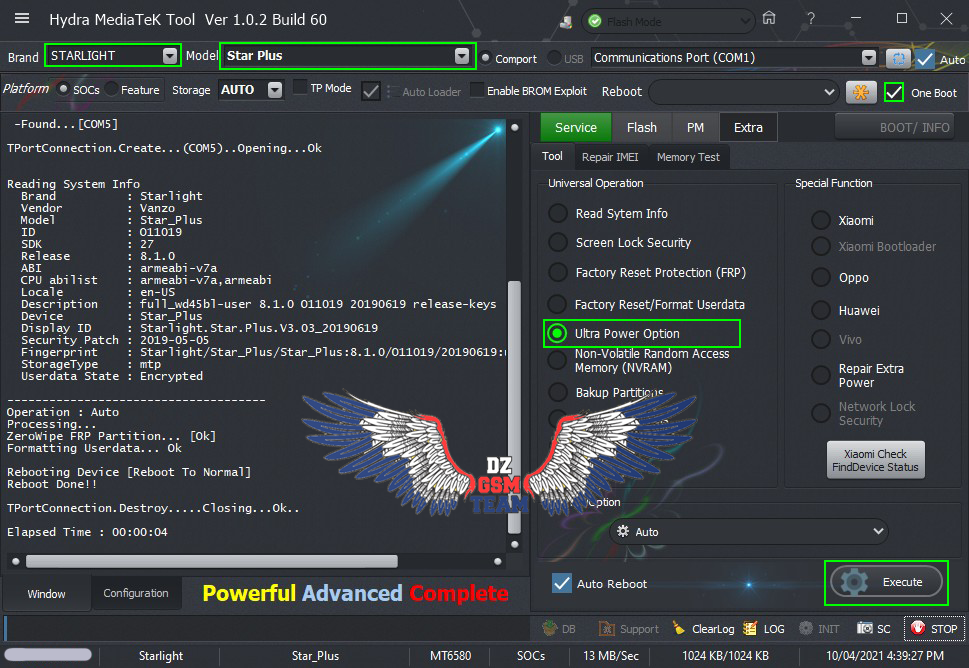
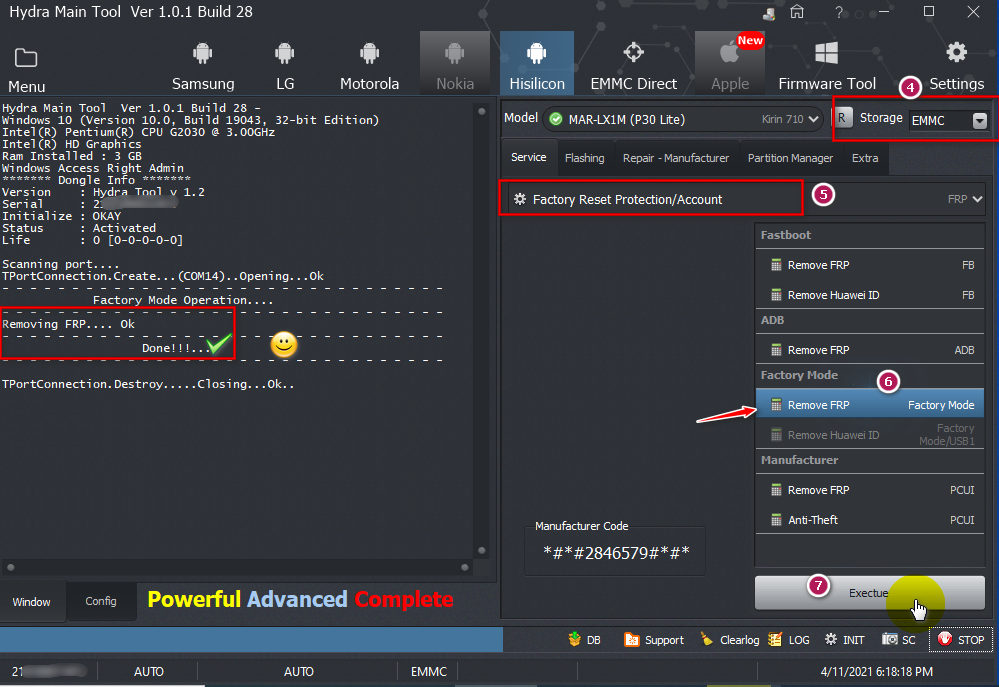
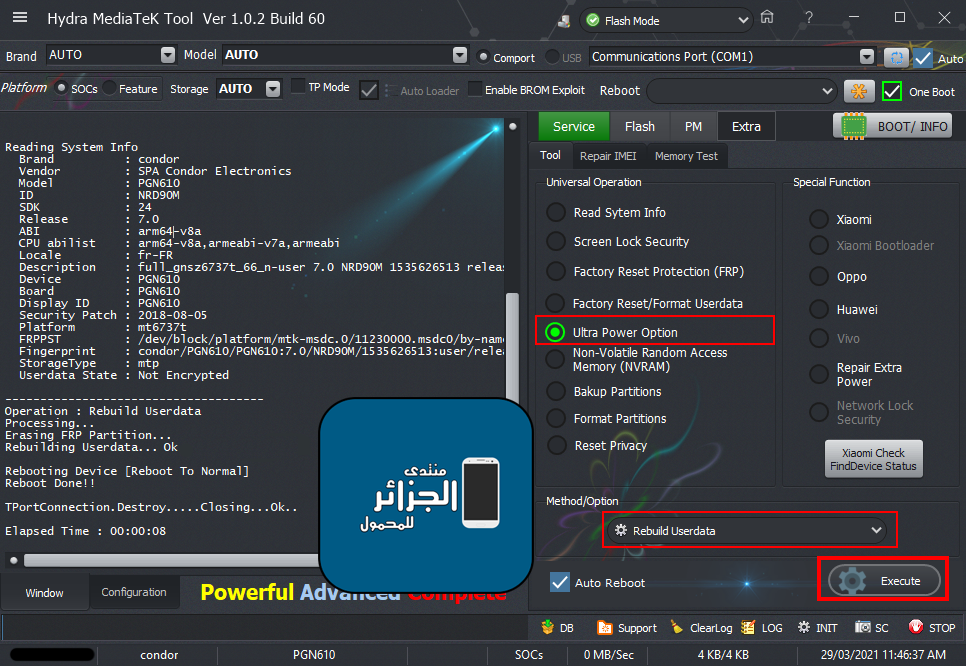
ترك الهاتف متصل بالكابل والذهاب لخاصية Ulta Power Option ثم Rebuild Userdata
Condor P8 lite (PGN610) Rebuild Userdata Done
الهاتف يدخل لمود ريكوفري (Recovery Mode) ثم يعيد التشغيل
تم الحل باستعمال خاصية Rebuild Userdata
اولا بوت انفو BOOT INFO على الهايدرا

كود:
[B][FONT=Arial][SIZE=2]Brand : AUTO Model : AUTO Connection : Flash Mode
=====================================
How To Boot : Power off phone
* BROM Mode : Press VOL +
* Preloader Mode : Just Insert cable
Connection
-Please wait...
-Found...
-PreLoader...[COM4]
TPortConnection.Create...(COM4)..Opening...Ok
Handshaking...Ok
Identifying Hardware ID.....
BROM CPUID : 0321 (0000)MT6737T[6735]
BROM HW_SW_VER : 8A00 CA00 0000 0000
Handshaking...
Identifying Hardware ID.....
BROM CPUID : 0321 (0000)MT6737T[6735]
BROM HW_SW_VER : 8A00 CA00 0000 0000
FUSEID : 00000000
FUSEID : 00000000
SECURE VERSION : 00
BL VERSION : 00
BR Secured : 00
NORMAL BOOT
Preparing Download Agent..
