- إنضم
- 16 سبتمبر 2012
- المشاركات
- 3,136
- مستوى التفاعل
- 2,975
- النقاط
- 113
كود:
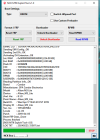
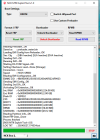
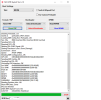
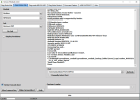
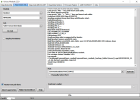
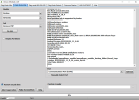
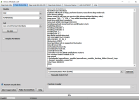
[Reset FRP]
Waiting for device...Found
Port Info : MediaTek USB Port_V1633 (COM46) [\\?\usb#vid_0e8d&pid_0003#5&21e739f&0&3#{86e0d1e0-8089-11d0-9ce4-08003e301f73}]
: MediaTek Inc., 3.0.1504.0 [usb2ser.sys]
: BROM PORT
Hw ID : MT6765 [0766] Helio P35/G35
Details : 8A00,CA00,0000
Sec. Cfg : [SBA Active] [SLA Inactive] [DAA Active]
MEID : 767256725AE2F5C806BB26BE0E6A192A
SoC ID[0] : EFF20E08AAF1051AE246A877B0A772BC
SoC ID[1] : 97EA2B3CABE3E5B92A0E73EE5480368A
Executing Exploit...Done
Reading Preloader...OK
Saved as : preloader_k62v1_64_bsp.bin
Loading EMI Config from Preloader...OK
Sec. Cfg : [SBA Inactive] [SLA Inactive] [DAA Inactive]
Sending DA1...OK
Running DA1...OK
Waiting DA SYNC Signal...OK
Setting Checksum Level...Done [Storage]
Connection : brom
Speed : HIGH-SPEED
Reading EMI Configuration...OK
EMMC CID : 150100474436424D4201F016CE4D2519
Sending EMI Config...OK
Sending 2nd DA...OK
Activating DA Extension...OK
Int. RAM : 0x0000000000038000 [224.00 KB]
Ext. RAM : 0x00000000C0000000 [3.00 GB]
Flash ID : GD6BMB
CID : 150100474436424D4201F016CE4D2519
BOOT1 : 0x0000000000400000 [4.00 MB]
BOOT2 : 0x0000000000400000 [4.00 MB]
RPMB : 0x0000000000400000 [4.00 MB]
USERAREA : 0x0000000747C00000 [29.12 GB]
Reading Parititon Info...OK
Brand : Condor
Manufacturer : SPA Condor Electronics
Model : Allure M3 Lite
Device : Allure_M3_Lite
And. Ver. : 8.1.0
Prod. Name : Allure_M3_Lite
Build Dt. : Wed Apr 17 18:41:20 CST 2019
Display ID : Allure_M3_Lite
Ver. Inc. : 1555497684
Locale : en-US
Patch : 2019-04-05
Reset FRP Data...Done
Process finished
[NCK MTK Exploit Tool v1.0]
LOG TXT : 20240225_155611.txt