DA : 6735.bin
Agent: MTK_DOWNLOAD_AGENT -HYDRA
Ver : MTK_AllInOne_DA_v3.3001.2018-09-18.13:22_452898
Init : Loader [1]
Sending : Accepted
Identifying Protocol...
Protocol : Old - eMMC
00000000000000000000
PRMMCCID : 520001154D423145CACD0742C336D9F0
Init Configuration
Running DA 4.2 on BBID : 0x9B Ok
Initializing Loader [2]
Sending Loader [2] Accepted
Reading Flashchip data....
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x00000003A3E00000 -14,561 GB
ERAM Size : 0x00000000C0000000 -3 GB
IRAM Size : 0x0000000000020000 -128 KB
UNICAL RID : 84B0C3BBB637173870B889E5117B9A56
eMMC CID : 520001154D423145CACD0742C3C3D9F0
Change to HIGH SPEED...
5A
Connection
-Please wait...
-Found...[COM5]
Reading Partition Table
SIZE[0x000007E8] 23 Items > Done
Reading System Info
Brand : condor
Vendor : SPA Condor Electronics
Model : PGN610
ID : NRD90M
SDK : 24
Release : 7.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : fr-FR
Description : full_gnsz6737t_66_n-user 7.0 NRD90M 1535626513 release-keys
Device : PGN610
Board : PGN610
Display ID : PGN610
Security Patch : 2018-08-05
Platform : mt6737t
FRPPST : /dev/block/platform/mtk-msdc.0/11230000.msdc0/by-name/frp
Fingerprint : condor/PGN610/PGN610:7.0/NRD90M/1535626513:user/release-keys
StorageType : mtp
Userdata State : Not Encrypted
Autobackup Partitions
-preloader[0x00000000] 512 KB -> preloader.bin...Ok
-> Renaming Preloader.... preloader_gnsz6737t_66_n.bin
Creating Scatter file... C:\Hydra 1.0.2.60\Hydra Tool\\Backup\Auto\condor_PGN610_0321-mt6737t-7.0_PGN610_290321120129\MT6737T_Android_scatter.txt
-nvram[0x00380000] 5 MB -> nvram.bin...Ok
-frp[0x06A00000] 1024 KB -> frp.bin...Ok
-nvdata[0x06B00000] 32 MB -> nvdata.bin...Ok
Done!!!
C:\Hydra 1.0.2.60\Hydra Tool\\Backup\Auto\condor_PGN610_0321-mt6737t-7.0_PGN610_290321120129
MTK Phone Loader is NOW RUNNING.
TPortConnection.Destroy.....Closing...Ok..
=====================================
Elapsed Time : 00:00:17
[/SIZE][/FONT][/B]ترك الهاتف متصل بالكابل والذهاب لخاصية Ulta Power Option ثم Rebuild Userdata

كود:
[B][FONT=Arial Black][SIZE=2]Brand : AUTO Model : AUTO Connection : Flash Mode
=====================================
Connection
-Please wait...
-Found...[COM5]
TPortConnection.Create...(COM5)..Opening...Ok
Reading System Info
Brand : condor
Vendor : SPA Condor Electronics
Model : PGN610
ID : NRD90M
SDK : 24
Release : 7.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : fr-FR
Description : full_gnsz6737t_66_n-user 7.0 NRD90M 1535626513 release-keys
Device : PGN610
Board : PGN610
Display ID : PGN610
Security Patch : 2018-08-05
Platform : mt6737t
FRPPST : /dev/block/platform/mtk-msdc.0/11230000.msdc0/by-name/frp
Fingerprint : condor/PGN610/PGN610:7.0/NRD90M/1535626513:user/release-keys
StorageType : mtp
Userdata State : Not Encrypted
-------------------------------------
[COLOR="#FF0000"]Operation : Rebuild Userdata
Processing...
Erasing FRP Partition...
Rebuilding Userdata... Ok
[/COLOR]
Rebooting Device [Reboot To Normal]
Reboot Done!!
TPortConnection.Destroy.....Closing...Ok..
Elapsed Time : 00:00:08
[/SIZE][/FONT][/B]